Copyright © 2015 Bert N. Langford (Images may be subject to copyright. Please send feedback)
Welcome to Our Generation USA!
Covers all activities of
The United States Military,
as well as the CIA, Department of Defense, Department of Homeland Security; memorials, cemeteries, medals and other awards, veteran affairs including medical care (e.g. PTSD), future job training, recruiting, retirement, major wars including war on terrorism, and more.
See Also "Greatest Americans"
Military including the United States Armed Forces
YouTube Musical Video: United States Military Tribute - - "My Sacrifice" by Creed
Pictured: LEFT to RIGHT: US B-2 Spirit bomber; Statue of Liberty with Air Force Jets Fly-over; United States Military Academy at West Point
Military in General:
The military, also called the armed forces, are forces authorized to use deadly force, and weapons, to support the interests of the state and some or all of its citizens. The task of the military is usually defined as defense of the state and its citizens, and the prosecution of war against another state.
The military may also have additional sanctioned and non-sanctioned functions within a society, including,
The military can also function as a discrete subculture within a larger civil society, through the development of separate infrastructures, which may include housing, schools, utilities, food production and banking.
The United States Armed Forces:
The federal armed forces of the United States consist of the Army, Marine Corps, Navy, Air Force, and Coast Guard.
The President of the United States is the military's overall head, and helps form military policy with the U.S. Department of Defense (DoD), a federal executive department, acting as the principal organ by which military policy is carried out.
From the time of its inception, the military played a decisive role in the history of the United States. A sense of national unity and identity was forged as a result of victory in the First Barbary War and the Second Barbary War.
Even so, the Founders were suspicious of a permanent military force. It played an important role in the American Civil War, where leading generals on both sides were picked from members of the United States military.
Not until the outbreak of World War II did a large standing army become officially established. The National Security Act of 1947, adopted following World War II and during the Cold War's onset, created the modern U.S. military framework; the Act merged previously Cabinet-level Department of War and the Department of the Navy into the National Military Establishment (renamed the Department of Defense in 1949), headed by the Secretary of Defense; and created the Department of the Air Force and National Security Council.
The U.S. military is one of the largest militaries in terms of number of personnel. It draws its personnel from a large pool of paid volunteers; although conscription has been used in the past in various times of both war and peace, it has not been used since 1972.
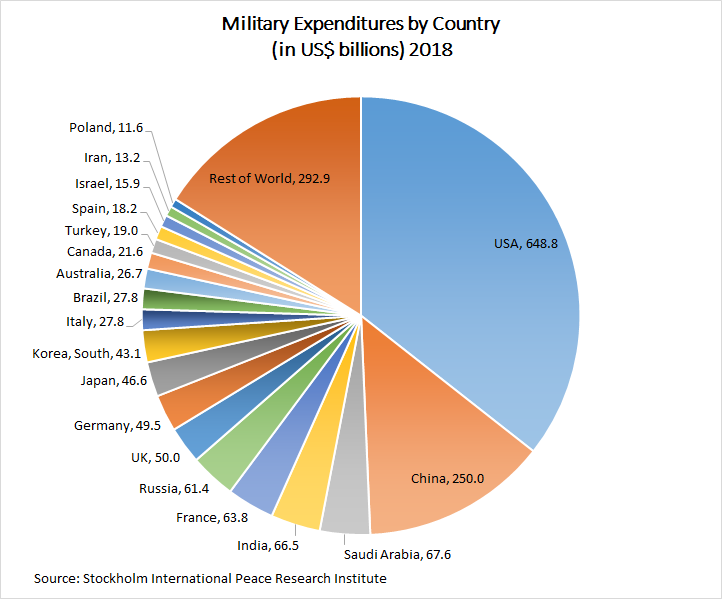
As of 2016, the United States spends about $580.3 billion annually to fund its military forces and Overseas Contingency Operations.
Put together, the United States constitutes roughly 39 percent of the world's military expenditures. For the period 2010–14, the Stockholm International Peace Research Institute (SIPRI) found that the United States was the world's largest exporter of major arms, accounting for 31 per cent of global shares.
The United States was also the world's eighth largest importer of major weapons for the same period. The U.S. Armed Forces has significant capabilities in both defense and power projection due to its large budget, resulting in advanced and powerful equipment, and its widespread deployment of force around the world, including about 800 military bases in foreign locations.
For Further Amplification, click on any of the following hyperlinks:
The military, also called the armed forces, are forces authorized to use deadly force, and weapons, to support the interests of the state and some or all of its citizens. The task of the military is usually defined as defense of the state and its citizens, and the prosecution of war against another state.
The military may also have additional sanctioned and non-sanctioned functions within a society, including,
- the promotion of a political agenda,
- protecting corporate economic interests,
- internal population control,
- construction,
- emergency services,
- social ceremonies,
- and guarding important areas.
The military can also function as a discrete subculture within a larger civil society, through the development of separate infrastructures, which may include housing, schools, utilities, food production and banking.
The United States Armed Forces:
The federal armed forces of the United States consist of the Army, Marine Corps, Navy, Air Force, and Coast Guard.
The President of the United States is the military's overall head, and helps form military policy with the U.S. Department of Defense (DoD), a federal executive department, acting as the principal organ by which military policy is carried out.
From the time of its inception, the military played a decisive role in the history of the United States. A sense of national unity and identity was forged as a result of victory in the First Barbary War and the Second Barbary War.
Even so, the Founders were suspicious of a permanent military force. It played an important role in the American Civil War, where leading generals on both sides were picked from members of the United States military.
Not until the outbreak of World War II did a large standing army become officially established. The National Security Act of 1947, adopted following World War II and during the Cold War's onset, created the modern U.S. military framework; the Act merged previously Cabinet-level Department of War and the Department of the Navy into the National Military Establishment (renamed the Department of Defense in 1949), headed by the Secretary of Defense; and created the Department of the Air Force and National Security Council.
The U.S. military is one of the largest militaries in terms of number of personnel. It draws its personnel from a large pool of paid volunteers; although conscription has been used in the past in various times of both war and peace, it has not been used since 1972.
As of 2016, the United States spends about $580.3 billion annually to fund its military forces and Overseas Contingency Operations.
Put together, the United States constitutes roughly 39 percent of the world's military expenditures. For the period 2010–14, the Stockholm International Peace Research Institute (SIPRI) found that the United States was the world's largest exporter of major arms, accounting for 31 per cent of global shares.
The United States was also the world's eighth largest importer of major weapons for the same period. The U.S. Armed Forces has significant capabilities in both defense and power projection due to its large budget, resulting in advanced and powerful equipment, and its widespread deployment of force around the world, including about 800 military bases in foreign locations.
For Further Amplification, click on any of the following hyperlinks:
- History
- Command structure
- Budget
- Personnel
- Order of precedence
- See also:
- Awards and decorations of the United States military
- Full-spectrum dominance
- List of active United States military aircraft
- List of currently active United States military land vehicles
- List of currently active United States military watercraft
- Military expression
- Military justice
- National Guard
- Public opinion of the military
- Servicemembers' Group Life Insurance
- Sexual orientation and gender identity in the United States military
- State Defense Force
- TRICARE – Health care plan for the U.S. uniformed services
- United States military casualties of war
- United States military veteran suicide
- United States Service academies
- Women in the United States Army
- Women in the United States Marines
- Women in the United States Navy
- Women in the United States Air Force
- Women in the United States Coast Guard
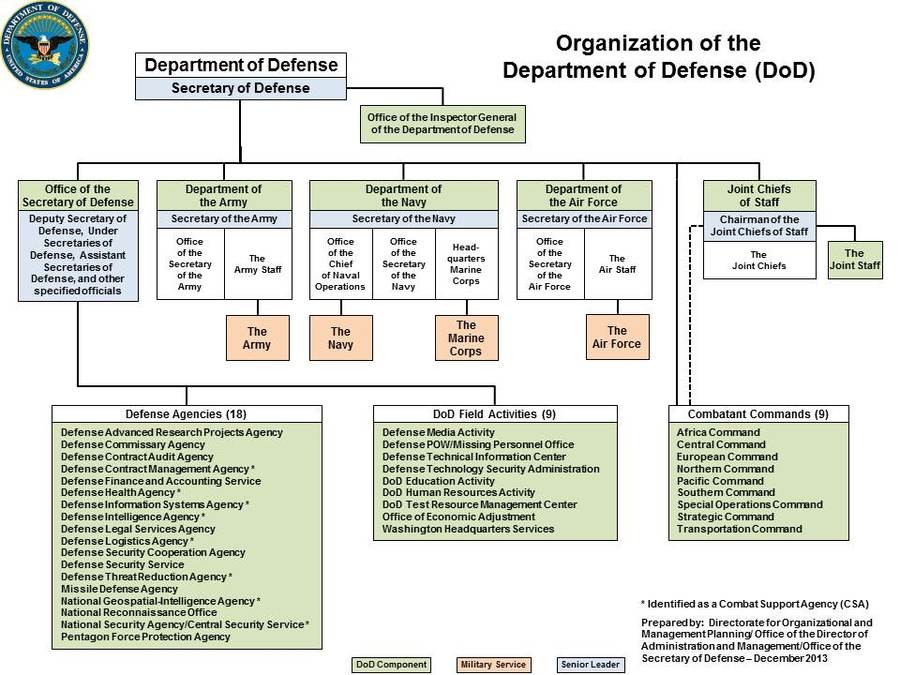
United States Department of Defense,
Pictured: Organizational Chart for the US. Department of Defense
- including U.S Central Command;
- as well as a List of the Major U.S. Defense Contractors.
Pictured: Organizational Chart for the US. Department of Defense
Click here for a list of Defense Contractors serving the United States Defense Department.
The Department of Defense (DoD) is an executive branch department of the federal government of the United States charged with coordinating and supervising all agencies and functions of the government concerned directly with national security and the United States Armed Forces.
The department is the largest employer in the world, with nearly 1.3 million active duty servicemen and women as of 2016. Adding to its employees are over 826,000 National Guardsmen and Reservists from the four services, and over 742,000 civilians bringing the total to over 2.8 million employees.
Headquartered at the Pentagon in Arlington, Virginia, just outside Washington, D.C., the DoD's stated mission is ...to provide a lethal Joint Force to defend the security of our country and sustain American influence abroad.
The Department of Defense is headed by the Secretary of Defense, a cabinet-level head who reports directly to the President of the United States.
Beneath the Department of Defense are three subordinate military departments:
In addition, four national intelligence services are subordinate to the Department of Defense:
Other Defense Agencies include:
All of the above are under the command of the Secretary of Defense. Military operations are managed by ten regional or functional Unified combatant commands.
The Department of Defense also operates several joint services schools, including the National Defense University (NDU) and the National War College (NWC).
Click on any of the following blue hyperlinks for more about the United States Department of Defense:
U.S Central Command
The United States Central Command (USCENTCOM or CENTCOM) is a theater-level Unified Combatant Command of the U.S. Department of Defense. It was established in 1983, taking over the 1980 Rapid Deployment Joint Task Force (RDJTF) responsibilities.
The CENTCOM Area of Responsibility (AOR) includes countries in the West Asia, parts of North Africa, and Central Asia, most notably Afghanistan and Iraq. CENTCOM has been the main American presence in many military operations, including the Persian Gulf War (Operation Desert Storm, 1991), the War in Afghanistan (Operation Enduring Freedom, 2001–2014), and the Iraq War (Operation Iraqi Freedom, 2003–2011).
As of 2015, CENTCOM forces are deployed primarily in Afghanistan (Operation Resolute Support, 2015–present), Iraq and Syria (Operation Inherent Resolve, 2014–present) in supporting and advise-and-assist roles.
As of 1 September 2016, CENTCOM's commander was General Joseph Votel, U.S. Army.
Of all six American regional unified combatant commands, CENTCOM is among the three with headquarters outside its area of operations (the other two being USAFRICOM and USSOUTHCOM).
CENTCOM's main headquarters is located at MacDill Air Force Base, in Tampa, Florida. A forward headquarters was established in 2002 at Camp As Sayliyah in Doha, Qatar, which in 2009 transitioned to a forward headquarters at Al Udeid Air Base in Qatar.
The United States Central Command (USCENTCOM or CENTCOM) is a theater-level Unified Combatant Command of the U.S. Department of Defense. It was established in 1983, taking over the 1980 Rapid Deployment Joint Task Force (RDJTF) responsibilities.
The CENTCOM Area of Responsibility (AOR) includes countries in the West Asia, parts of North Africa, and Central Asia, most notably Afghanistan and Iraq.
CENTCOM has been the main American presence in many military operations, including :
As of 2015, CENTCOM forces are deployed primarily in Afghanistan (Operation Resolute Support, 2015–present), Iraq and Syria (Operation Inherent Resolve, 2014–present) in supporting and advise-and-assist roles.
As of 1 September 2016, CENTCOM's commander was General Joseph Votel, U.S. Army.
Of all six American regional unified combatant commands, CENTCOM is among the three with headquarters outside its area of operations (the other two being USAFRICOM and USSOUTHCOM).
CENTCOM's main headquarters is located at MacDill Air Force Base, in Tampa, Florida. A forward headquarters was established in 2002 at Camp As Sayliyah in Doha, Qatar, which in 2009 transitioned to a forward headquarters at Al Udeid Air Base in Qatar.
Click on any of the following blue hyperlinks for more about the United States Central Command:
The Department of Defense (DoD) is an executive branch department of the federal government of the United States charged with coordinating and supervising all agencies and functions of the government concerned directly with national security and the United States Armed Forces.
The department is the largest employer in the world, with nearly 1.3 million active duty servicemen and women as of 2016. Adding to its employees are over 826,000 National Guardsmen and Reservists from the four services, and over 742,000 civilians bringing the total to over 2.8 million employees.
Headquartered at the Pentagon in Arlington, Virginia, just outside Washington, D.C., the DoD's stated mission is ...to provide a lethal Joint Force to defend the security of our country and sustain American influence abroad.
The Department of Defense is headed by the Secretary of Defense, a cabinet-level head who reports directly to the President of the United States.
Beneath the Department of Defense are three subordinate military departments:
- the United States Department of the Army,
- the United States Department of the Navy,
- and the United States Department of the Air Force.
In addition, four national intelligence services are subordinate to the Department of Defense:
- the Defense Intelligence Agency (DIA),
- the National Security Agency (NSA),
- the National Geospatial-Intelligence Agency (NGA),
- and the National Reconnaissance Office (NRO).
Other Defense Agencies include:
- the Defense Advanced Research Projects Agency (DARPA),
- the Defense Logistics Agency (DLA),
- the Missile Defense Agency (MDA),
- the Defense Health Agency (DHA),
- Defense Threat Reduction Agency (DTRA),
- the Defense Security Service (DSS),
- and the Pentagon Force Protection Agency (PFPA),
All of the above are under the command of the Secretary of Defense. Military operations are managed by ten regional or functional Unified combatant commands.
The Department of Defense also operates several joint services schools, including the National Defense University (NDU) and the National War College (NWC).
Click on any of the following blue hyperlinks for more about the United States Department of Defense:
- History
- Organizational structure
- Budget
- Criticism
- Energy use
- Freedom of Information Act processing performance
- Related legislation
- See also:
- Official website
- Department of Defense in the Federal Register
- Office of the Under Secretary of Defense (Comptroller) Budget and Financial Management Policy
- Department of Defense IA Policy Chart
- Works by United States Department of Defense at Project Gutenberg
- Works by or about United States Department of Defense at Internet Archive
- Department of Defense Collection on the Internet Archive
- Arms industry
- List of United States military bases
- Military–industrial complex
- Nuclear weapons
- Private military company
- Title 32 of the Code of Federal Regulations
- Warrior Games
- JADE (planning system)
- Global Command and Control System
U.S Central Command
The United States Central Command (USCENTCOM or CENTCOM) is a theater-level Unified Combatant Command of the U.S. Department of Defense. It was established in 1983, taking over the 1980 Rapid Deployment Joint Task Force (RDJTF) responsibilities.
The CENTCOM Area of Responsibility (AOR) includes countries in the West Asia, parts of North Africa, and Central Asia, most notably Afghanistan and Iraq. CENTCOM has been the main American presence in many military operations, including the Persian Gulf War (Operation Desert Storm, 1991), the War in Afghanistan (Operation Enduring Freedom, 2001–2014), and the Iraq War (Operation Iraqi Freedom, 2003–2011).
As of 2015, CENTCOM forces are deployed primarily in Afghanistan (Operation Resolute Support, 2015–present), Iraq and Syria (Operation Inherent Resolve, 2014–present) in supporting and advise-and-assist roles.
As of 1 September 2016, CENTCOM's commander was General Joseph Votel, U.S. Army.
Of all six American regional unified combatant commands, CENTCOM is among the three with headquarters outside its area of operations (the other two being USAFRICOM and USSOUTHCOM).
CENTCOM's main headquarters is located at MacDill Air Force Base, in Tampa, Florida. A forward headquarters was established in 2002 at Camp As Sayliyah in Doha, Qatar, which in 2009 transitioned to a forward headquarters at Al Udeid Air Base in Qatar.
The United States Central Command (USCENTCOM or CENTCOM) is a theater-level Unified Combatant Command of the U.S. Department of Defense. It was established in 1983, taking over the 1980 Rapid Deployment Joint Task Force (RDJTF) responsibilities.
The CENTCOM Area of Responsibility (AOR) includes countries in the West Asia, parts of North Africa, and Central Asia, most notably Afghanistan and Iraq.
CENTCOM has been the main American presence in many military operations, including :
- the Persian Gulf War (Operation Desert Storm, 1991),
- the War in Afghanistan (Operation Enduring Freedom, 2001–2014),
- and the Iraq War (Operation Iraqi Freedom, 2003–2011).
As of 2015, CENTCOM forces are deployed primarily in Afghanistan (Operation Resolute Support, 2015–present), Iraq and Syria (Operation Inherent Resolve, 2014–present) in supporting and advise-and-assist roles.
As of 1 September 2016, CENTCOM's commander was General Joseph Votel, U.S. Army.
Of all six American regional unified combatant commands, CENTCOM is among the three with headquarters outside its area of operations (the other two being USAFRICOM and USSOUTHCOM).
CENTCOM's main headquarters is located at MacDill Air Force Base, in Tampa, Florida. A forward headquarters was established in 2002 at Camp As Sayliyah in Doha, Qatar, which in 2009 transitioned to a forward headquarters at Al Udeid Air Base in Qatar.
Click on any of the following blue hyperlinks for more about the United States Central Command:
- History
- Structure including War planning
- Geographic scope
- Commanders
- See also:
- U.S. Central Command official website
- Multi-National Force – Iraq.com mnf-iraq.com (in English)
- Spiegel, Peter (5 January 2007). "Naming New Generals A Key Step In Shift On Iraq". Los Angeles Times.
- Foreign Policy, Pentagon Ups the Ante in Syria Fight
- http://www.armytimes.com/story/military/pentagon/2014/12/30/iraq-1st-infantry-funk/21062071/ - Combined Joint Forces Land Component Command - Iraq
- Strategic Army Corps
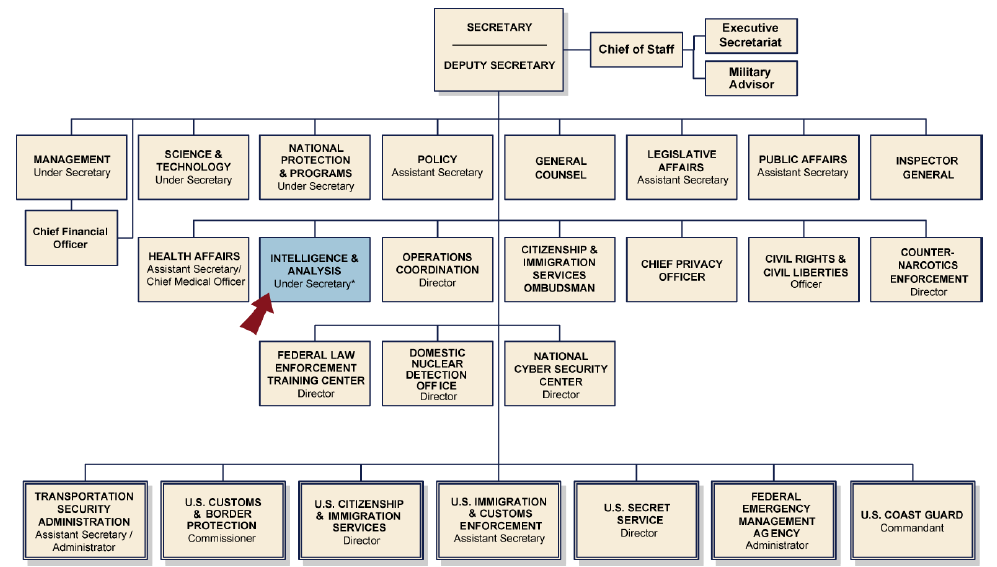
United States Department of Homeland Security
YouTube Video:"We are DHS!"
Pictured below: Organizational Chart for the U.S. Department of Homeland Security
YouTube Video:"We are DHS!"
Pictured below: Organizational Chart for the U.S. Department of Homeland Security
The United States Department of Homeland Security (DHS) is a cabinet department of the United States federal government with responsibilities in public security, roughly comparable to the interior or home ministries of other countries.
Its stated missions involve anti-terrorism, border security, immigration and customs, cyber security, and disaster prevention and management. It was created in response to the September 11 attacks and is the youngest U.S. cabinet department.
In fiscal year 2017, it was allocated a net discretionary budget of $40.6 billion. With more than 240,000 employees, DHS is the third largest Cabinet department, after the Departments of Defense and Veterans Affairs.
Homeland security policy is coordinated at the White House by the Homeland Security Council. Other agencies with significant homeland security responsibilities include the Departments of Health and Human Services, Justice, and Energy.
The former Secretary, John F. Kelly, was replaced by Secretary Kirstjen Nielsen on December 5, 2017.
Function:
Whereas the Department of Defense is charged with military actions abroad, the Department of Homeland Security works in the civilian sphere to protect the United States within, at, and outside its borders.
Its stated goal is to prepare for, prevent, and respond to domestic emergencies, particularly terrorism. On March 1, 2003, DHS absorbed the Immigration and Naturalization Service (INS) and assumed its duties. In doing so, it divided the enforcement and services functions into two separate and new agencies: Immigration and Customs Enforcement and Citizenship and Immigration Services.
The investigative divisions and intelligence gathering units of the INS and Customs Service were merged forming Homeland Security Investigations.
Additionally, the border enforcement functions of the INS, including the U.S. Border Patrol, the U.S. Customs Service, and the Animal and Plant Health Inspection Service were consolidated into a new agency under DHS: U.S. Customs and Border Protection.
The Federal Protective Service falls under the National Protection and Programs Directorate.
Click on any of the following blue hyperlinks for more about The U.S. Department of Homeland Security:
Its stated missions involve anti-terrorism, border security, immigration and customs, cyber security, and disaster prevention and management. It was created in response to the September 11 attacks and is the youngest U.S. cabinet department.
In fiscal year 2017, it was allocated a net discretionary budget of $40.6 billion. With more than 240,000 employees, DHS is the third largest Cabinet department, after the Departments of Defense and Veterans Affairs.
Homeland security policy is coordinated at the White House by the Homeland Security Council. Other agencies with significant homeland security responsibilities include the Departments of Health and Human Services, Justice, and Energy.
The former Secretary, John F. Kelly, was replaced by Secretary Kirstjen Nielsen on December 5, 2017.
Function:
Whereas the Department of Defense is charged with military actions abroad, the Department of Homeland Security works in the civilian sphere to protect the United States within, at, and outside its borders.
Its stated goal is to prepare for, prevent, and respond to domestic emergencies, particularly terrorism. On March 1, 2003, DHS absorbed the Immigration and Naturalization Service (INS) and assumed its duties. In doing so, it divided the enforcement and services functions into two separate and new agencies: Immigration and Customs Enforcement and Citizenship and Immigration Services.
The investigative divisions and intelligence gathering units of the INS and Customs Service were merged forming Homeland Security Investigations.
Additionally, the border enforcement functions of the INS, including the U.S. Border Patrol, the U.S. Customs Service, and the Animal and Plant Health Inspection Service were consolidated into a new agency under DHS: U.S. Customs and Border Protection.
The Federal Protective Service falls under the National Protection and Programs Directorate.
Click on any of the following blue hyperlinks for more about The U.S. Department of Homeland Security:
- Structure
- National Terrorism Advisory System
- History
- Seal
- Headquarters
- Disaster preparedness and response
- Cyber-security
- Expenditures
- Criticism
- See also:
- Official website
- DHS in the Federal Register
- Container Security Initiative
- E-Verify
- Electronic System for Travel Authorization
- Homeland
- Emergency Management Institute
- Homeland Security USA
- Homeland security grant
- List of state departments of homeland security
- National Biodefense Analysis and Countermeasures Center (NBACC), Ft Detrick, MD
- National Interoperability Field Operations Guide
- National Strategy for Homeland Security
- Project Hostile Intent
- Public Safety Canada
- Shadow Wolves
- Terrorism in the United States
- United States visas
- United States Visitor and Immigrant Status Indicator Technology (US-VISIT)
- Visa Waiver Program
United States Air Force
YouTube Video: F 16 Fighter Pilots over Afghanistan
YouTube Video: Awesome Air Show by U.S. Air Force Thunderbirds With F-16 Fighting Falcon
Pictured below: First F-35 Lightning II of the 33rd Fighter Wing arrives at Eglin AFB
The United States Air Force (USAF) is the aerial and space warfare service branch of the United States Armed Forces. It is one of the five branches of the United States Armed Forces, and one of the seven American uniformed services.
Initially established as a part of the United States Army on 1 August 1907, the USAF was formed as a separate branch of the U.S. Armed Forces on 18 September 1947 with the passing of the National Security Act of 1947. It is the youngest branch of the U.S. Armed Forces, and the fourth in order of precedence.
The USAF is the largest and most technologically advanced air force in the world. The Air Force articulates its core missions as:
The U.S. Air Force is a military service branch organized within the Department of the Air Force, one of the three military departments of the Department of Defense (see above). The Air Force, through the Department of the Air Force, is headed by the civilian Secretary of the Air Force, who reports to the Secretary of Defense, and is appointed by the President with Senate confirmation.
The highest-ranking military officer in the Air Force is the Chief of Staff of the Air Force, who exercises supervision over Air Force units and serves as one of the Joint Chiefs of Staff.
Air Force forces are assigned, as directed by the Secretary of Defense, to the combatant commanders, and neither the Secretary of the Air Force nor the Chief of Staff of the Air Force have operational command authority over them.
Along with conducting independent air and space operations, the U.S. Air Force provides air support for land and naval forces and aids in the recovery of troops in the field. As of 2017, the service operates more than 5,369 military aircraft, 406 ICBMs and 170 military satellites.
It has a $161 billion budget and is the second largest service branch, with 318,415 active duty personnel, 140,169 civilian personnel, 69,200 Air Force Reserve personnel, and 105,700 Air National Guard personnel.
Mission:
According to the National Security Act of 1947 (61 Stat. 502), which created the USAF:
In general the United States Air Force shall include aviation forces both combat and service not otherwise assigned.
It shall be organized, trained, and equipped primarily for prompt and sustained offensive and defensive air operations.
The Air Force shall be responsible for the preparation of the air forces necessary for the effective prosecution of war except as otherwise assigned and, in accordance with integrated joint mobilization plans, for the expansion of the peacetime components of the Air Force to meet the needs of war.§8062 of Title 10 US Code defines the purpose of the USAF as:
The stated mission of the USAF today is to "fly, fight, and win in air, space, and cyberspace".
Click on any of the following blue hyperlinks for more about the United States Air Force:
Initially established as a part of the United States Army on 1 August 1907, the USAF was formed as a separate branch of the U.S. Armed Forces on 18 September 1947 with the passing of the National Security Act of 1947. It is the youngest branch of the U.S. Armed Forces, and the fourth in order of precedence.
The USAF is the largest and most technologically advanced air force in the world. The Air Force articulates its core missions as:
- air and space superiority,
- global integrated ISR,
- rapid global mobility,
- global strike, and command and control.
The U.S. Air Force is a military service branch organized within the Department of the Air Force, one of the three military departments of the Department of Defense (see above). The Air Force, through the Department of the Air Force, is headed by the civilian Secretary of the Air Force, who reports to the Secretary of Defense, and is appointed by the President with Senate confirmation.
The highest-ranking military officer in the Air Force is the Chief of Staff of the Air Force, who exercises supervision over Air Force units and serves as one of the Joint Chiefs of Staff.
Air Force forces are assigned, as directed by the Secretary of Defense, to the combatant commanders, and neither the Secretary of the Air Force nor the Chief of Staff of the Air Force have operational command authority over them.
Along with conducting independent air and space operations, the U.S. Air Force provides air support for land and naval forces and aids in the recovery of troops in the field. As of 2017, the service operates more than 5,369 military aircraft, 406 ICBMs and 170 military satellites.
It has a $161 billion budget and is the second largest service branch, with 318,415 active duty personnel, 140,169 civilian personnel, 69,200 Air Force Reserve personnel, and 105,700 Air National Guard personnel.
Mission:
According to the National Security Act of 1947 (61 Stat. 502), which created the USAF:
In general the United States Air Force shall include aviation forces both combat and service not otherwise assigned.
It shall be organized, trained, and equipped primarily for prompt and sustained offensive and defensive air operations.
The Air Force shall be responsible for the preparation of the air forces necessary for the effective prosecution of war except as otherwise assigned and, in accordance with integrated joint mobilization plans, for the expansion of the peacetime components of the Air Force to meet the needs of war.§8062 of Title 10 US Code defines the purpose of the USAF as:
- to preserve the peace and security, and provide for the defense, of the United States, the Territories, Commonwealths, and possessions, and any areas occupied by the United States;
- to support national policy;
- to implement national objectives;
- to overcome any nations responsible for aggressive acts that imperil the peace and security of the United States.
The stated mission of the USAF today is to "fly, fight, and win in air, space, and cyberspace".
Click on any of the following blue hyperlinks for more about the United States Air Force:
- Vision
- Core missions
- History
- Organization
- Personnel
- Aircraft inventory
- Culture
- Air Force Academy
- See also:
- Official:
- Other:
- Searchable database of Air Force historical reports
- USAF emblems
- Members of the US Air Force on RallyPoint
- Aircraft Investment Plan, Fiscal Years (FY) 2011–2040, Submitted with the FY 2011 Budget
- National Commission on the Structure of the Air Force: Report to the President and the Congress of the United States
- Works by or about United States Air Force at Internet Archive
- Airman's Creed
- Air Force Association
- Air Force Combat Ammunition Center
- Air Force Knowledge Now
- Company Grade Officers' Council
- Department of the Air Force Police
- Future military aircraft of the United States
- List of active United States military aircraft
- List of United States Air Force installations
- List of United States Airmen
- List of U.S. Air Force acronyms and expressions
- National Museum of the United States Air Force
- Structure of the United States Air Force
- United States Air Force Band
- United States Air Force Chaplain Corps
- United States Air Force Combat Control Team
- United States Air Force Medical Service
- United States Air Force Thunderbirds
- Women in the United States Air Force
United States Army
YouTube Video: Tribute to Women in the U.S. Army
Pictured below: 23 distinct styles of dress which represents and honors the American Patriots and Pioneers who helped found the United States and the U.S. Army Soldiers who served while wearing these uniforms, weapons, and accouterments — during some of the most well-known and significant conflicts since the first militia musters of the 17th century. Shot in 4K and featuring Mark Aaron as "the soldier
The United States Army (USA) is the land warfare service branch of the United States Armed Forces. It is one of the seven uniformed services of the United States, and is designated as the Army of the United States in the United States Constitution, Article 2, Section 2, Clause 1] and United States Code, Title 10, Subtitle B, Chapter 301, Section 3001].
As the oldest and most senior branch of the U.S. military in order of precedence, the modern U.S. Army has its roots in the Continental Army, which was formed (14 June 1775) to fight the American Revolutionary War (1775–1783)—before the United States of America was established as a country.
After the Revolutionary War, the Congress of the Confederation created the United States Army on 3 June 1784 to replace the disbanded Continental Army. The United States Army considers itself descended from the Continental Army, and dates its institutional inception from the origin of that armed force in 1775.
As a uniformed military service, the U.S. Army is part of the Department of the Army, which is one of the three military departments of the Department of Defense. The U.S. Army is headed by a civilian senior appointed civil servant, the Secretary of the Army (SECARMY) and by a chief military officer, the Chief of Staff of the Army (CSA) who is also a member of the Joint Chiefs of Staff.
It is the largest military branch, and in the fiscal year 2017, the projected end strength for the Regular Army (USA) was 476,000 soldiers; the Army National Guard (ARNG) had 343,000 soldiers and the United States Army Reserve (USAR) had 199,000 soldiers; the combined-component strength of the U.S. Army was 1,018,000 soldiers.[4]
As a branch of the armed forces, the mission of the U.S. Army is "to fight and win our Nation's wars, by providing prompt, sustained, land dominance, across the full range of military operations and the spectrum of conflict, in support of combatant commanders". The branch participates in conflicts worldwide and is the major ground-based offensive and defensive force of the United States.
Mission:
The United States Army serves as the land-based branch of the U.S. Armed Forces. Section 3062 of Title 10, U.S. Code defines the purpose of the army as:
Click on any of the following blue hyperlinks for more about the United States Army:
As the oldest and most senior branch of the U.S. military in order of precedence, the modern U.S. Army has its roots in the Continental Army, which was formed (14 June 1775) to fight the American Revolutionary War (1775–1783)—before the United States of America was established as a country.
After the Revolutionary War, the Congress of the Confederation created the United States Army on 3 June 1784 to replace the disbanded Continental Army. The United States Army considers itself descended from the Continental Army, and dates its institutional inception from the origin of that armed force in 1775.
As a uniformed military service, the U.S. Army is part of the Department of the Army, which is one of the three military departments of the Department of Defense. The U.S. Army is headed by a civilian senior appointed civil servant, the Secretary of the Army (SECARMY) and by a chief military officer, the Chief of Staff of the Army (CSA) who is also a member of the Joint Chiefs of Staff.
It is the largest military branch, and in the fiscal year 2017, the projected end strength for the Regular Army (USA) was 476,000 soldiers; the Army National Guard (ARNG) had 343,000 soldiers and the United States Army Reserve (USAR) had 199,000 soldiers; the combined-component strength of the U.S. Army was 1,018,000 soldiers.[4]
As a branch of the armed forces, the mission of the U.S. Army is "to fight and win our Nation's wars, by providing prompt, sustained, land dominance, across the full range of military operations and the spectrum of conflict, in support of combatant commanders". The branch participates in conflicts worldwide and is the major ground-based offensive and defensive force of the United States.
Mission:
The United States Army serves as the land-based branch of the U.S. Armed Forces. Section 3062 of Title 10, U.S. Code defines the purpose of the army as:
- Preserving the peace and security and providing for the defense of the United States, the Commonwealths and possessions and any areas occupied by the United States
- Supporting the national policies
- Implementing the national objectives
- Overcoming any nations responsible for aggressive acts that imperil the peace and security of the United States
Click on any of the following blue hyperlinks for more about the United States Army:
- History
- Organization
- Personnel
- Equipment
- See also:
- Army.mil – United States Army official website
- Army.mil/photos – United States Army featured photos
- GoArmy.com – official recruiting site
- U.S. Army Collection – Missouri History Museum
- Finding Aids for researching the U.S. Army (compiled by the United States Army Center of Military History)
- America's Army (Video games for recruitment)
- Army CHESS (Computer Hardware Enterprise Software and Solutions)
- Army National Guard
- Comparative military ranks
- History of the United States Army
- List of active United States military aircraft
- List of former United States Army medical units
- List of wars involving the United States
- Military–industrial complex
- Officer Candidate School (United States Army)
- Reserve Officers' Training Corps and Junior Reserve Officers' Training Corps
- Soldier's Creed
- Structure of the United States Army
- Timeline of United States military operations
- Transformation of the United States Army
- U.S. Army Combat Arms Regimental System
- U.S. Army Regimental System
- United States Military Academy
- United States Army Basic Training
- United States Army Center of Military History
- United States Volunteers
- Vehicle markings of the United States military
- Warrant Officer Candidate School (United States Army)
United States Navy
YouTube Video: Watch a US Navy aircraft carrier launch all its F-18 fighter jets
YouTube Video: Life Aboard US Navy Ballistic Missile Submarine USS Wyoming
Pictured below:
TOP: The aircraft carrier Dwight D. Eisenhower (CVN 69) of the US Navy on a mission
BOTTOM: US launches 'most advanced' stealth sub amid undersea rivalry
The United States Navy (USN) is the naval warfare service branch of the United States Armed Forces and one of the seven uniformed services of the United States. It is the largest and most capable navy in the world, with the highest combined battle fleet tonnage and the world's largest aircraft carrier fleet, with eleven in service, and two new carriers under construction.
With 319,421 personnel on active duty and 99,616 in the Ready Reserve, the Navy is the third largest of the service branches. It has 282 deployable combat vessels and more than 3,700 operational aircraft as of March 2018. making it the second largest and second most powerful air force in the world.
The U.S. Navy traces its origins to the Continental Navy, which was established during the American Revolutionary War and was effectively disbanded as a separate entity shortly thereafter. The U.S. Navy played a major role in the American Civil War by blockading the Confederacy and seizing control of its rivers. It played the central role in the World War II defeat of Imperial Japan.
The 21st century U.S. Navy maintains a sizable global presence, deploying in strength in such areas as the Western Pacific, the Mediterranean, and the Indian Ocean. It is a blue-water navy with the ability to project force onto the littoral regions of the world, engage in forward deployments during peacetime and rapidly respond to regional crises, making it a frequent actor in U.S. foreign and military policy.
The Navy is administratively managed by the Department of the Navy, which is headed by the civilian Secretary of the Navy. The Department of the Navy is itself a division of the Department of Defense, which is headed by the Secretary of Defense. The Chief of Naval Operations (CNO) is the most senior naval officer serving in the Department of the Navy.
Mission:
The mission of the Navy is to maintain, train and equip combat-ready Naval forces capable of winning wars, deterring aggression and maintaining freedom of the seas.
— Mission statement of the United States Navy.
The U.S. Navy is a seaborne branch of the military of the United States. The Navy's three primary areas of responsibility:
U.S. Navy training manuals state that the mission of the U.S. Armed Forces is "to be prepared to conduct prompt and sustained combat operations in support of the national interest. "As part of that establishment, the U.S. Navy's functions comprise sea control, power projection and nuclear deterrence, in addition to "sealift" duties
Click on any of the following blue hyperlinks for more about the United States Navy:
With 319,421 personnel on active duty and 99,616 in the Ready Reserve, the Navy is the third largest of the service branches. It has 282 deployable combat vessels and more than 3,700 operational aircraft as of March 2018. making it the second largest and second most powerful air force in the world.
The U.S. Navy traces its origins to the Continental Navy, which was established during the American Revolutionary War and was effectively disbanded as a separate entity shortly thereafter. The U.S. Navy played a major role in the American Civil War by blockading the Confederacy and seizing control of its rivers. It played the central role in the World War II defeat of Imperial Japan.
The 21st century U.S. Navy maintains a sizable global presence, deploying in strength in such areas as the Western Pacific, the Mediterranean, and the Indian Ocean. It is a blue-water navy with the ability to project force onto the littoral regions of the world, engage in forward deployments during peacetime and rapidly respond to regional crises, making it a frequent actor in U.S. foreign and military policy.
The Navy is administratively managed by the Department of the Navy, which is headed by the civilian Secretary of the Navy. The Department of the Navy is itself a division of the Department of Defense, which is headed by the Secretary of Defense. The Chief of Naval Operations (CNO) is the most senior naval officer serving in the Department of the Navy.
Mission:
The mission of the Navy is to maintain, train and equip combat-ready Naval forces capable of winning wars, deterring aggression and maintaining freedom of the seas.
— Mission statement of the United States Navy.
The U.S. Navy is a seaborne branch of the military of the United States. The Navy's three primary areas of responsibility:
- The preparation of naval forces necessary for the effective prosecution of war.
- The maintenance of naval aviation, including land-based naval aviation, air transport essential for naval operations, and all air weapons and air techniques involved in the operations and activities of the Navy.
- The development of aircraft, weapons, tactics, technique, organization, and equipment of naval combat and service elements.
U.S. Navy training manuals state that the mission of the U.S. Armed Forces is "to be prepared to conduct prompt and sustained combat operations in support of the national interest. "As part of that establishment, the U.S. Navy's functions comprise sea control, power projection and nuclear deterrence, in addition to "sealift" duties
Click on any of the following blue hyperlinks for more about the United States Navy:
- History
- Organization
- Personnel
- Bases
- Equipment
- Naval jack
- Notable sailors
- See also:
- Official website
- "U.S. Naval Institute".
- A Cooperative Strategy for 21st Century Seapower
- "Navy.com, USN official recruitment site".
- "U.S. Navy News website".
- "US Navy". GlobalSecurity.
- D'Alessandro, Michael P. (ed.). "Naval Open Source Intelligence".
- "United States Navy Official Website".
- Lanzendörfer, Tim. "The Pacific War: The U.S. Navy".
- "United States Navy Memorial".
- America's Naval Hardware – Life magazine slideshow
- "Photographic History of The U.S. Navy". Naval History. NavSource.
- "Haze Gray & Underway – Naval History and Photography". HazeGray.org.
- "U.S. Navy Ships". Military Analysis Network. Federation of America Scientists.
- U.S. Navy during the Cold War from the Dean Peter Krogh Foreign Affairs Digital Archives
- "United States Navy in World War I". World War I at Sea.net. Retrieved 3 February 2007. (Includes warship losses.)
- "U.S. Navy in World War II". World War II on the World Wide Web. Hyper War. (Includes The Official Chronology of the U.S. Navy in World War II.)
- "Our Fighting Ships". U.S. WW II Newsmap. Army Orientation Course. 29 June 1942. Hosted by the UNT Libraries Digital Collections
- "Strict Neutrality – Britain & France at War with Germany, September 1939 – May 1940". United States Navy and World War II. Naval-History.net.
- "The National Security Strategy of the United States of America".
- "Naval recognition-Grand Valley State University Archives and Special Collections".
- "US Navy SEALs Directory".
- United States Navy at the Wayback Machine (archived 4 January 1997)
- Ohio Replacement Submarine
- Spearhead-class expeditionary fast transport
- Bibliography of early American naval history
- Modern United States Navy carrier air operations
- Naval militia
- Women in the United States Navy
- United States Merchant Marine Academy
United States Marine Corps
YouTube Video: Marine Cpl. Carpenter awarded Medal of Honor
Pictured below: (L) Marines raising the Flag on Iwo Jima; (R) Two of the first female graduates of the School of Infantry-East's Infantry Training Battalion course, 2013
The United States Marine Corps (USMC), also referred to as the United States Marines, is a branch of the United States Armed Forces responsible for conducting expeditionary and amphibious operations with (per the topics above) the United States Navy as well as the Army and Air Force.
The U.S. Marine Corps is one of the four armed service branches in the U.S. Department of Defense (DoD) and one of the seven uniformed services of the United States.
The Marine Corps has been a component of the U.S. Department of the Navy since 30 June 1834, working closely with naval forces.
The USMC operates installations on land and aboard sea-going amphibious warfare ships around the world. Additionally, several of the Marines' tactical aviation squadrons, primarily Marine Fighter Attack squadrons, are also embedded in Navy carrier air wings and operate from the aircraft carriers.
The history of the Marine Corps began when two battalions of Continental Marines were formed on 10 November 1775 in Philadelphia as a service branch of infantry troops capable of fighting both at sea and on shore.
In the Pacific theater of World War II the Corps took the lead in a massive campaign of amphibious warfare, advancing from island to island. As of 2017, the USMC has around 186,000 active duty members and some 38,500 reserve Marines. It is the smallest U.S. military service within the DoD.
Mission:
As outlined in 10 U.S.C. § 5063 and as originally introduced under the National Security Act of 1947, three primary areas of responsibility for the Marine Corps are:
Click on any of the following blue hyperlinks for more about the United States Marine Corp:
The U.S. Marine Corps is one of the four armed service branches in the U.S. Department of Defense (DoD) and one of the seven uniformed services of the United States.
The Marine Corps has been a component of the U.S. Department of the Navy since 30 June 1834, working closely with naval forces.
The USMC operates installations on land and aboard sea-going amphibious warfare ships around the world. Additionally, several of the Marines' tactical aviation squadrons, primarily Marine Fighter Attack squadrons, are also embedded in Navy carrier air wings and operate from the aircraft carriers.
The history of the Marine Corps began when two battalions of Continental Marines were formed on 10 November 1775 in Philadelphia as a service branch of infantry troops capable of fighting both at sea and on shore.
In the Pacific theater of World War II the Corps took the lead in a massive campaign of amphibious warfare, advancing from island to island. As of 2017, the USMC has around 186,000 active duty members and some 38,500 reserve Marines. It is the smallest U.S. military service within the DoD.
Mission:
As outlined in 10 U.S.C. § 5063 and as originally introduced under the National Security Act of 1947, three primary areas of responsibility for the Marine Corps are:
- Seizure or defense of advanced naval bases and other land operations to support naval campaigns;
- Development of tactics, technique, and equipment used by amphibious landing forces in coordination with the Army and Air Force; and
- Such other duties as the President or Department of Defense may direct.
Click on any of the following blue hyperlinks for more about the United States Marine Corp:
- Mission
- History
- Organization
- Special Operations
- Personnel
- Uniforms
- Culture
- Equipment
- Relationship with other services
- Budget
- See also:
- United States Marine Corps Women's Reserve
- Marines.mil – Official site
- Official USMC recruitment site
- Marine Corps recruitment video
- Marine Corps History Division
- A Cooperative Strategy for 21st Century Seapower
- Marine Corps Heritage Foundation
- Online Marine community
- Members of the USMC on RallyPoint
- An Unofficial Dictionary for Marines
United States Coast Guard
YouTube Video: Coast Guard Top 10 Rescue Videos
Pictured below: United States Coast Guard medevacs man south of Panama City, FL
The United States Coast Guard (USCG) is a branch of the United States Armed Forces and one of the country's seven uniformed services.
The Coast Guard is a maritime, military, multi-mission service unique among the U.S. military branches for having a maritime law enforcement mission (with jurisdiction in both domestic and international waters) and a federal regulatory agency mission as part of its mission set.
USCG operates under the U.S. Department of Homeland Security during peacetime, and can be transferred to the U.S. Department of the Navy by the U.S. President at any time, or by the U.S. Congress during times of war. This has happened twice, in 1917, during World War I, and in 1941, during World War II.
Created by Congress on 4 August 1790 at the request of Alexander Hamilton as the Revenue Marine, it is the oldest continuous seagoing service of the United States. As Secretary of the Treasury, Hamilton headed the Revenue Marine, whose original purpose was collecting customs duties in the nation's seaports.
By the 1860s, the service was known as the U.S. Revenue Cutter Service and the term Revenue Marine gradually fell into disuse.
The modern Coast Guard was formed by a merger of the Revenue Cutter Service and the U.S. Life-Saving Service on 28 January 1915, under the U.S. Department of the Treasury. As one of the country's five armed services, the Coast Guard has been involved in every U.S. war from 1790 to the Iraq War and the War in Afghanistan.
The Coast Guard has 40,992 men and women on active duty, 7,000 reservists, 31,000 auxiliarists, and 8,577 full-time civilian employees, for a total workforce of 87,569.
The Coast Guard maintains an extensive fleet of 243 coastal and ocean-going patrol ships, tenders, tugs and icebreakers called "Cutters", and 1650 smaller boats, as well as an extensive aviation division consisting of 201 helicopters and fixed-wing aircraft.
While the U.S. Coast Guard is the smallest of the U.S. military service branches, in terms of size, the U.S. Coast Guard by itself is the world's 12th largest naval force.
Click on any of the following blue hyperlinks for more about the United States Coast Guard:
The Coast Guard is a maritime, military, multi-mission service unique among the U.S. military branches for having a maritime law enforcement mission (with jurisdiction in both domestic and international waters) and a federal regulatory agency mission as part of its mission set.
USCG operates under the U.S. Department of Homeland Security during peacetime, and can be transferred to the U.S. Department of the Navy by the U.S. President at any time, or by the U.S. Congress during times of war. This has happened twice, in 1917, during World War I, and in 1941, during World War II.
Created by Congress on 4 August 1790 at the request of Alexander Hamilton as the Revenue Marine, it is the oldest continuous seagoing service of the United States. As Secretary of the Treasury, Hamilton headed the Revenue Marine, whose original purpose was collecting customs duties in the nation's seaports.
By the 1860s, the service was known as the U.S. Revenue Cutter Service and the term Revenue Marine gradually fell into disuse.
The modern Coast Guard was formed by a merger of the Revenue Cutter Service and the U.S. Life-Saving Service on 28 January 1915, under the U.S. Department of the Treasury. As one of the country's five armed services, the Coast Guard has been involved in every U.S. war from 1790 to the Iraq War and the War in Afghanistan.
The Coast Guard has 40,992 men and women on active duty, 7,000 reservists, 31,000 auxiliarists, and 8,577 full-time civilian employees, for a total workforce of 87,569.
The Coast Guard maintains an extensive fleet of 243 coastal and ocean-going patrol ships, tenders, tugs and icebreakers called "Cutters", and 1650 smaller boats, as well as an extensive aviation division consisting of 201 helicopters and fixed-wing aircraft.
While the U.S. Coast Guard is the smallest of the U.S. military service branches, in terms of size, the U.S. Coast Guard by itself is the world's 12th largest naval force.
Click on any of the following blue hyperlinks for more about the United States Coast Guard:
- Mission
- A typical day
- History
- Organization
- Personnel
- Equipment
- Symbols
- Uniforms
- Coast Guard Reserve
- Women in the Coast Guard
- Coast Guard Auxiliary
- Deployable Operations Group
- Medals and honors
- Notable Coast Guardsmen
- Organizations
- In popular culture
- See also:
- U.S. Coast Guard Website
- Women & the U. S. Coast Guard
- Coast Guard in the Federal Register
- Reports on the Coast Guard, Department of Homeland Security Office of Inspector General
- 'A Cooperative Strategy for 21st Century Seapower'
- U.S. Coast Guard Videos
- Coast Guard Personnel Locator
- All Comprehensive Security Plans for Mid and High Value Homes
- How to join the U.S. Coast Guard
- U.S. Coast Guard Auxiliary Website
- Coast Guard Channel
- Coast Guard News
- Greg Trauthwein (17 March 2014). "USCG ... Past, Present & Future". Maritime Reporter and Marine News magazines online. Retrieved 26 February 2015.
- America's Waterway Watch at the Library of Congress Web Archives (archived 2010-12-13)
- United States Coast Guard at the Wayback Machine (archived 29 January 1997)
- Coast Guard:
- AMVER
- Badges of the United States Coast Guard
- Chaplain of the Coast Guard
- Coast Guard Day
- Code of Federal Regulations, Title 33
- Joint Maritime Training Center
- List of United States Coast Guard cutters
- Maritime Law Enforcement Academy
- MARSEC
- National Data Buoy Center
- National Ice Center
- Naval militia
- North Pacific Coast Guard Agencies Forum
- Patrol Forces Southwest Asia
- SPARS
- U.S. Coast Guard Intelligence
- U.S. Coast Guard Legal Division
- United States Coast Guard Air Stations
- United States Coast Guard Police
- United States Coast Guard Research & Development Center
- United States Coast Guard Stations
- Women in the United States Coast Guard
- Related agencies:
Mutual Assured Destruction (Global Nuclear Policy), including the Doomsday Clock
TOP: Donald Trump wants to ‘greatly’ expand U.S. nuclear capability. Here’s what that means. (Washington Post 12/22/2016)
BOTTOM: The Doomsday Clock just ticked closer to midnight (USA Today 1/25/2018)
- "YouTube Video: Nuclear 'Doomsday Clock' Is The Closest To Midnight It's Been Since The Cold War | TIME 1/28/2018
- YouTube Video: The insanity of nuclear deterrence Robert Green | TEDxChristchurch
- YouTube Video: Mutual assured destruction - Video Learning - WizScience.com
TOP: Donald Trump wants to ‘greatly’ expand U.S. nuclear capability. Here’s what that means. (Washington Post 12/22/2016)
BOTTOM: The Doomsday Clock just ticked closer to midnight (USA Today 1/25/2018)
Mutual assured destruction or mutually assured destruction (MAD) is a doctrine of military strategy and national security policy in which a full-scale use of nuclear weapons by two or more opposing sides would cause the complete annihilation of both the attacker and the defender (see pre-emptive nuclear strike and second strike).
MAD is based on the theory of deterrence, which holds that the threat of using strong weapons against the enemy prevents the enemy's use of those same weapons. The strategy is a form of Nash equilibrium in which, once armed, neither side has any incentive to initiate a conflict or to disarm.
Theory:
Under MAD, each side has enough nuclear weaponry to destroy the other side and that either side, if attacked for any reason by the other, would retaliate with equal or greater force. The expected result is an immediate, irreversible escalation of hostilities resulting in both combatants' mutual, total, and assured destruction.
The doctrine requires that neither side construct shelters on a massive scale. If one side constructed a similar system of shelters, it would violate the MAD doctrine and destabilize the situation, because it would have less to fear from a second strike. The same principle is invoked against missile defense.
The doctrine further assumes that neither side will dare to launch a first strike because the other side would launch on warning (also called fail-deadly) or with surviving forces (a second strike), resulting in unacceptable losses for both parties. The payoff of the MAD doctrine was and still is expected to be a tense but stable global peace.
The primary application of this doctrine started during the Cold War (1940s to 1991), in which MAD was seen as helping to prevent any direct full-scale conflicts between the United States and the Soviet Union while they engaged in smaller proxy wars around the world. It was also responsible for the arms race, as both nations struggled to keep nuclear parity, or at least retain second-strike capability. Although the Cold War ended in the early 1990s, the MAD doctrine continues to be applied.
Proponents of MAD as part of US and USSR strategic doctrine believed that nuclear war could best be prevented if neither side could expect to survive a full-scale nuclear exchange as a functioning state. Since the credibility of the threat is critical to such assurance, each side had to invest substantial capital in their nuclear arsenals even if they were not intended for use.
In addition, neither side could be expected or allowed to adequately defend itself against the other's nuclear missiles. This led both to the hardening and diversification of nuclear delivery systems (such as nuclear missile silos, ballistic missile submarines, and nuclear bombers kept at fail-safe points) and to the Anti-Ballistic Missile Treaty.
This MAD scenario is often referred to as nuclear deterrence. The term "deterrence" is now used in this context; originally, its use was limited to legal terminology.
Click on any of the following blue hyperlinks for more about Mutual Assured Destruction (MAD):
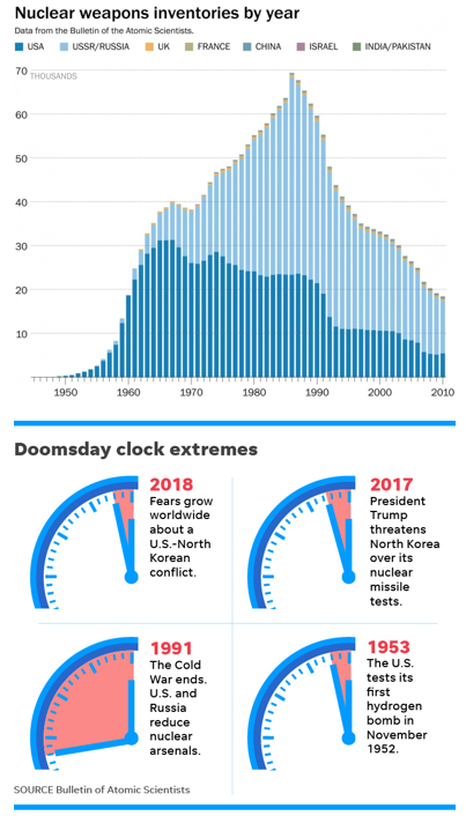
The Doomsday Clock is a symbol which represents the likelihood of a man-made global catastrophe. Maintained since 1947 by the members of the Bulletin of the Atomic Scientists, The Clock is a metaphor for threats to humanity from unchecked scientific and technical advances. The Clock represents the hypothetical global catastrophe as "midnight" and the Bulletin's opinion on how close the world is to a global catastrophe as a number of "minutes" to midnight.
The factors influencing the Clock are nuclear risk and climate change. The Bulletin's Science and Security Board also monitors new developments in the life sciences and technology that could inflict irrevocable harm to humanity.
The Clock's original setting in 1947 was seven minutes to midnight. It has been set backward and forward 23 times since then, the smallest-ever number of minutes to midnight being two (in 1953 and 2018) and the largest seventeen (in 1991).
The most recent officially announced setting—2 minutes to midnight—was made in January 2018, which was left unchanged in 2019 due to the twin threats of nuclear weapons and climate change, and the problem of those threats being "exacerbated this past year by the increased use of information warfare to undermine democracy around the world, amplifying risk from these and other threats and putting the future of civilization in extraordinary danger.”
Click on any of the following blue hyperlinks for more about the Doomsday Clock:
MAD is based on the theory of deterrence, which holds that the threat of using strong weapons against the enemy prevents the enemy's use of those same weapons. The strategy is a form of Nash equilibrium in which, once armed, neither side has any incentive to initiate a conflict or to disarm.
Theory:
Under MAD, each side has enough nuclear weaponry to destroy the other side and that either side, if attacked for any reason by the other, would retaliate with equal or greater force. The expected result is an immediate, irreversible escalation of hostilities resulting in both combatants' mutual, total, and assured destruction.
The doctrine requires that neither side construct shelters on a massive scale. If one side constructed a similar system of shelters, it would violate the MAD doctrine and destabilize the situation, because it would have less to fear from a second strike. The same principle is invoked against missile defense.
The doctrine further assumes that neither side will dare to launch a first strike because the other side would launch on warning (also called fail-deadly) or with surviving forces (a second strike), resulting in unacceptable losses for both parties. The payoff of the MAD doctrine was and still is expected to be a tense but stable global peace.
The primary application of this doctrine started during the Cold War (1940s to 1991), in which MAD was seen as helping to prevent any direct full-scale conflicts between the United States and the Soviet Union while they engaged in smaller proxy wars around the world. It was also responsible for the arms race, as both nations struggled to keep nuclear parity, or at least retain second-strike capability. Although the Cold War ended in the early 1990s, the MAD doctrine continues to be applied.
Proponents of MAD as part of US and USSR strategic doctrine believed that nuclear war could best be prevented if neither side could expect to survive a full-scale nuclear exchange as a functioning state. Since the credibility of the threat is critical to such assurance, each side had to invest substantial capital in their nuclear arsenals even if they were not intended for use.
In addition, neither side could be expected or allowed to adequately defend itself against the other's nuclear missiles. This led both to the hardening and diversification of nuclear delivery systems (such as nuclear missile silos, ballistic missile submarines, and nuclear bombers kept at fail-safe points) and to the Anti-Ballistic Missile Treaty.
This MAD scenario is often referred to as nuclear deterrence. The term "deterrence" is now used in this context; originally, its use was limited to legal terminology.
Click on any of the following blue hyperlinks for more about Mutual Assured Destruction (MAD):
- History
- Official policy
- Criticism
- See also
- Absolute war
- Appeasement
- Balance of terror
- Counterforce
- Moral equivalence
- Nuclear winter
- Nuclear missile defense
- Nuclear holocaust
- Nuclear peace
- Nuclear strategy
- Pyrrhic victory
- Rational choice theory
- Weapon of mass destruction
- "The Rise of U.S. Nuclear Primacy" from Foreign Affairs, March/April 2006
- First Strike and Mutual Deterrence from the Dean Peter Krogh Foreign Affairs Digital Archives
- Herman Kahn's Doomsday Machine
- Robert McNamara's "Mutual Deterrence" speech from 1967
- Center for Arms Control and Non-Proliferation
- Nuclear Files.org Mutual Assured Destruction
- John G. Hines et al. Soviet Intentions 1965–1985. BDM, 1995.
The Doomsday Clock is a symbol which represents the likelihood of a man-made global catastrophe. Maintained since 1947 by the members of the Bulletin of the Atomic Scientists, The Clock is a metaphor for threats to humanity from unchecked scientific and technical advances. The Clock represents the hypothetical global catastrophe as "midnight" and the Bulletin's opinion on how close the world is to a global catastrophe as a number of "minutes" to midnight.
The factors influencing the Clock are nuclear risk and climate change. The Bulletin's Science and Security Board also monitors new developments in the life sciences and technology that could inflict irrevocable harm to humanity.
The Clock's original setting in 1947 was seven minutes to midnight. It has been set backward and forward 23 times since then, the smallest-ever number of minutes to midnight being two (in 1953 and 2018) and the largest seventeen (in 1991).
The most recent officially announced setting—2 minutes to midnight—was made in January 2018, which was left unchanged in 2019 due to the twin threats of nuclear weapons and climate change, and the problem of those threats being "exacerbated this past year by the increased use of information warfare to undermine democracy around the world, amplifying risk from these and other threats and putting the future of civilization in extraordinary danger.”
Click on any of the following blue hyperlinks for more about the Doomsday Clock:
- History
- Reception
- In popular culture
- See also:
Artificial Intelligence Arms Race, including How A.I. Could Be Weaponized to Spread Disinformation
by New York Times
by New York Times
- YouTube Video: the Threat of A.I. Weapons
- YouTube Video: What happens when our computers get smarter than we are? by Nick Bostrom (TED.com)
- YouTube Video: Artificial Intelligence: it will kill us by Jay Tuck TEDxHamburgSalon
Click here for background about Artificial Intelligence
Click here to see New York Times OpEd: "How A.I. Could Be Weaponized to Spread Disinformation" By Cade Metz and Scott Blumenthal of the New York Times June 7, 2019
Artificial Arms Race:
An artificial intelligence arms race is a competition between two or more states to have its military forces equipped with the best "artificial intelligence" (AI). Since the mid-2010s, many analysts have argued that a such a global arms race for better artificial intelligence has already begun.
Stances toward military artificial intelligence:
Russia:
Russian General Viktor Bondarev, commander-in-chief of the Russian air force, has stated that as early as February 2017, Russia has been working on AI-guided missiles that can decide to switch targets mid-flight.
Reports by state-sponsored Russian media on potential military uses of AI increased in mid-2017. In May 2017, the CEO of Russia's Kronstadt Group, a defense contractor, stated that "there already exist completely autonomous AI operation systems that provide the means for UAV clusters, when they fulfill missions autonomously, sharing tasks between them, and interact", and that it is inevitable that "swarms of drones" will one day fly over combat zones.
Russia has been testing several autonomous and semi-autonomous combat systems, such as Kalashnikov's "neural net" combat module, with a machine gun, a camera, and an AI that its makers claim can make its own targeting judgements without human intervention.
In September 2017, during a National Knowledge Day address to over a million students in 16,000 Russian schools, Russian President Vladimir Putin stated "Artificial intelligence is the future, not only for Russia but for all humankind... Whoever becomes the leader in this sphere will become the ruler of the world".
The Russian government has strongly rejected any ban on lethal autonomous weapons systems, suggesting that such a ban could be ignored.
China:
Further information: Artificial intelligence industry in China
According to a February 2019 report by Gregory C. Allen of the Center for a New American Security, "China’s leadership – including President Xi Jinping – believes that being at the forefront in AI technology is critical to the future of global military and economic power competition."
Chinese military officials have said that their goal is to incorporate commercial AI technology to "narrow the gap between the Chinese military and global advanced powers."
The close ties between Silicon Valley and China, and the open nature of the American research community, has made the West's most advanced AI technology easily available to China; in addition, Chinese industry has numerous home-grown AI accomplishments of its own, such as Baidu passing a notable Chinese-language speech recognition capability benchmark in 2015. As of 2017, Beijing's roadmap aims to create a $150 billion AI industry by 2030.
Before 2013, Chinese defense procurement was mainly restricted to a few conglomerates; however, as of 2017, China often sources sensitive emerging technology such as drones and artificial intelligence from private start-up companies.
One Chinese state has pledged to invest $5 billion in AI. Beijing has committed $2 billion to an AI development park. The Japan Times reported in 2018 that annual private Chinese investment in AI is under $7 billion per year. AI startups in China received nearly half of total global investment in AI startups in 2017; the Chinese filed for nearly five times as many AI patents as did Americans.
China published a position paper in 2016 questioning the adequacy of existing international law to address the eventuality of fully autonomous weapons, becoming the first permanent member of the U.N. Security Council to broach the issue.
United States:
In 2014, former Secretary of Defense Chuck Hagel posited the "Third Offset Strategy" that rapid advances in artificial intelligence will define the next generation of warfare. According to data science and analytics firm Govini, The U.S. Department of Defense increased investment in artificial intelligence, big data and cloud computing from $5.6 billion in 2011 to $7.4 billion in 2016. However, the civilian NSF budget for AI saw no increase in 2017.
The U.S. has many military AI combat programs, such as the Sea Hunter autonomous warship, which is designed to operate for extended periods at sea without a single crew member, and to even guide itself in and out of port. As of 2017, a temporary US Department of Defense directive requires a human operator to be kept in the loop when it comes to the taking of human life by autonomous weapons systems. Japan Times reported in 2018 that the United States private investment is around $70 billion per year.
United Kingdom:
In 2015, the UK government opposed a ban on lethal autonomous weapons, stating that "international humanitarian law already provides sufficient regulation for this area", but that all weapons employed by UK armed forces would be "under human oversight and control".
Israel:
Israel's Harpy anti-radar "fire and forget" drone is designed to be launched by ground troops, and autonomously fly over an area to find and destroy radar that fits pre-determined criteria.
South Korea:
The South Korean Super aEgis II machine gun, unveiled in 2010, sees use both in South Korea and in the Middle East. It can identify, track, and destroy a moving target at a range of 4 km.
While the technology can theoretically operate without human intervention, in practice safeguards are installed to require manual input. A South Korean manufacturer states, "Our weapons don't sleep, like humans must. They can see in the dark, like humans can't. Our technology therefore plugs the gaps in human capability", and they want to "get to a place where our software can discern whether a target is friend, foe, civilian or military".
Trends:
According to Siemens, worldwide military spending on robotics was 5.1 billion USD in 2010 and 7.5 billion USD in 2015.
China became a top player in artificial intelligence research in the 2010s. According to the Financial Times, in 2016, for the first time, China published more AI papers than the entire European Union.
When restricted to number of AI papers in the top 5% of cited papers, China overtook the United States in 2016 but lagged behind the European Union. 23% of the researchers presenting at the 2017 American Association for the Advancement of Artificial Intelligence (AAAI) conference were Chinese. Eric Schmidt, the former chairman of Alphabet, has predicted China will be the leading country in AI by 2025.
Proposals for international regulation:
As early as 2007, scholars such as AI professor Noel Sharkey have warned of "an emerging arms race among the hi-tech nations to develop autonomous submarines, fighter jets, battleships and tanks that can find their own targets and apply violent force without the involvement of meaningful human decisions".
As early as 2014, AI specialists such as Steve Omohundro have been warning that "An autonomous weapons arms race is already taking place". Miles Brundage of the University of Oxford has argued an AI arms race might be somewhat mitigated through diplomacy: "We saw in the various historical arms races that collaboration and dialog can pay dividends".
Over a hundred experts signed an open letter in 2017 calling on the UN to address the issue of lethal autonomous weapons; however, at a November 2017 session of the UN Convention on Certain Conventional Weapons (CCW), diplomats could not agree even on how to define such weapons.
The Indian ambassador and chair of the CCW stated that agreement on rules remained a distant prospect. As of 2017, twenty-two countries have called for a full ban on lethal autonomous weapons.
Many experts believe attempts to completely ban killer robots are likely to fail. A 2017 report from Harvard's Belfer Center predicts that AI has the potential to be as transformative as nuclear weapons.
The report further argues that "Preventing expanded military use of AI is likely impossible" and that "the more modest goal of safe and effective technology management must be pursued", such as banning the attaching of an AI dead man's switch to a nuclear arsenal. Part of the impracticality is that detecting treaty violations would be extremely difficult.
Other reactions to autonomous weapons:
A 2015 open letter calling for the ban of lethal automated weapons systems has been signed by tens of thousands of citizens, including scholars such as the following:
Professor Noel Sharkey of the University of Sheffield has warned that autonomous weapons will inevitably fall into the hands of terrorist groups such as the Islamic State.
Disassociation:
Many Western tech companies are leery of being associated too closely with the U.S. military, for fear of losing access to China's market. Furthermore, some researchers, such as DeepMind's Demis Hassabis, are ideologically opposed to contributing to military work.
For example, Project Maven is a Pentagon project involving using machine learning and engineering talent to distinguish people and objects in drone videos, established in a memo by the U.S. Deputy Secretary of Defense on 26 April 2017.
Also known as the Algorithmic Warfare Cross Functional Team, it is, according to Lt. Gen. of the United States Air Force Jack Shanahan in November 2017, a project "designed to be that pilot project, that pathfinder, that spark that kindles the flame front of artificial intelligence across the rest of the [Defense] Department".
Its chief, U.S. Marine Corps Col. Drew Cukor, said: "People and computers will work symbiotically to increase the ability of weapon systems to detect objects." At the second Defense One Tech Summit in July 2017, Cukor also said that the investment in a "deliberate workflow process" was funded by the Department [of Defense] through its "rapid acquisition authorities" for about "the next 36 months".
In June 2018, company sources at Google said that top executive Diane Greene told staff that the company would not follow-up Project Maven after the current contract expires in March 2019.
Click here to see New York Times OpEd: "How A.I. Could Be Weaponized to Spread Disinformation" By Cade Metz and Scott Blumenthal of the New York Times June 7, 2019
Artificial Arms Race:
An artificial intelligence arms race is a competition between two or more states to have its military forces equipped with the best "artificial intelligence" (AI). Since the mid-2010s, many analysts have argued that a such a global arms race for better artificial intelligence has already begun.
Stances toward military artificial intelligence:
Russia:
Russian General Viktor Bondarev, commander-in-chief of the Russian air force, has stated that as early as February 2017, Russia has been working on AI-guided missiles that can decide to switch targets mid-flight.
Reports by state-sponsored Russian media on potential military uses of AI increased in mid-2017. In May 2017, the CEO of Russia's Kronstadt Group, a defense contractor, stated that "there already exist completely autonomous AI operation systems that provide the means for UAV clusters, when they fulfill missions autonomously, sharing tasks between them, and interact", and that it is inevitable that "swarms of drones" will one day fly over combat zones.
Russia has been testing several autonomous and semi-autonomous combat systems, such as Kalashnikov's "neural net" combat module, with a machine gun, a camera, and an AI that its makers claim can make its own targeting judgements without human intervention.
In September 2017, during a National Knowledge Day address to over a million students in 16,000 Russian schools, Russian President Vladimir Putin stated "Artificial intelligence is the future, not only for Russia but for all humankind... Whoever becomes the leader in this sphere will become the ruler of the world".
The Russian government has strongly rejected any ban on lethal autonomous weapons systems, suggesting that such a ban could be ignored.
China:
Further information: Artificial intelligence industry in China
According to a February 2019 report by Gregory C. Allen of the Center for a New American Security, "China’s leadership – including President Xi Jinping – believes that being at the forefront in AI technology is critical to the future of global military and economic power competition."
Chinese military officials have said that their goal is to incorporate commercial AI technology to "narrow the gap between the Chinese military and global advanced powers."
The close ties between Silicon Valley and China, and the open nature of the American research community, has made the West's most advanced AI technology easily available to China; in addition, Chinese industry has numerous home-grown AI accomplishments of its own, such as Baidu passing a notable Chinese-language speech recognition capability benchmark in 2015. As of 2017, Beijing's roadmap aims to create a $150 billion AI industry by 2030.
Before 2013, Chinese defense procurement was mainly restricted to a few conglomerates; however, as of 2017, China often sources sensitive emerging technology such as drones and artificial intelligence from private start-up companies.
One Chinese state has pledged to invest $5 billion in AI. Beijing has committed $2 billion to an AI development park. The Japan Times reported in 2018 that annual private Chinese investment in AI is under $7 billion per year. AI startups in China received nearly half of total global investment in AI startups in 2017; the Chinese filed for nearly five times as many AI patents as did Americans.
China published a position paper in 2016 questioning the adequacy of existing international law to address the eventuality of fully autonomous weapons, becoming the first permanent member of the U.N. Security Council to broach the issue.
United States:
In 2014, former Secretary of Defense Chuck Hagel posited the "Third Offset Strategy" that rapid advances in artificial intelligence will define the next generation of warfare. According to data science and analytics firm Govini, The U.S. Department of Defense increased investment in artificial intelligence, big data and cloud computing from $5.6 billion in 2011 to $7.4 billion in 2016. However, the civilian NSF budget for AI saw no increase in 2017.
The U.S. has many military AI combat programs, such as the Sea Hunter autonomous warship, which is designed to operate for extended periods at sea without a single crew member, and to even guide itself in and out of port. As of 2017, a temporary US Department of Defense directive requires a human operator to be kept in the loop when it comes to the taking of human life by autonomous weapons systems. Japan Times reported in 2018 that the United States private investment is around $70 billion per year.
United Kingdom:
In 2015, the UK government opposed a ban on lethal autonomous weapons, stating that "international humanitarian law already provides sufficient regulation for this area", but that all weapons employed by UK armed forces would be "under human oversight and control".
Israel:
Israel's Harpy anti-radar "fire and forget" drone is designed to be launched by ground troops, and autonomously fly over an area to find and destroy radar that fits pre-determined criteria.
South Korea:
The South Korean Super aEgis II machine gun, unveiled in 2010, sees use both in South Korea and in the Middle East. It can identify, track, and destroy a moving target at a range of 4 km.
While the technology can theoretically operate without human intervention, in practice safeguards are installed to require manual input. A South Korean manufacturer states, "Our weapons don't sleep, like humans must. They can see in the dark, like humans can't. Our technology therefore plugs the gaps in human capability", and they want to "get to a place where our software can discern whether a target is friend, foe, civilian or military".
Trends:
According to Siemens, worldwide military spending on robotics was 5.1 billion USD in 2010 and 7.5 billion USD in 2015.
China became a top player in artificial intelligence research in the 2010s. According to the Financial Times, in 2016, for the first time, China published more AI papers than the entire European Union.
When restricted to number of AI papers in the top 5% of cited papers, China overtook the United States in 2016 but lagged behind the European Union. 23% of the researchers presenting at the 2017 American Association for the Advancement of Artificial Intelligence (AAAI) conference were Chinese. Eric Schmidt, the former chairman of Alphabet, has predicted China will be the leading country in AI by 2025.
Proposals for international regulation:
As early as 2007, scholars such as AI professor Noel Sharkey have warned of "an emerging arms race among the hi-tech nations to develop autonomous submarines, fighter jets, battleships and tanks that can find their own targets and apply violent force without the involvement of meaningful human decisions".
As early as 2014, AI specialists such as Steve Omohundro have been warning that "An autonomous weapons arms race is already taking place". Miles Brundage of the University of Oxford has argued an AI arms race might be somewhat mitigated through diplomacy: "We saw in the various historical arms races that collaboration and dialog can pay dividends".
Over a hundred experts signed an open letter in 2017 calling on the UN to address the issue of lethal autonomous weapons; however, at a November 2017 session of the UN Convention on Certain Conventional Weapons (CCW), diplomats could not agree even on how to define such weapons.
The Indian ambassador and chair of the CCW stated that agreement on rules remained a distant prospect. As of 2017, twenty-two countries have called for a full ban on lethal autonomous weapons.
Many experts believe attempts to completely ban killer robots are likely to fail. A 2017 report from Harvard's Belfer Center predicts that AI has the potential to be as transformative as nuclear weapons.
The report further argues that "Preventing expanded military use of AI is likely impossible" and that "the more modest goal of safe and effective technology management must be pursued", such as banning the attaching of an AI dead man's switch to a nuclear arsenal. Part of the impracticality is that detecting treaty violations would be extremely difficult.
Other reactions to autonomous weapons:
A 2015 open letter calling for the ban of lethal automated weapons systems has been signed by tens of thousands of citizens, including scholars such as the following:
- physicist Stephen Hawking,
- Tesla magnate Elon Musk,
- and Apple's Steve Wozniak.
Professor Noel Sharkey of the University of Sheffield has warned that autonomous weapons will inevitably fall into the hands of terrorist groups such as the Islamic State.
Disassociation:
Many Western tech companies are leery of being associated too closely with the U.S. military, for fear of losing access to China's market. Furthermore, some researchers, such as DeepMind's Demis Hassabis, are ideologically opposed to contributing to military work.
For example, Project Maven is a Pentagon project involving using machine learning and engineering talent to distinguish people and objects in drone videos, established in a memo by the U.S. Deputy Secretary of Defense on 26 April 2017.
Also known as the Algorithmic Warfare Cross Functional Team, it is, according to Lt. Gen. of the United States Air Force Jack Shanahan in November 2017, a project "designed to be that pilot project, that pathfinder, that spark that kindles the flame front of artificial intelligence across the rest of the [Defense] Department".
Its chief, U.S. Marine Corps Col. Drew Cukor, said: "People and computers will work symbiotically to increase the ability of weapon systems to detect objects." At the second Defense One Tech Summit in July 2017, Cukor also said that the investment in a "deliberate workflow process" was funded by the Department [of Defense] through its "rapid acquisition authorities" for about "the next 36 months".
In June 2018, company sources at Google said that top executive Diane Greene told staff that the company would not follow-up Project Maven after the current contract expires in March 2019.
Military Technology, including its History
- YouTube Video: New technology makes troops invisible
- YouTube Video: US Military's latest technology 2018
- YouTube Video: Modern US Military Technologies Revelation
Description of above slide show covering new Military Technologies as reported by Kiplinger follows below:
"Cyberthreats are where much of the action is for today’s military, but war planners haven’t forgotten the need to keep up with traditional ways of enhancing America’s defense: weapons and the means to deliver them.
Here’s a glimpse of the next array of high-tech systems in development at companies and labs partnering with the Defense Advanced Research Projects Agency (DARPA), the science and weapons development arm of the Defense Department, as well as other research outfits.
Slide #1: Super-smart Cruise Missile: One of the Navy's next weapons, the Long Range Anti-Ship Missile, is an evolution of an existing idea, the cruise missile, but, boy, is it smarter. Cruise missiles were originally conceived to deliver a nuclear warhead deep inside the Soviet Union by flying a pre-planned route to specific coordinates. But the LRASM is all about flexibility and autonomy, designed to find and destroy a specific target in a crowded environment -- say, the South China Sea, for example. Its development by DARPA, in fact, was spurred by a request from the U.S. Pacific Command.
If a neutral ship gets in its path, the missile will fly over it. If a group of missiles is launched at a group of enemy ships, each will stick to its designated target — instead of, say, all missiles locking on the closest or largest ship.
Slide #2: Speedy, Stealthy Armored Vehicles: When it comes to military armored vehicles, the trend has been: Bigger is better. Where once soldiers traveled in Humvees, now they use hulking Mine-Resistant Ambush Protected vehicles (MRAPs). The price of protection has been the loss of speed and mobility. DARPA is hoping to shake things up with its Ground X-Vehicle Technologies program, which has tasked a range of companies to come up with vehicles whose priority is to avoid getting hit. The demanding list of criteria include:
Windows remain a weak point in armor, so some of the proposed designs do away with them. The future is in cameras and sensors that would support, in DARPA's words, "high-resolution, 360-degree visualization of data from multiple onboard sensors and technologies to support closed-cockpit vehicle operations." This program is relatively preliminary; DARPA is still seeking input.
Slide #3: Disappearing Devices: DARPA researchers are developing self-destructing electronic components, such as small polymer panels that sublimate directly from a solid phase to a gas phase, and electronics-bearing glass strips with high-stress inner anatomies that can be readily triggered to shatter into ultra-fine particles after use.
Why would anyone want such a thing? To prevent sensitive technologies from falling into the hands of an enemy, or — like unexploded ordnance — becoming an environmental hazard. A small drone could navigate unfamiliar territory, relay imagery back to both fighters on the ground and commanders a continent away, and then drop to earth with its design secrets nothing but useless dust.
The program is called Vanishing Programmable Resources (VAPR). DARPA has seen enough progress on this front that they've allocated additional money to take the concept of vanishing even further: to small delivery vehicles that could be air-dropped, bringing water, batteries or emergency medical supplies to the ground, and then disappear.
Slide #4: Making electricity while on march: On today's battlefield, ever more devices need electric power. This bionic device, known as PowerWalk, generates electricity from a fighter's own gait, power that can be used to recharge computers, radios, mobile phones and the like — and reduce the number of batteries that need to be carried into the field. That can free up space for other supplies, such as food, water, or ammunition.
Think of it as a wearable elliptical machine. The power demand is minimal when the wearer is raising his or her leg, but higher on the descending portion of the stride. While moving on a level surface, a user generates about 10 watts of electricity, which the PowerWalk’s designer, Vancouver-based Bionic Power, says is enough to charge as many as four smart phones in an hour. The PowerWalk doesn’t store any energy itself, but passes it on to the soldier’s electronics that need the juice.
The Army Natick Soldier Research, Development and Engineering Center in Massachusetts will be field-testing the devices this year.
Slide #5: An Aircraft Carrier for Drones (Minus the Ship): Drones are where all the action is in the air these days. But as many people who got one for the holidays can tell you, it's one thing to fly a drone but another entirely to land one safely.
The military has the same problem, particularly among horizontally flying drones (think airplane rather than helicopter) that it wants to launch and capture without a proper runway, whether out in the field or at sea. Currently, smaller drones are often retrieved using nets, a hard "landing" that can stress the drone, and some are simply not retrieved and written off.
The DARPA-funded SideArm project is meant to do away with catching unmanned aerial systems (military-speak for drones) like butterflies, using instead a catapult-and-hook system whose operating principles mimic the rapid-fire takeoff and recovery of combat aircraft from aircraft carriers.
Unlike those massive ships, the SideArm is small enough to fit in a standard 20-foot shipping container, and can be mounted on a ship or a truck, or just sit right on the ground. In recent testing with Aurora Flight Sciences of Manassas, Va., SideArm was able to snag a 400-pound Lockheed Martin Fury UAS, and data from the test showed the system should be capable of catching a drone weighing up to 1,100 pounds.
Slide #6: An Aircraft Carrier for Drones in the Sky: Even more ambitious, when it comes to launching and retrieving drones, is DARPA's Gremlins program, which envisions low-cost, reusable unmanned aerial systems that could be dropped by a variety of aircraft (even another drone!), do their work, then return to another plane for airborne recovery.
One of the hoped-for upsides of this complicated aerial ballet is the ability to reuse the drone (about 20 uses is envisioned). Currently, the military often relies on expendable unmanned systems for this sort of work. Those drones don't come home from their missions, even if they've survived their environment.
DARPA has awarded research contracts to two teams, one led by Dynetics Inc. of Huntsville, Al., and one by General Atomics Aeronautical Systems Inc. of San Diego, and flight tests are envisioned in 2019.
Slide #7: VTOL Experimental Plane program: Vertical-takeoff airplanes have been built — the best known is probably the Marines’ V-22 Osprey, which can shift its giant blades from working like helicopter rotors for liftoff and landing to propellers for fast horizontal flight when flying troops and equipment in and out of battle.
But the Osprey’s design dates to the early 1980s (it had a long, controversial development), and DARPA is already thinking about an improved version, via the VTOL Experimental Plane program, which calls for a craft that’s faster, performs better in a hover and carries more payload.
The program is already in phase 2, which means a design contract has been awarded to Aurora Flight Sciences. Aurora’s craft, dubbed the XV-24A, uses the turboshaft engine from the V-22 (but only one) to generate 3 megawatts of electricity, the equivalent of an average commercial wind turbine. That, in turn, would power ducted fans in the aircrafts’ wings, which could rotate: vertical for hovering, horizontal for flying forward. Aurora has flown a scale model (see image inset), but DARPA acknowledges that volume production remains a long way off.
___________________________________________________________________________
Military Technology:
Military technology is the application of technology for use in warfare. It comprises the kinds of technology that are distinctly military in nature and not civilian in application, usually because they lack useful or legal civilian applications, or are dangerous to use without appropriate military training.
The line is porous; military inventions have been brought into civilian use throughout history, with sometimes minor modification if any, and civilian innovations have similarly been put to military use.
Military technology is often researched and developed by scientists and engineers specifically for use in battle by the armed forces. Many new technologies came as a result of the military funding of science.
Weapons engineering is the design, development, testing and lifecycle management of military weapons and systems. It draws on the knowledge of several traditional engineering disciplines, including the following disciplines:
Click on any of the following blue hyperlinks for more about Military Technology:
History of Military Technology:
The military funding of science has had a powerful transformative effect on the practice and products of scientific research since the early 20th century. Particularly since World War I, advanced science-based technologies have been viewed as essential elements of a successful military.
World War I is often called "the chemists’ war", both for the extensive use of poison gas and the importance of nitrates and advanced high explosives. Poison gas, beginning in 1915 with chlorine from the powerful German dye industry, was used extensively by the Germans and the British; over the course of the war, scientists on both sides raced to develop more and more potent chemicals and devise countermeasures against the newest enemy gases.
Physicists also contributed to the war effort, developing wireless communication technologies and sound-based methods of detecting U-boats, resulting in the first tenuous long-term connections between academic science and the military.
World War II marked a massive increase in the military funding of science, particularly physics. In addition to the Manhattan Project and the resulting atomic bomb, British and American work on radar was widespread and ultimately highly influential in the course of the war; radar enabled detection of enemy ships and aircraft, as well as the radar-based proximity fuze.
Mathematical cryptography, meteorology, and rocket science were also central to the war effort, with military-funded wartime advances having a significant long-term effect on each discipline. The technologies employed at the end--jet aircraft, radar and proximity fuzes, and the atomic bomb—were radically different from pre-war technology; military leaders came to view continued advances in technology as the critical element for success in future wars.
The advent of the Cold War solidified the links between military institutions and academic science, particularly in the United States and the Soviet Union, so that even during a period of nominal peace military funding continued to expand. Funding spread to the social sciences as well as the natural sciences, and whole new fields, such as digital computing, were born of military patronage.
Following the end of the Cold War and the dissolution of the Soviet Union, military funding of science has decreased substantially, but much of the American military-scientific complex remains in place.
The sheer scale of military funding for science since World War II has instigated a large body of historical literature analyzing the effects of that funding, especially for American science.
Since Paul Forman’s 1987 article “Behind quantum electronics: National security as a basis for physical research in the United State, 1940-1960,” there has been an ongoing historical debate over precisely how and to what extent military funding affected the course of scientific research and discovery.
Forman and others have argued that military funding fundamentally redirected science—particularly physics—toward applied research, and that military technologies predominantly formed the basis for subsequent research even in areas of basic science; ultimately the very culture and ideals of science were colored by extensive collaboration between scientists and military planners.
An alternate view has been presented by Daniel Kevles, that while military funding provided many new opportunities for scientists and dramatically expanded the scope of physical research, scientists by-and-large retained their intellectual autonomy.
Click on any of the following blue hyperlinks for more about the History of Military Technology:
"Cyberthreats are where much of the action is for today’s military, but war planners haven’t forgotten the need to keep up with traditional ways of enhancing America’s defense: weapons and the means to deliver them.
Here’s a glimpse of the next array of high-tech systems in development at companies and labs partnering with the Defense Advanced Research Projects Agency (DARPA), the science and weapons development arm of the Defense Department, as well as other research outfits.
Slide #1: Super-smart Cruise Missile: One of the Navy's next weapons, the Long Range Anti-Ship Missile, is an evolution of an existing idea, the cruise missile, but, boy, is it smarter. Cruise missiles were originally conceived to deliver a nuclear warhead deep inside the Soviet Union by flying a pre-planned route to specific coordinates. But the LRASM is all about flexibility and autonomy, designed to find and destroy a specific target in a crowded environment -- say, the South China Sea, for example. Its development by DARPA, in fact, was spurred by a request from the U.S. Pacific Command.
If a neutral ship gets in its path, the missile will fly over it. If a group of missiles is launched at a group of enemy ships, each will stick to its designated target — instead of, say, all missiles locking on the closest or largest ship.
Slide #2: Speedy, Stealthy Armored Vehicles: When it comes to military armored vehicles, the trend has been: Bigger is better. Where once soldiers traveled in Humvees, now they use hulking Mine-Resistant Ambush Protected vehicles (MRAPs). The price of protection has been the loss of speed and mobility. DARPA is hoping to shake things up with its Ground X-Vehicle Technologies program, which has tasked a range of companies to come up with vehicles whose priority is to avoid getting hit. The demanding list of criteria include:
- Reduce vehicle size and weight by 50 percent
- Reduce onboard crew needed to operate vehicle by 50 percent
- Increase vehicle speed by 100 percent
- Access 95 percent of terrain
Windows remain a weak point in armor, so some of the proposed designs do away with them. The future is in cameras and sensors that would support, in DARPA's words, "high-resolution, 360-degree visualization of data from multiple onboard sensors and technologies to support closed-cockpit vehicle operations." This program is relatively preliminary; DARPA is still seeking input.
Slide #3: Disappearing Devices: DARPA researchers are developing self-destructing electronic components, such as small polymer panels that sublimate directly from a solid phase to a gas phase, and electronics-bearing glass strips with high-stress inner anatomies that can be readily triggered to shatter into ultra-fine particles after use.
Why would anyone want such a thing? To prevent sensitive technologies from falling into the hands of an enemy, or — like unexploded ordnance — becoming an environmental hazard. A small drone could navigate unfamiliar territory, relay imagery back to both fighters on the ground and commanders a continent away, and then drop to earth with its design secrets nothing but useless dust.
The program is called Vanishing Programmable Resources (VAPR). DARPA has seen enough progress on this front that they've allocated additional money to take the concept of vanishing even further: to small delivery vehicles that could be air-dropped, bringing water, batteries or emergency medical supplies to the ground, and then disappear.
Slide #4: Making electricity while on march: On today's battlefield, ever more devices need electric power. This bionic device, known as PowerWalk, generates electricity from a fighter's own gait, power that can be used to recharge computers, radios, mobile phones and the like — and reduce the number of batteries that need to be carried into the field. That can free up space for other supplies, such as food, water, or ammunition.
Think of it as a wearable elliptical machine. The power demand is minimal when the wearer is raising his or her leg, but higher on the descending portion of the stride. While moving on a level surface, a user generates about 10 watts of electricity, which the PowerWalk’s designer, Vancouver-based Bionic Power, says is enough to charge as many as four smart phones in an hour. The PowerWalk doesn’t store any energy itself, but passes it on to the soldier’s electronics that need the juice.
The Army Natick Soldier Research, Development and Engineering Center in Massachusetts will be field-testing the devices this year.
Slide #5: An Aircraft Carrier for Drones (Minus the Ship): Drones are where all the action is in the air these days. But as many people who got one for the holidays can tell you, it's one thing to fly a drone but another entirely to land one safely.
The military has the same problem, particularly among horizontally flying drones (think airplane rather than helicopter) that it wants to launch and capture without a proper runway, whether out in the field or at sea. Currently, smaller drones are often retrieved using nets, a hard "landing" that can stress the drone, and some are simply not retrieved and written off.
The DARPA-funded SideArm project is meant to do away with catching unmanned aerial systems (military-speak for drones) like butterflies, using instead a catapult-and-hook system whose operating principles mimic the rapid-fire takeoff and recovery of combat aircraft from aircraft carriers.
Unlike those massive ships, the SideArm is small enough to fit in a standard 20-foot shipping container, and can be mounted on a ship or a truck, or just sit right on the ground. In recent testing with Aurora Flight Sciences of Manassas, Va., SideArm was able to snag a 400-pound Lockheed Martin Fury UAS, and data from the test showed the system should be capable of catching a drone weighing up to 1,100 pounds.
Slide #6: An Aircraft Carrier for Drones in the Sky: Even more ambitious, when it comes to launching and retrieving drones, is DARPA's Gremlins program, which envisions low-cost, reusable unmanned aerial systems that could be dropped by a variety of aircraft (even another drone!), do their work, then return to another plane for airborne recovery.
One of the hoped-for upsides of this complicated aerial ballet is the ability to reuse the drone (about 20 uses is envisioned). Currently, the military often relies on expendable unmanned systems for this sort of work. Those drones don't come home from their missions, even if they've survived their environment.
DARPA has awarded research contracts to two teams, one led by Dynetics Inc. of Huntsville, Al., and one by General Atomics Aeronautical Systems Inc. of San Diego, and flight tests are envisioned in 2019.
Slide #7: VTOL Experimental Plane program: Vertical-takeoff airplanes have been built — the best known is probably the Marines’ V-22 Osprey, which can shift its giant blades from working like helicopter rotors for liftoff and landing to propellers for fast horizontal flight when flying troops and equipment in and out of battle.
But the Osprey’s design dates to the early 1980s (it had a long, controversial development), and DARPA is already thinking about an improved version, via the VTOL Experimental Plane program, which calls for a craft that’s faster, performs better in a hover and carries more payload.
The program is already in phase 2, which means a design contract has been awarded to Aurora Flight Sciences. Aurora’s craft, dubbed the XV-24A, uses the turboshaft engine from the V-22 (but only one) to generate 3 megawatts of electricity, the equivalent of an average commercial wind turbine. That, in turn, would power ducted fans in the aircrafts’ wings, which could rotate: vertical for hovering, horizontal for flying forward. Aurora has flown a scale model (see image inset), but DARPA acknowledges that volume production remains a long way off.
___________________________________________________________________________
Military Technology:
Military technology is the application of technology for use in warfare. It comprises the kinds of technology that are distinctly military in nature and not civilian in application, usually because they lack useful or legal civilian applications, or are dangerous to use without appropriate military training.
The line is porous; military inventions have been brought into civilian use throughout history, with sometimes minor modification if any, and civilian innovations have similarly been put to military use.
Military technology is often researched and developed by scientists and engineers specifically for use in battle by the armed forces. Many new technologies came as a result of the military funding of science.
Weapons engineering is the design, development, testing and lifecycle management of military weapons and systems. It draws on the knowledge of several traditional engineering disciplines, including the following disciplines:
- mechanical engineering,
- electrical engineering,
- mechatronics,
- electro-optics,
- aerospace engineering,
- materials engineering,
- and chemical engineering.
Click on any of the following blue hyperlinks for more about Military Technology:
- History: See "History of Military Technology" below
- Modern technology
- Postmodern technology
- Future technology
History of Military Technology:
The military funding of science has had a powerful transformative effect on the practice and products of scientific research since the early 20th century. Particularly since World War I, advanced science-based technologies have been viewed as essential elements of a successful military.
World War I is often called "the chemists’ war", both for the extensive use of poison gas and the importance of nitrates and advanced high explosives. Poison gas, beginning in 1915 with chlorine from the powerful German dye industry, was used extensively by the Germans and the British; over the course of the war, scientists on both sides raced to develop more and more potent chemicals and devise countermeasures against the newest enemy gases.
Physicists also contributed to the war effort, developing wireless communication technologies and sound-based methods of detecting U-boats, resulting in the first tenuous long-term connections between academic science and the military.
World War II marked a massive increase in the military funding of science, particularly physics. In addition to the Manhattan Project and the resulting atomic bomb, British and American work on radar was widespread and ultimately highly influential in the course of the war; radar enabled detection of enemy ships and aircraft, as well as the radar-based proximity fuze.
Mathematical cryptography, meteorology, and rocket science were also central to the war effort, with military-funded wartime advances having a significant long-term effect on each discipline. The technologies employed at the end--jet aircraft, radar and proximity fuzes, and the atomic bomb—were radically different from pre-war technology; military leaders came to view continued advances in technology as the critical element for success in future wars.
The advent of the Cold War solidified the links between military institutions and academic science, particularly in the United States and the Soviet Union, so that even during a period of nominal peace military funding continued to expand. Funding spread to the social sciences as well as the natural sciences, and whole new fields, such as digital computing, were born of military patronage.
Following the end of the Cold War and the dissolution of the Soviet Union, military funding of science has decreased substantially, but much of the American military-scientific complex remains in place.
The sheer scale of military funding for science since World War II has instigated a large body of historical literature analyzing the effects of that funding, especially for American science.
Since Paul Forman’s 1987 article “Behind quantum electronics: National security as a basis for physical research in the United State, 1940-1960,” there has been an ongoing historical debate over precisely how and to what extent military funding affected the course of scientific research and discovery.
Forman and others have argued that military funding fundamentally redirected science—particularly physics—toward applied research, and that military technologies predominantly formed the basis for subsequent research even in areas of basic science; ultimately the very culture and ideals of science were colored by extensive collaboration between scientists and military planners.
An alternate view has been presented by Daniel Kevles, that while military funding provided many new opportunities for scientists and dramatically expanded the scope of physical research, scientists by-and-large retained their intellectual autonomy.
Click on any of the following blue hyperlinks for more about the History of Military Technology:
- Science and military technology before the modern era
- World War I and the interwar years
- World War II
- American Cold War science
- Historical debate
- See also:
Cyberwarfare, focusing specifically on Cyberwarfare in the United States
TOP: Cyberwarfare: FBI undercover operation exposing cyberwarfare.
BOTTOM: Some of the types of attacks that have been, or could be, used in cyberwarfare.
- YouTube Video: US Military Keeping Secrets From Trump
- YouTube Video: Top 5 Ways to Prevent a Cyber Attack
- YouTube Video: How Hackers Really Crack Your Passwords
TOP: Cyberwarfare: FBI undercover operation exposing cyberwarfare.
BOTTOM: Some of the types of attacks that have been, or could be, used in cyberwarfare.
Cyberwarfare involves the battlespace use and targeting of computers and networks in warfare. It involves both offensive and defensive operations pertaining to the threat of cyberattacks, espionage and sabotage. There has been controversy over whether such operations can duly be called "war". Nevertheless, nations have been developing their capabilities and engaged in cyberwarfare either as an aggressor, defendant, or both.
Cyberwarfare has been defined as "actions by a nation-state to penetrate another nation's computers or networks for the purposes of causing damage or disruption", but other definitions also include non-state actors, such as terrorist groups, companies, political or ideological extremist groups, hacktivists, and transnational criminal organizations.
Some governments have made it an integral part of their overall military strategy, with some having invested heavily in cyberwarfare capability. Cyberwarfare is essentially a formalized version of penetration testing in which a government entity has established it as a war-fighting capability.
This capability uses the same set of penetration testing methodologies but applies them, in the case of United States doctrine, in a strategical way to
Types of Threats:
Espionage:
Traditional espionage is not an act of war, nor is cyber-espionage, and both are generally assumed to be ongoing between major powers. Despite this assumption, some incidents can cause serious tensions between nations, and are often described as "attacks". For example:
Sabotage:
Computers and satellites that coordinate other activities are vulnerable components of a system and could lead to the disruption of equipment. Compromise of military systems, such as C4ISTAR components that are responsible for orders and communications could lead to their interception or malicious replacement.
Power, water, fuel, communications, and transportation infrastructure all may be vulnerable to disruption. According to Clarke, the civilian realm is also at risk, noting that the security breaches have already gone beyond stolen credit card numbers, and that potential targets can also include the electric power grid, trains, or the stock market.
In mid July 2010, security experts discovered a malicious software program called Stuxnet that had infiltrated factory computers and had spread to plants around the world. It is considered "the first attack on critical industrial infrastructure that sits at the foundation of modern economies," notes The New York Times.
Stuxnet, while extremely effective in delaying Iran's nuclear program for the development of nuclear weaponry, came at a high cost. For the first time, it became clear that not only could cyber weapons be defensive but they could be offensive.
The large decentralization and scale of cyberspace makes it extremely difficult to direct from a policy perspective. Non-state actors can play as large a part in the cyberwar space as state actors, which leads to dangerous, sometimes disastrous, consequences.
Small groups of highly skilled malware developers are able to as effectively impact global politics and cyber warfare as large governmental agencies. A major aspect of this ability lies in the willingness of these groups to share their exploits and developments on the web as a form of arms proliferation.
This allows lesser hackers to become more proficient in creating the large scale attacks that once only a small handful were skillful enough to manage. In addition, thriving black markets for these kinds of cyber weapons are buying and selling these cyber capabilities to the highest bidder without regard for consequences.
Denial-of-Service Attack:
Main article: Denial-of-service attack
In computing, a denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a machine or network resource unavailable to its intended users. Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers. DoS attacks may not be limited to computer-based methods, as strategic physical attacks against infrastructure can be just as devastating.
For example, cutting undersea communication cables may severely cripple some regions and countries with regards to their information warfare ability.
Electrical Power Grid:
The federal government of the United States admits that the electric power grid is susceptible to cyberwarfare. The United States Department of Homeland Security works with industries to identify vulnerabilities and to help industries enhance the security of control system networks, the federal government is also working to ensure that security is built in as the next generation of "smart grid" networks are developed.
In April 2009, reports surfaced that China and Russia had infiltrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national security officials. The North American Electric Reliability Corporation (NERC) has issued a public notice that warns that the electrical grid is not adequately protected from cyber attack. China denies intruding into the U.S. electrical grid.
One countermeasure would be to disconnect the power grid from the Internet and run the net with droop speed control only. Massive power outages caused by a cyber attack could disrupt the economy, distract from a simultaneous military attack, or create a national trauma.
Howard Schmidt, former Cyber-Security Coordinator of the US, commented on those possibilities: "It's possible that hackers have gotten into administrative computer systems of utility companies, but says those aren't linked to the equipment controlling the grid, at least not in developed countries. [Schmidt] has never heard that the grid itself has been hacked.
On 23 December 2015, what is believed to be a first known successful cyber attack on a power grid took place in Ukraine leading to temporary blackouts. The cyber attack is attributed to the Russian advanced persistent threat group called "Sandworm" and it was performed during an ongoing military confrontation.
Click on any of the following blue hyperlinks for more about Cyberwarfare:
Cyberwarfare in the United States:
As a major developed economy, the United States is highly dependent on the Internet and therefore greatly exposed to cyber attacks. At the same time, the United States has substantial capabilities in both defense and power projection thanks to its advanced technology and large military budget.
Cyber warfare continues to be a growing threat as more physical systems and infrastructure are linked to the internet. Malicious hacking from domestic or foreign enemies remains a constant threat to the United States. In response to these growing threats, the United States has developed significant cyber capabilities.
The United States Department of Defense recognizes the use of computers and the Internet to conduct warfare in cyberspace as a threat to national security, but also as a platform for attack.
The United States Cyber Command centralizes command of cyberspace operations, organizes existing cyber resources and synchronizes defense of U.S. military networks. It is an armed forces sub-unified command subordinate to United States Strategic Command.
In April 2015, the U.S. Department of Defense (DoD) published its latest Cyber Strategy building upon the previous DoD Strategy for Operating in Cyberspace published in July 2011.
The DoD Cyber strategy focuses on building capabilities to protect, secure, and defend its own DoD networks, systems and information; defend the nation against cyber attacks; and support contingency plans. This includes being prepared to operate and continue to carry out missions in environments impacted by cyber attacks.
The DoD outlines three cyber missions:
In addition the Cyber Strategy emphasizes the need to build bridges to the private sector, so that the best talent and technology the United States has to offer is at disposal to the DoD.
The Five Pillars:
US Department of Defense Cyber Strategy, US DoD, April 2015.The five pillars is the base of the Department of Defense's strategy for cyberwarfare.
The first pillar is to recognize that the new domain for warfare is cyberspace and that it is similar to the other elements in the battlespace. The key objectives of this pillar is to build up technical capabilities and accelerate research and development to provide the United States with a technological advantage.
The second pillar is proactive defenses as opposed to passive defense. Two examples of passive defense are computer hygiene and firewalls. The balance of the attacks require active defense using sensors to provide a rapid response to detect and stop a cyber attack on a computer network. This would provide military tactics to backtrace, hunt down and attack an enemy intruder.
The third pillar is critical infrastructure protection (CIP) to ensure the protection of critical infrastructure by developing warning systems to anticipate threats.
The fourth pillar is the use of collective defense which would provide the ability of early detection, and to incorporate it into the cyberwarfare defense structure. The goal of this pillar being to explore all options in the face of a conflict, and to minimize loss of life and destruction of property.
The fifth pillar is build and maintain international alliances and partnerships to deter shared threats, and to remain adaptive and flexible to build new alliances as required. This is focused on "priority regions, to include the Middle East, Asia-Pacific, and Europe"
Cyber Attack as an Act of War:
In 2011, The White House published an "International Strategy for Cyberspace" that reserved the right to use military force in response to a cyberattack:
"When warranted, the United States will respond to hostile acts in cyberspace as we would to any other threat to our country. We reserve the right to use all necessary means — diplomatic, informational, military, and economic — as appropriate and consistent with applicable international law, in order to defend our Nation, our allies, our partners, and our interests. In so doing, we will exhaust all options before military force whenever we can; will carefully weigh the costs and risks of action against the costs of inaction; and will act in a way that reflects our values and strengthens our legitimacy, seeking broad international support whenever possible."
In 2013, the Defense Science Board, an independent advisory committee to the U.S. Secretary of Defense, went further, stating that "The cyber threat is serious, with potential consequences similar in some ways to the nuclear threat of the Cold War," and recommending, in response to the "most extreme case" (described as a "catastrophic full spectrum cyber attack"), that "Nuclear weapons would remain the ultimate response and anchor the deterrence ladder."
Click on any of the following blue hyperlinks for more about Cyberwarfare in the United States:
Cyberwarfare has been defined as "actions by a nation-state to penetrate another nation's computers or networks for the purposes of causing damage or disruption", but other definitions also include non-state actors, such as terrorist groups, companies, political or ideological extremist groups, hacktivists, and transnational criminal organizations.
Some governments have made it an integral part of their overall military strategy, with some having invested heavily in cyberwarfare capability. Cyberwarfare is essentially a formalized version of penetration testing in which a government entity has established it as a war-fighting capability.
This capability uses the same set of penetration testing methodologies but applies them, in the case of United States doctrine, in a strategical way to
- Prevent cyber attacks against critical infrastructure
- Reduce national vulnerability to cyber attacks
- Minimize damage and recovery time from cyber attacks
Types of Threats:
- Cyberattacks, where immediate damage or disruption is caused are the main concern.
- Cyber espionage, which can provide the information needed to make a successful cyberattack or scandal to launch an information warfare.
Espionage:
Traditional espionage is not an act of war, nor is cyber-espionage, and both are generally assumed to be ongoing between major powers. Despite this assumption, some incidents can cause serious tensions between nations, and are often described as "attacks". For example:
- Massive spying by the US on many countries, revealed by Edward Snowden.
- After the NSA's spying on Germany's Chancellor Angela Merkel was revealed, the Chancellor compared the NSA with the Stasi.
- The NSA recording nearly every cell phone conversation in the Bahamas, without the Bahamian government's permission, and similar programs in Kenya, the Philippines, Mexico and Afghanistan.
- The "Titan Rain" probes of American defense contractors computer systems since 2003.
- The Office of Personnel Management data breach, in the US, widely attributed to China.
Sabotage:
Computers and satellites that coordinate other activities are vulnerable components of a system and could lead to the disruption of equipment. Compromise of military systems, such as C4ISTAR components that are responsible for orders and communications could lead to their interception or malicious replacement.
Power, water, fuel, communications, and transportation infrastructure all may be vulnerable to disruption. According to Clarke, the civilian realm is also at risk, noting that the security breaches have already gone beyond stolen credit card numbers, and that potential targets can also include the electric power grid, trains, or the stock market.
In mid July 2010, security experts discovered a malicious software program called Stuxnet that had infiltrated factory computers and had spread to plants around the world. It is considered "the first attack on critical industrial infrastructure that sits at the foundation of modern economies," notes The New York Times.
Stuxnet, while extremely effective in delaying Iran's nuclear program for the development of nuclear weaponry, came at a high cost. For the first time, it became clear that not only could cyber weapons be defensive but they could be offensive.
The large decentralization and scale of cyberspace makes it extremely difficult to direct from a policy perspective. Non-state actors can play as large a part in the cyberwar space as state actors, which leads to dangerous, sometimes disastrous, consequences.
Small groups of highly skilled malware developers are able to as effectively impact global politics and cyber warfare as large governmental agencies. A major aspect of this ability lies in the willingness of these groups to share their exploits and developments on the web as a form of arms proliferation.
This allows lesser hackers to become more proficient in creating the large scale attacks that once only a small handful were skillful enough to manage. In addition, thriving black markets for these kinds of cyber weapons are buying and selling these cyber capabilities to the highest bidder without regard for consequences.
Denial-of-Service Attack:
Main article: Denial-of-service attack
In computing, a denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a machine or network resource unavailable to its intended users. Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers. DoS attacks may not be limited to computer-based methods, as strategic physical attacks against infrastructure can be just as devastating.
For example, cutting undersea communication cables may severely cripple some regions and countries with regards to their information warfare ability.
Electrical Power Grid:
The federal government of the United States admits that the electric power grid is susceptible to cyberwarfare. The United States Department of Homeland Security works with industries to identify vulnerabilities and to help industries enhance the security of control system networks, the federal government is also working to ensure that security is built in as the next generation of "smart grid" networks are developed.
In April 2009, reports surfaced that China and Russia had infiltrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national security officials. The North American Electric Reliability Corporation (NERC) has issued a public notice that warns that the electrical grid is not adequately protected from cyber attack. China denies intruding into the U.S. electrical grid.
One countermeasure would be to disconnect the power grid from the Internet and run the net with droop speed control only. Massive power outages caused by a cyber attack could disrupt the economy, distract from a simultaneous military attack, or create a national trauma.
Howard Schmidt, former Cyber-Security Coordinator of the US, commented on those possibilities: "It's possible that hackers have gotten into administrative computer systems of utility companies, but says those aren't linked to the equipment controlling the grid, at least not in developed countries. [Schmidt] has never heard that the grid itself has been hacked.
On 23 December 2015, what is believed to be a first known successful cyber attack on a power grid took place in Ukraine leading to temporary blackouts. The cyber attack is attributed to the Russian advanced persistent threat group called "Sandworm" and it was performed during an ongoing military confrontation.
Click on any of the following blue hyperlinks for more about Cyberwarfare:
- Motivations
- By region
- Cyberpeace
- Cyber counterintelligence
- Controversy over terms
- Legality, rules
- In films
- See also:
- Cash machine
- Computer security organizations
- Cyber-arms industry
- Cyber-collection
- Cyber spying
- Cyber terrorism
- Duqu
- Fifth Dimension Operations
- IT risk
- iWar
- List of cyber attack threat trends
- List of cyber-attacks
- Penetration test
- Proactive cyber defense
- Signals intelligence
- Virtual war
- United States Cyber Command
- NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE)
- Cyberwar News community by Reza Rafati
- Videos
- "Sabotaging the System" video, "60 Minutes", 8 November 2009, CBS News, 15 minutes
- Articles
- ABC: Former White House security advisor warns of cyber war
- Wall Street Journal: Fighting Wars in Cyberspace
- Will There Be An Electronic Pearl Harbor, PC World by Ira Winkler, 1 December 2009
- Senate panel: 80 percent of cyberattacks preventable, Wired, 17 November 2009
- Duncan Gardham, 26 June 2009, Hackers recruited to fight 'new cold war', Telegraph UK
- Stefano Mele, Jan 2016, Cyber Strategy & Policy Brief (Volume 01 – January 2016)
- Stefano Mele, Jun 2013, Cyber-Weapons: Legal and Strategic Aspects (version 2.0)
- Stefano Mele, Sep 2010, Cyberwarfare and its damaging effects on citizens
- Cybersecurity: Authoritative Reports and Resources, US Congressional Research Service
- Why the USA is Losing The Cyberwar Against China, by Joseph Steinberg, VentureBeat, 9 November 2011
- Michael Riley and Ashlee Vance, 20 July 2011, Cyber Weapons: The New Arms Race
- The Digital Arms Race: NSA Preps America for Future Battle, Der Spiegel, January 2015
Cyberwarfare in the United States:
As a major developed economy, the United States is highly dependent on the Internet and therefore greatly exposed to cyber attacks. At the same time, the United States has substantial capabilities in both defense and power projection thanks to its advanced technology and large military budget.
Cyber warfare continues to be a growing threat as more physical systems and infrastructure are linked to the internet. Malicious hacking from domestic or foreign enemies remains a constant threat to the United States. In response to these growing threats, the United States has developed significant cyber capabilities.
The United States Department of Defense recognizes the use of computers and the Internet to conduct warfare in cyberspace as a threat to national security, but also as a platform for attack.
The United States Cyber Command centralizes command of cyberspace operations, organizes existing cyber resources and synchronizes defense of U.S. military networks. It is an armed forces sub-unified command subordinate to United States Strategic Command.
In April 2015, the U.S. Department of Defense (DoD) published its latest Cyber Strategy building upon the previous DoD Strategy for Operating in Cyberspace published in July 2011.
The DoD Cyber strategy focuses on building capabilities to protect, secure, and defend its own DoD networks, systems and information; defend the nation against cyber attacks; and support contingency plans. This includes being prepared to operate and continue to carry out missions in environments impacted by cyber attacks.
The DoD outlines three cyber missions:
- Defend DoD networks, systems, and information.
- Defend the United States and its interests against cyberattacks of significant consequence.
- Provide integrated cyber capabilities to support military operations and contingency plans.
In addition the Cyber Strategy emphasizes the need to build bridges to the private sector, so that the best talent and technology the United States has to offer is at disposal to the DoD.
The Five Pillars:
- Build and maintain ready forces and capabilities to conduct cyberspace operations;
- Defend the DoD information network, secure DoD data, and mitigate risks to DoD missions;
- Be prepared to defend the U.S. homeland and U.S. vital interests from disruptive or destructive cyberattacks of significant consequence;
- Build and maintain viable cyber options and plan to use those options to control conflict escalation and to shape the conflict environment at all stages;
- Build and maintain robust international alliances and partnerships to deter shared threats and increase international security and stability.
US Department of Defense Cyber Strategy, US DoD, April 2015.The five pillars is the base of the Department of Defense's strategy for cyberwarfare.
The first pillar is to recognize that the new domain for warfare is cyberspace and that it is similar to the other elements in the battlespace. The key objectives of this pillar is to build up technical capabilities and accelerate research and development to provide the United States with a technological advantage.
The second pillar is proactive defenses as opposed to passive defense. Two examples of passive defense are computer hygiene and firewalls. The balance of the attacks require active defense using sensors to provide a rapid response to detect and stop a cyber attack on a computer network. This would provide military tactics to backtrace, hunt down and attack an enemy intruder.
The third pillar is critical infrastructure protection (CIP) to ensure the protection of critical infrastructure by developing warning systems to anticipate threats.
The fourth pillar is the use of collective defense which would provide the ability of early detection, and to incorporate it into the cyberwarfare defense structure. The goal of this pillar being to explore all options in the face of a conflict, and to minimize loss of life and destruction of property.
The fifth pillar is build and maintain international alliances and partnerships to deter shared threats, and to remain adaptive and flexible to build new alliances as required. This is focused on "priority regions, to include the Middle East, Asia-Pacific, and Europe"
Cyber Attack as an Act of War:
In 2011, The White House published an "International Strategy for Cyberspace" that reserved the right to use military force in response to a cyberattack:
"When warranted, the United States will respond to hostile acts in cyberspace as we would to any other threat to our country. We reserve the right to use all necessary means — diplomatic, informational, military, and economic — as appropriate and consistent with applicable international law, in order to defend our Nation, our allies, our partners, and our interests. In so doing, we will exhaust all options before military force whenever we can; will carefully weigh the costs and risks of action against the costs of inaction; and will act in a way that reflects our values and strengthens our legitimacy, seeking broad international support whenever possible."
In 2013, the Defense Science Board, an independent advisory committee to the U.S. Secretary of Defense, went further, stating that "The cyber threat is serious, with potential consequences similar in some ways to the nuclear threat of the Cold War," and recommending, in response to the "most extreme case" (described as a "catastrophic full spectrum cyber attack"), that "Nuclear weapons would remain the ultimate response and anchor the deterrence ladder."
Click on any of the following blue hyperlinks for more about Cyberwarfare in the United States:
- Attacks on other nations
- Cyber threat information sharing
- United States Cyber Command
- Timeline of Cyber Warfare Attacks against the United States
- See also:
- Air Force Cyber Command (Provisional)
- Computer Security
- Cyber spying
- Cyber terrorism
- Cyberwarfare by Russian state
- Defense Information Systems Network
- Denial-of-service attack
- Electronic warfare
- Espionage
- Hacker (computer security)
- iWar
- Information warfare
- List of cyber attack threat trends
- Penetration testing
- Proactive Cyber Defense
- Siberian pipeline sabotage
- Signals intelligence
- Chinese Intelligence Operations in the United States
- Chinese Information Operations and Warfare
- Military-digital complex
- Economic and Industrial Espionage
- U.S. Cyber Command
- Hunt, Edward (2012). "US Government Computer Penetration Programs and the Implications for Cyberwar". IEEE Annals of the History of Computing.
- Obama Order Sped Up Wave of Cyberattacks Against Iran with diagram, 1 June 2012
Stealth Technology
- YouTube Video of the Stealth Bomber in Action
- YouTube Video: How Does Stealth Technology Work?
- YouTube Video: Here's The Inside Scoop of How Deadly the New F-35 Stealth Fighter Will Be
Stealth technology also termed low observable technology (LO technology) is a sub-discipline of military tactics and passive electronic countermeasures, which cover a range of techniques used with personnel, aircraft, ships, submarines, missiles and satellites to make them less visible (ideally invisible) to radar, infrared, sonar and other detection methods. It corresponds to military camouflage for these parts of the electromagnetic spectrum (Multi-spectral camouflage).
Development of modern stealth technologies in the United States began in 1958, where earlier attempts in preventing radar tracking of its U-2 spy planes during the Cold War by the Soviet Union had been unsuccessful. Designers turned to develop a particular shape for planes that tended to reduce detection, by redirecting electromagnetic waves from radars.
Radar-absorbent material was also tested and made to reduce or block radar signals that reflect off from the surface of planes. Such changes to shape and surface composition form stealth technology as currently used on the Northrop Grumman B-2 Spirit "Stealth Bomber".
The concept of stealth is to operate or hide without giving enemy forces any indications as to the presence of friendly forces. This concept was first explored through camouflage by blending into the background visual clutter. As the potency of detection and interception technologies (radar, Infra-red search and track, surface-to-air missiles, etc.) have increased over time, so too has the extent to which the design and operation of military personnel and vehicles have been affected in response. Some military uniforms are treated with chemicals to reduce their infrared signature.
A modern "stealth" vehicle is designed from the outset to have a chosen spectral signature. The degree of stealth embodied in a particular design is chosen according to the predicted capabilities of projected threats.
Click on any of the following blue hyperlinks for more about Stealth Technology:
Development of modern stealth technologies in the United States began in 1958, where earlier attempts in preventing radar tracking of its U-2 spy planes during the Cold War by the Soviet Union had been unsuccessful. Designers turned to develop a particular shape for planes that tended to reduce detection, by redirecting electromagnetic waves from radars.
Radar-absorbent material was also tested and made to reduce or block radar signals that reflect off from the surface of planes. Such changes to shape and surface composition form stealth technology as currently used on the Northrop Grumman B-2 Spirit "Stealth Bomber".
The concept of stealth is to operate or hide without giving enemy forces any indications as to the presence of friendly forces. This concept was first explored through camouflage by blending into the background visual clutter. As the potency of detection and interception technologies (radar, Infra-red search and track, surface-to-air missiles, etc.) have increased over time, so too has the extent to which the design and operation of military personnel and vehicles have been affected in response. Some military uniforms are treated with chemicals to reduce their infrared signature.
A modern "stealth" vehicle is designed from the outset to have a chosen spectral signature. The degree of stealth embodied in a particular design is chosen according to the predicted capabilities of projected threats.
Click on any of the following blue hyperlinks for more about Stealth Technology:
- History
- Principles
- Radar cross-section (RCS) reductions
- Acoustics
- Visibility
- Infrared
- Reducing radio frequency (RF) emissions
- Measuring
- Tactics
- Research
- List of stealth aircraft
- List of stealth ships
- See also
- Horten brothers – German engineers whose planes were the models for the stealth bombers.
- Multi-spectral camouflage
- Petr Ufimtsev – Soviet/Russian physicist who created much of the original theory behind radar stealth
- Radar
- Stealth design used for military aircraft?
- A Stealth Satellite Sourcebook
- Stealth in strike warfare
- Stealth technology
- The Paradigm Shift in Air Superiority (Stealth)
Military Science and Engineering
TOP: The EBG combat engineering vehicle, based on the AMX 30 tank, is used by the engineers of the French Army for a variety of missions.
BOTTOM: Remote control of drones is one of the many contributions science and technology have made to war. (Image by MICHAELA REHLE/REUTERS/CORBIS)
- YouTube Video 6 Mind-Bending Future Military Technologies That Are on the Next Level
- YouTube Video: WORST NIGHTMARE for Russian Military US Military advanced robot technology
- YouTube Video: TOP 7 AMAZING MILITARY INVENTIONS
TOP: The EBG combat engineering vehicle, based on the AMX 30 tank, is used by the engineers of the French Army for a variety of missions.
BOTTOM: Remote control of drones is one of the many contributions science and technology have made to war. (Image by MICHAELA REHLE/REUTERS/CORBIS)
Military science is the study of military processes, institutions, and behavior, along with the study of warfare, and the theory and application of organized coercive force. It is mainly focused on theory, method, and practice of producing military capability in a manner consistent with national defense policy.
Military science serves to identify the following elements:
The above are necessary to sustain relative advantage of military force; and to increase the likelihood and favorable outcomes of victory in peace or during a war. Military scientists include theorists, researchers, experimental scientists, applied scientists, designers, engineers, test technicians, and other military personnel.
Military personnel obtain weapons, equipment, and training to achieve specific strategic goals. Military science is also used to establish enemy capability as part of technical intelligence.
In military history, military science had been used during the period of Industrial Revolution as a general term to refer to all matters of military theory and technology application as a single academic discipline, including that of the deployment and employment of troops in peacetime or in battle.
In military education, military science is often the name of the department in the education institution that administers officer candidate education. However, this education usually focuses on the officer leadership training and basic information about employment of military theories, concepts, methods and systems, and graduates are not military scientists on completion of studies, but rather junior military officers.
Click on any of the following blue hyperlinks for more about Military Science:
Military engineering is loosely defined as the art, science, and practice of designing and building military works and maintaining lines of military transport and military communications. Military engineers are also responsible for logistics behind military tactics.
Modern military engineering differs from civil engineering. In the 20th and 21st centuries, military engineering also includes other engineering disciplines such as mechanical and electrical engineering techniques.
According to NATO, "military engineering is that engineer activity undertaken, regardless of component or service, to shape the physical operating environment. Military engineering incorporates support to maneuver and to the force as a whole, including military engineering functions such as engineer support to force protection, counter-improvised explosive devices, environmental protection, engineer intelligence and military search.
Military engineering does not encompass the activities undertaken by those 'engineers' who maintain, repair and operate vehicles, vessels, aircraft, weapon systems and equipment."
Military engineering is an academic subject taught in military academies or schools of military engineering. The construction and demolition tasks related to military engineering are usually performed by military engineers including soldiers trained as sappers or pioneers. In modern armies, soldiers trained to perform such tasks while well forward in battle and under fire are often called combat engineers.
In some countries, military engineers may also perform non-military construction tasks in peacetime such as flood control and river navigation works, but such activities do not fall within the scope of military engineering.
The word engineer was initially used in the context of warfare, dating back to 1325 when engine’er (literally, one who operates an engine) referred to "a constructor of military engines". In this context, "engine" referred to a military machine, i. e., a mechanical contraption used in war (for example, a catapult).
As the design of civilian structures such as bridges and buildings developed as a technical discipline, the term civil engineering entered the lexicon as a way to distinguish between those specializing in the construction of such non-military projects and those involved in the older discipline.
As the prevalence of civil engineering outstripped engineering in a military context and the number of disciplines expanded, the original military meaning of the word "engineering" is now largely obsolete. In its place, the term "military engineering" has come to be used.
Click on any of the following blue hyperlinks for more about Military Engineering:
Military science serves to identify the following elements:
The above are necessary to sustain relative advantage of military force; and to increase the likelihood and favorable outcomes of victory in peace or during a war. Military scientists include theorists, researchers, experimental scientists, applied scientists, designers, engineers, test technicians, and other military personnel.
Military personnel obtain weapons, equipment, and training to achieve specific strategic goals. Military science is also used to establish enemy capability as part of technical intelligence.
In military history, military science had been used during the period of Industrial Revolution as a general term to refer to all matters of military theory and technology application as a single academic discipline, including that of the deployment and employment of troops in peacetime or in battle.
In military education, military science is often the name of the department in the education institution that administers officer candidate education. However, this education usually focuses on the officer leadership training and basic information about employment of military theories, concepts, methods and systems, and graduates are not military scientists on completion of studies, but rather junior military officers.
Click on any of the following blue hyperlinks for more about Military Science:
- History
- Employment of military skills
- Military concepts and methods
- Military systems
- Military studies journals
- University studies
- See also:
- List of basic military science and technology topics
- List of military writers
- US Military/Government Texts:
- The Logic of Warfighting Experiments by Kass (CCRP, 2006)
- Complexity, Networking, and Effects Based Approaches to Operations by Smith (CCRP, 2006)
- Understanding Command and Control by Alberts and Hayes (CCRP, 2006)
- The Agile Organization by Atkinson and Moffat (CCRP, 2005)
- Power to the Edge by Alberts and Hayes (CCRP, 2003)
- Network Centric Warfare by Alberts et al. (CCRP, 1999)
Military engineering is loosely defined as the art, science, and practice of designing and building military works and maintaining lines of military transport and military communications. Military engineers are also responsible for logistics behind military tactics.
Modern military engineering differs from civil engineering. In the 20th and 21st centuries, military engineering also includes other engineering disciplines such as mechanical and electrical engineering techniques.
According to NATO, "military engineering is that engineer activity undertaken, regardless of component or service, to shape the physical operating environment. Military engineering incorporates support to maneuver and to the force as a whole, including military engineering functions such as engineer support to force protection, counter-improvised explosive devices, environmental protection, engineer intelligence and military search.
Military engineering does not encompass the activities undertaken by those 'engineers' who maintain, repair and operate vehicles, vessels, aircraft, weapon systems and equipment."
Military engineering is an academic subject taught in military academies or schools of military engineering. The construction and demolition tasks related to military engineering are usually performed by military engineers including soldiers trained as sappers or pioneers. In modern armies, soldiers trained to perform such tasks while well forward in battle and under fire are often called combat engineers.
In some countries, military engineers may also perform non-military construction tasks in peacetime such as flood control and river navigation works, but such activities do not fall within the scope of military engineering.
The word engineer was initially used in the context of warfare, dating back to 1325 when engine’er (literally, one who operates an engine) referred to "a constructor of military engines". In this context, "engine" referred to a military machine, i. e., a mechanical contraption used in war (for example, a catapult).
As the design of civilian structures such as bridges and buildings developed as a technical discipline, the term civil engineering entered the lexicon as a way to distinguish between those specializing in the construction of such non-military projects and those involved in the older discipline.
As the prevalence of civil engineering outstripped engineering in a military context and the number of disciplines expanded, the original military meaning of the word "engineering" is now largely obsolete. In its place, the term "military engineering" has come to be used.
Click on any of the following blue hyperlinks for more about Military Engineering:
- History
- Education
- Sub-discipline
- Explosives Engineering
- Institutions & Professional Associations
- Military engineering by country
- See also:
Manhattan Project along with Development of the Atomic Bomb
- YouTube Video: The Moment in Time: The Manhattan Project
- YouTube Video: Testing The Atomic Bomb | Hiroshima | BBC
- YouTube Video: An exclusive look at the world’s largest-ever nuclear cleanup
The Manhattan Project was a research and development undertaking during World War II that produced the first nuclear weapons. It was led by the United States with the support of the United Kingdom and Canada.
From 1942 to 1946, the project was under the direction of Major General Leslie Groves of the U.S. Army Corps of Engineers. Nuclear physicist Robert Oppenheimer was the director of the Los Alamos Laboratory that designed the actual bombs.
The Army component of the project was designated the Manhattan District; Manhattan gradually superseded the official codename, Development of Substitute Materials, for the entire project. Along the way, the project absorbed its earlier British counterpart, Tube Alloys.
The Manhattan Project began modestly in 1939, but grew to employ more than 130,000 people and cost nearly US$2 billion (about $23 billion in 2018 dollars). Over 90% of the cost was for building factories and to produce fissile material, with less than 10% for development and production of the weapons. Research and production took place at more than 30 sites across the United States, the United Kingdom, and Canada.
Two types of atomic bombs were developed concurrently during the war: a relatively simple gun-type fission weapon and a more complex implosion-type nuclear weapon. The Thin Man gun-type design proved impractical to use with plutonium, and therefore a simpler gun-type called Little Boy was developed that used uranium-235, an isotope that makes up only 0.7 percent of natural uranium. Chemically identical to the most common isotope, uranium-238, and with almost the same mass, it proved difficult to separate the two.
Three methods were employed for uranium enrichment: electromagnetic, gaseous and thermal. Most of this work was performed at the Clinton Engineer Works at Oak Ridge, Tennessee.
In parallel with the work on uranium was an effort to produce plutonium. After the feasibility of the world's first artificial nuclear reactor was demonstrated in Chicago at the Metallurgical Laboratory, it designed the X-10 Graphite Reactor at Oak Ridge and the production reactors in Hanford, Washington, in which uranium was irradiated and transmuted into plutonium.
The plutonium was then chemically separated from the uranium, using the bismuth phosphate process. The Fat Man plutonium implosion-type weapon was developed in a concerted design and development effort by the Los Alamos Laboratory.
The project was also charged with gathering intelligence on the German nuclear weapon project. Through Operation Alsos, Manhattan Project personnel served in Europe, sometimes behind enemy lines, where they gathered nuclear materials and documents, and rounded up German scientists. Despite the Manhattan Project's tight security, Soviet atomic spies successfully penetrated the program.
The first nuclear device ever detonated was an implosion-type bomb at the Trinity test, conducted at New Mexico's Alamogordo Bombing and Gunnery Range on 16 July 1945.
Little Boy and Fat Man bombs were used a month later in the atomic bombings of Hiroshima and Nagasaki, respectively. In the immediate postwar years, the Manhattan Project conducted weapons testing at Bikini Atoll as part of Operation Crossroads, developed new weapons, promoted the development of the network of national laboratories, supported medical research into radiology and laid the foundations for the nuclear navy. It maintained control over American atomic weapons research and production until the formation of the United States Atomic Energy Commission in January 1947.
Click on any of the following blue hyperlinks for more about The Manhattan Project:
A nuclear weapon (also called an atom bomb, nuke, atomic bomb, nuclear warhead, A-bomb, or nuclear bomb) is an explosive device that derives its destructive force from nuclear reactions, either fission (fission bomb) or from a combination of fission and fusion reactions (thermonuclear bomb).
Both bomb types release large quantities of energy from relatively small amounts of matter. The first test of a fission ("atomic") bomb released an amount of energy approximately equal to 20,000 tons of TNT. The first thermonuclear ("hydrogen") bomb test released energy approximately equal to 10 million tons of TNT (42 PJ).
A thermonuclear weapon weighing little more than 2,400 pounds (1,100 kg) can release energy equal to more than 1.2 million tons of TNT (5.0 PJ). A nuclear device no larger than traditional bombs can devastate an entire city by blast, fire, and radiation. Since they are weapons of mass destruction, the proliferation of nuclear weapons is a focus of international relations policy.
Nuclear weapons have been used twice in war, both times by the United States against Japan near the end of World War II:
These bombings caused injuries that resulted in the deaths of approximately 200,000 civilians and military personnel. The ethics of these bombings and their role in Japan's surrender are subjects of debate.
Since the atomic bombings of Hiroshima and Nagasaki, nuclear weapons have been detonated over two thousand times for testing and demonstration. Only a few nations possess such weapons or are suspected of seeking them.
The only countries known to have detonated nuclear weapons—and acknowledge possessing them—are (chronologically by date of first test)
Israel is believed to possess nuclear weapons, though, in a policy of deliberate ambiguity, it does not acknowledge having them. Germany, Italy, Turkey, Belgium and the Netherlands are nuclear weapons sharing states.
South Africa is the only country to have independently developed and then renounced and dismantled its nuclear weapons.
The Treaty on the Non-Proliferation of Nuclear Weapons aims to reduce the spread of nuclear weapons, but its effectiveness has been questioned, and political tensions remained high in the 1970s and 1980s. Modernization of weapons continues to this day.
Click on any of the following blue hyperlinks for more about Nuclear Weapons:
From 1942 to 1946, the project was under the direction of Major General Leslie Groves of the U.S. Army Corps of Engineers. Nuclear physicist Robert Oppenheimer was the director of the Los Alamos Laboratory that designed the actual bombs.
The Army component of the project was designated the Manhattan District; Manhattan gradually superseded the official codename, Development of Substitute Materials, for the entire project. Along the way, the project absorbed its earlier British counterpart, Tube Alloys.
The Manhattan Project began modestly in 1939, but grew to employ more than 130,000 people and cost nearly US$2 billion (about $23 billion in 2018 dollars). Over 90% of the cost was for building factories and to produce fissile material, with less than 10% for development and production of the weapons. Research and production took place at more than 30 sites across the United States, the United Kingdom, and Canada.
Two types of atomic bombs were developed concurrently during the war: a relatively simple gun-type fission weapon and a more complex implosion-type nuclear weapon. The Thin Man gun-type design proved impractical to use with plutonium, and therefore a simpler gun-type called Little Boy was developed that used uranium-235, an isotope that makes up only 0.7 percent of natural uranium. Chemically identical to the most common isotope, uranium-238, and with almost the same mass, it proved difficult to separate the two.
Three methods were employed for uranium enrichment: electromagnetic, gaseous and thermal. Most of this work was performed at the Clinton Engineer Works at Oak Ridge, Tennessee.
In parallel with the work on uranium was an effort to produce plutonium. After the feasibility of the world's first artificial nuclear reactor was demonstrated in Chicago at the Metallurgical Laboratory, it designed the X-10 Graphite Reactor at Oak Ridge and the production reactors in Hanford, Washington, in which uranium was irradiated and transmuted into plutonium.
The plutonium was then chemically separated from the uranium, using the bismuth phosphate process. The Fat Man plutonium implosion-type weapon was developed in a concerted design and development effort by the Los Alamos Laboratory.
The project was also charged with gathering intelligence on the German nuclear weapon project. Through Operation Alsos, Manhattan Project personnel served in Europe, sometimes behind enemy lines, where they gathered nuclear materials and documents, and rounded up German scientists. Despite the Manhattan Project's tight security, Soviet atomic spies successfully penetrated the program.
The first nuclear device ever detonated was an implosion-type bomb at the Trinity test, conducted at New Mexico's Alamogordo Bombing and Gunnery Range on 16 July 1945.
Little Boy and Fat Man bombs were used a month later in the atomic bombings of Hiroshima and Nagasaki, respectively. In the immediate postwar years, the Manhattan Project conducted weapons testing at Bikini Atoll as part of Operation Crossroads, developed new weapons, promoted the development of the network of national laboratories, supported medical research into radiology and laid the foundations for the nuclear navy. It maintained control over American atomic weapons research and production until the formation of the United States Atomic Energy Commission in January 1947.
Click on any of the following blue hyperlinks for more about The Manhattan Project:
- Origins
- Feasibility
- Organization
- Project sites
- Uranium
- Plutonium
- Personnel
- Secrecy
- Foreign intelligence
- Atomic bombings of Hiroshima and Nagasaki
- After the war
- Cost
- Legacy
- "The Atomic Bomb and the End of World War II, A Collection of Primary Sources". George Washington University. Retrieved 27 July 2011.
- "Atomic Heritage Foundation". Atomic Heritage Foundation. Retrieved 27 July 2011.
- "Voices of the Manhattan Project". Atomic Heritage Foundation. Retrieved 10 February 2015. Features hundreds of audio/visual interviews with Manhattan Project veterans.
- "History Center: Los Alamos National Laboratory". Los Alamos National Laboratory. Retrieved 27 July 2011.
- "ORNL: The first 50 Years: History of ORNL". ORNL Review. 25 (3). Archived from the original on 2 June 2016. Retrieved 13 October 2015
A nuclear weapon (also called an atom bomb, nuke, atomic bomb, nuclear warhead, A-bomb, or nuclear bomb) is an explosive device that derives its destructive force from nuclear reactions, either fission (fission bomb) or from a combination of fission and fusion reactions (thermonuclear bomb).
Both bomb types release large quantities of energy from relatively small amounts of matter. The first test of a fission ("atomic") bomb released an amount of energy approximately equal to 20,000 tons of TNT. The first thermonuclear ("hydrogen") bomb test released energy approximately equal to 10 million tons of TNT (42 PJ).
A thermonuclear weapon weighing little more than 2,400 pounds (1,100 kg) can release energy equal to more than 1.2 million tons of TNT (5.0 PJ). A nuclear device no larger than traditional bombs can devastate an entire city by blast, fire, and radiation. Since they are weapons of mass destruction, the proliferation of nuclear weapons is a focus of international relations policy.
Nuclear weapons have been used twice in war, both times by the United States against Japan near the end of World War II:
- On August 6, 1945, the U.S. Army Air Forces detonated a uranium gun-type fission bomb nicknamed "Little Boy" over the Japanese city of Hiroshima;
- three days later, on August 9, the U.S. Army Air Forces detonated a plutonium implosion-type fission bomb nicknamed "Fat Man" over the Japanese city of Nagasaki.
These bombings caused injuries that resulted in the deaths of approximately 200,000 civilians and military personnel. The ethics of these bombings and their role in Japan's surrender are subjects of debate.
Since the atomic bombings of Hiroshima and Nagasaki, nuclear weapons have been detonated over two thousand times for testing and demonstration. Only a few nations possess such weapons or are suspected of seeking them.
The only countries known to have detonated nuclear weapons—and acknowledge possessing them—are (chronologically by date of first test)
- the United States,
- the Soviet Union (succeeded as a nuclear power by Russia),
- the United Kingdom,
- France,
- China,
- India,
- Pakistan,
- and North Korea.
Israel is believed to possess nuclear weapons, though, in a policy of deliberate ambiguity, it does not acknowledge having them. Germany, Italy, Turkey, Belgium and the Netherlands are nuclear weapons sharing states.
South Africa is the only country to have independently developed and then renounced and dismantled its nuclear weapons.
The Treaty on the Non-Proliferation of Nuclear Weapons aims to reduce the spread of nuclear weapons, but its effectiveness has been questioned, and political tensions remained high in the 1970s and 1980s. Modernization of weapons continues to this day.
Click on any of the following blue hyperlinks for more about Nuclear Weapons:
- Types
- Weapons delivery
- Nuclear strategy
- Governance, control, and law
- Controversy
- Effects of nuclear explosions
- Costs and technology spin-offs
- Non-weapons uses
- History of development
- See also:
- Cobalt bomb
- Cuban Missile Crisis
- Dirty bomb
- Induced gamma emission
- International Court of Justice advisory opinion on the Legality of the Threat or Use of Nuclear Weapons
- List of nuclear close calls
- List of nuclear weapons
- List of states with nuclear weapons
- Nth Country Experiment
- Nuclear blackout
- Nuclear bunker buster
- Nuclear holocaust
- Nuclear warfare
- Nuclear weapons and the United Kingdom
- Nuclear weapons in popular culture
- Nuclear weapons of the United States
- OPANAL (Agency for the Prohibition of Nuclear Weapons in Latin America and the Caribbean)
- Russia and weapons of mass destruction
- Three Non-Nuclear Principles of Japan
- Nuclear Weapon Archive from Carey Sublette is a reliable source of information and has links to other sources and an informative FAQ.
- The Federation of American Scientists provide solid information on weapons of mass destruction, including nuclear weapons and their effects
- Alsos Digital Library for Nuclear Issues – contains many resources related to nuclear weapons, including a historical and technical overview and searchable bibliography of web and print resources.
- Video archive of US, Soviet, UK, Chinese and French Nuclear Weapon Testing at sonicbomb.com
- The National Museum of Nuclear Science & History (United States) – located in Albuquerque, New Mexico; a Smithsonian Affiliate Museum
- Nuclear Emergency and Radiation Resources
- The Manhattan Project: Making the Atomic Bomb at AtomicArchive.com
- Los Alamos National Laboratory: History (U.S. nuclear history)
- Race for the Superbomb, PBS website on the history of the H-bomb
- The Woodrow Wilson Center's Nuclear Proliferation International History Project or NPIHP is a global network of individuals and institutions engaged in the study of international nuclear history through archival documents, oral history interviews and other empirical sources.
- NUKEMAP3D – a 3D nuclear weapons effects simulator powered by Google Maps.
Technology for Military and Civilian Application
TOP: SpaceX Missile capable of (LEFT) launching then (RIGHT) landing Upright
CENTER: The basic components of a thermal-imaging device (e.g., nighttime goggles)
BOTTOM: How a Nuclear Reactor works to generate electricity for homes
- YouTube Video: How Nuclear Power Plants Work / Nuclear Energy (Animation)
- YouTube Video of a SpaceX Launch and Landing
- YouTube Video: How does Night Vision Goggles Work?
TOP: SpaceX Missile capable of (LEFT) launching then (RIGHT) landing Upright
CENTER: The basic components of a thermal-imaging device (e.g., nighttime goggles)
BOTTOM: How a Nuclear Reactor works to generate electricity for homes
In politics and diplomacy, "dual-use" refers to technology that can be used for both peaceful and military aims.
More generally speaking, dual-use can also refer to any technology which can satisfy more than one goal at any given time. Thus, expensive technologies which would otherwise only benefit civilian commercial interests can also be used to serve military purposes when not otherwise engaged such as the Global Positioning System.
Missile:
Originally developed as weapons during the Cold War, the United States and the Soviet Union spent billions of dollars developing rocket technology which could carry humans into space (and even eventually to the moon). The development of this peaceful rocket technology paralleled the development of intercontinental ballistic missile technology; and was a way of demonstrating to the other side the potential of one's own rockets.
Those who seek to develop ballistic missiles may claim that their rockets are for peaceful purposes; for example, for commercial satellite launching or scientific purposes. However, even genuinely peaceful rockets may be converted into weapons and provide the technological basis to do so.
Within peaceful rocket programs, different peaceful applications can be seen as having parallel military roles. For example, the return of scientific payloads safely to earth from orbit would indicate re-entry vehicle capability and demonstrating the ability to launch multiple satellites with a single launch vehicle can be seen in a military context as having the potential to deploy multiple independently targeted reentry vehicles.
Nuclear:
Dual-use nuclear technology refers to the possibility of military use of civilian nuclear power technology. Many technologies and materials associated with the creation of a nuclear power program have a dual-use capability, in that several stages of the nuclear fuel cycle allow diversion of nuclear materials for nuclear weapons. When this happens a nuclear power program can become a route leading to the atomic bomb or a public annex to a secret bomb program. The crisis over Iran’s nuclear activities is a case in point.
Many UN and US agencies warn that building more nuclear reactors unavoidably increases nuclear proliferation risks. A fundamental goal for American and global security is to minimize the proliferation risks associated with the expansion of nuclear power. If this development is "poorly managed or efforts to contain risks are unsuccessful, the nuclear future will be dangerous".
For nuclear power programs to be developed and managed safely and securely, it is important that countries have domestic “good governance” characteristics that will encourage proper nuclear operations and management:
These characteristics include:
Chemical:
Main article: List of Schedule 3 substances (CWC)
The modern history of chemical weapons can be traced back to the chemical industries of the belligerent nations of World War I, especially that of Germany. Many industrial chemical processes produce toxic intermediary stages, final products, and by-products, and any nation with a chemical industry has the potential to create weaponised chemical agents.
Biological:
Lax biosecurity at laboratories is worrying researchers and regulators that potential select agents may have fallen into the hands of malevolent parties. It may have been instrumental to the 2001 anthrax attacks in the United States. Universities sometimes flout regulations, complacent as to the dangers in doing so.
Though the majority of breaches are benign, the hybridization of hepatitis C and dengue-fever viruses at Imperial College London in 1997 resulted in a fine when health and safety rules were not observed. A research program at Texas A&M University was shut down when Brucella and Coxiella infections were not reported.
That the July 2007 terrorist attacks in central London and at Glasgow airport may have involved National Health Service medical professionals was a recent wake-up call that screening people with access to pathogens may be necessary. The challenge remains to maintain security without impairing the contributions to progress afforded by research.
Reports from the project on building a sustainable culture in dual-use bioethics suggest that, as a result of perceived changes in both science and security over the past decade, several states and multilateral bodies have underlined the importance of making life scientists aware of concerns over dual-use and the legal obligations underpinning the prevention of biological weapons.
One of the key mechanisms that have been identified to achieve this is through the education of life science students, with the objective of building what has been termed a “culture of responsibility”.
At the 2008 Meeting of States Parties to the Biological and Toxin Weapons Convention (BTWC), it was agreed by consensus that: States Parties recognized the importance of ensuring that those working in the biological sciences are aware of their obligations under the Convention and relevant national legislation and guidelines.
States Parties noted that formal requirements for seminars, modules or courses, including possible mandatory components, in relevant scientific and engineering training programmes and continuing professional education could assist in raising awareness and in implementing the Convention.
With several similar stipulations from other states and regional organisations, there is evidence to suggest that the concept of biosecurity education has become increasingly salient in the contemporary security discourse.
Unfortunately however, there is an emerging understanding in both the policy and academic literature that life scientists across the globe are frequently uninformed or under-informed on issues such as biosecurity, dual-use, the BTWC and national legislation outlawing biological weapons.
Moreover, despite numerous declarations by states and multilateral organisations, the extent to which statements at the international level have trickled down to multifaceted activity at the level of scientists remains limited.
Night vision and thermal imaging:
Imaging systems with extraordinary performance characteristics (high gain, specific spectral sensitivity, fine resolution, low noise) are heavily export-restricted by the few states capable of producing them, mainly to limit their proliferation to enemy combatants, but also to slow the inevitable reverse-engineering undertaken by other world powers.
These precision components, such as the image intensifiers used in night vision goggles and the focal plane arrays found in surveillance satellites and thermal cameras, have numerous civil applications which include nature photography, medical imaging, firefighting, and population control of predator species.
Night scenes of wild elephants and rhinos in the BBC nature documentary series Africa were shot on a Lunax Starlight HD camera (a custom-built digital cinema rig encompassing a Generation 3 image intensifier), and recolored digitally.
In the United States, civilians are free to buy and sell American-made night vision and thermal systems, such as those manufactured by defense contractors Harris, L3 Insight, and FLIR Systems, with very few restrictions. However, American night vision owners may not bring the equipment out of the country, sell it internationally, or even invite non-citizens to examine the technology, per International Traffic in Arms Regulations.
Export of American image intensifiers is selectively permitted under license by the United States Department of Commerce and the State Department. Contributing factors in acquiring a license include diplomatic relations with the destination country, number of pieces to be sold, and the relative quality of the equipment itself, expressed using a Figure Of Merit (FOM) score calculated from several key performance characteristics.
Competing international manufacturers (European defense contractor Photonis Group, Japanese scientific instrument giant Hamamatsu Photonics, and Russian state-financed laboratory JSC Katod) have entered the American market through licensed importers. In spite of their foreign origin, re-export of these components outside of the United States is restricted similarly to domestic components.
A 2012 assessment of the sector by the Department of Commerce and Bureau of Industry and Security made the case for relaxing export controls in light of the narrowing performance gap and increased competition internationally, and a review period undertaken by the Directorate of Defense Trade Controls in 2015 introduced much more granular performance definitions.
Other technologies:
In addition to obvious and headline-grabbing dual-use technologies there are some less obvious ones, in that many erstwhile peaceful technologies can be used in weapons.
One example during the First and Second World War is the role of German toy manufacturers: Germany was one of the leading nations in the production of wind-up toys, and the ability to produce large numbers of small and reliable clockwork motors was converted into the ability to produce shell and bomb fuses.
Control:
Most industrial countries have export controls on certain types of designated dual-use technologies, and they are required by a number of treaties as well. These controls restrict the export of certain commodities and technologies without the permission of the government.
The principal agency for investigating violations of dual use export controls in the United States is the Bureau of Industry and Security, Office of Export Enforcement. Interagency coordination of export control cases are conducted through the Export Enforcement Coordination Center (E2C2).
There are several international arrangements among countries which seek to harmonize lists of dual-use (and military) technologies to control. These include:
See also:
More generally speaking, dual-use can also refer to any technology which can satisfy more than one goal at any given time. Thus, expensive technologies which would otherwise only benefit civilian commercial interests can also be used to serve military purposes when not otherwise engaged such as the Global Positioning System.
Missile:
Originally developed as weapons during the Cold War, the United States and the Soviet Union spent billions of dollars developing rocket technology which could carry humans into space (and even eventually to the moon). The development of this peaceful rocket technology paralleled the development of intercontinental ballistic missile technology; and was a way of demonstrating to the other side the potential of one's own rockets.
Those who seek to develop ballistic missiles may claim that their rockets are for peaceful purposes; for example, for commercial satellite launching or scientific purposes. However, even genuinely peaceful rockets may be converted into weapons and provide the technological basis to do so.
Within peaceful rocket programs, different peaceful applications can be seen as having parallel military roles. For example, the return of scientific payloads safely to earth from orbit would indicate re-entry vehicle capability and demonstrating the ability to launch multiple satellites with a single launch vehicle can be seen in a military context as having the potential to deploy multiple independently targeted reentry vehicles.
Nuclear:
Dual-use nuclear technology refers to the possibility of military use of civilian nuclear power technology. Many technologies and materials associated with the creation of a nuclear power program have a dual-use capability, in that several stages of the nuclear fuel cycle allow diversion of nuclear materials for nuclear weapons. When this happens a nuclear power program can become a route leading to the atomic bomb or a public annex to a secret bomb program. The crisis over Iran’s nuclear activities is a case in point.
Many UN and US agencies warn that building more nuclear reactors unavoidably increases nuclear proliferation risks. A fundamental goal for American and global security is to minimize the proliferation risks associated with the expansion of nuclear power. If this development is "poorly managed or efforts to contain risks are unsuccessful, the nuclear future will be dangerous".
For nuclear power programs to be developed and managed safely and securely, it is important that countries have domestic “good governance” characteristics that will encourage proper nuclear operations and management:
These characteristics include:
- low degrees of corruption (to avoid officials selling materials and technology for their own personal gain as occurred with the A.Q. Khan smuggling network in Pakistan),
- high degrees of political stability (defined by the World Bank as “likelihood that the government will be destabilized or overthrown by unconstitutional or violent means, including politically-motivated violence and terrorism”),
- high governmental effectiveness scores (a World Bank aggregate measure of “the quality of the civil service and the degree of its independence from political pressures [and] the quality of policy formulation and implementation”),
- and a strong degree of regulatory competence.
Chemical:
Main article: List of Schedule 3 substances (CWC)
The modern history of chemical weapons can be traced back to the chemical industries of the belligerent nations of World War I, especially that of Germany. Many industrial chemical processes produce toxic intermediary stages, final products, and by-products, and any nation with a chemical industry has the potential to create weaponised chemical agents.
Biological:
Lax biosecurity at laboratories is worrying researchers and regulators that potential select agents may have fallen into the hands of malevolent parties. It may have been instrumental to the 2001 anthrax attacks in the United States. Universities sometimes flout regulations, complacent as to the dangers in doing so.
Though the majority of breaches are benign, the hybridization of hepatitis C and dengue-fever viruses at Imperial College London in 1997 resulted in a fine when health and safety rules were not observed. A research program at Texas A&M University was shut down when Brucella and Coxiella infections were not reported.
That the July 2007 terrorist attacks in central London and at Glasgow airport may have involved National Health Service medical professionals was a recent wake-up call that screening people with access to pathogens may be necessary. The challenge remains to maintain security without impairing the contributions to progress afforded by research.
Reports from the project on building a sustainable culture in dual-use bioethics suggest that, as a result of perceived changes in both science and security over the past decade, several states and multilateral bodies have underlined the importance of making life scientists aware of concerns over dual-use and the legal obligations underpinning the prevention of biological weapons.
One of the key mechanisms that have been identified to achieve this is through the education of life science students, with the objective of building what has been termed a “culture of responsibility”.
At the 2008 Meeting of States Parties to the Biological and Toxin Weapons Convention (BTWC), it was agreed by consensus that: States Parties recognized the importance of ensuring that those working in the biological sciences are aware of their obligations under the Convention and relevant national legislation and guidelines.
States Parties noted that formal requirements for seminars, modules or courses, including possible mandatory components, in relevant scientific and engineering training programmes and continuing professional education could assist in raising awareness and in implementing the Convention.
With several similar stipulations from other states and regional organisations, there is evidence to suggest that the concept of biosecurity education has become increasingly salient in the contemporary security discourse.
Unfortunately however, there is an emerging understanding in both the policy and academic literature that life scientists across the globe are frequently uninformed or under-informed on issues such as biosecurity, dual-use, the BTWC and national legislation outlawing biological weapons.
Moreover, despite numerous declarations by states and multilateral organisations, the extent to which statements at the international level have trickled down to multifaceted activity at the level of scientists remains limited.
Night vision and thermal imaging:
Imaging systems with extraordinary performance characteristics (high gain, specific spectral sensitivity, fine resolution, low noise) are heavily export-restricted by the few states capable of producing them, mainly to limit their proliferation to enemy combatants, but also to slow the inevitable reverse-engineering undertaken by other world powers.
These precision components, such as the image intensifiers used in night vision goggles and the focal plane arrays found in surveillance satellites and thermal cameras, have numerous civil applications which include nature photography, medical imaging, firefighting, and population control of predator species.
Night scenes of wild elephants and rhinos in the BBC nature documentary series Africa were shot on a Lunax Starlight HD camera (a custom-built digital cinema rig encompassing a Generation 3 image intensifier), and recolored digitally.
In the United States, civilians are free to buy and sell American-made night vision and thermal systems, such as those manufactured by defense contractors Harris, L3 Insight, and FLIR Systems, with very few restrictions. However, American night vision owners may not bring the equipment out of the country, sell it internationally, or even invite non-citizens to examine the technology, per International Traffic in Arms Regulations.
Export of American image intensifiers is selectively permitted under license by the United States Department of Commerce and the State Department. Contributing factors in acquiring a license include diplomatic relations with the destination country, number of pieces to be sold, and the relative quality of the equipment itself, expressed using a Figure Of Merit (FOM) score calculated from several key performance characteristics.
Competing international manufacturers (European defense contractor Photonis Group, Japanese scientific instrument giant Hamamatsu Photonics, and Russian state-financed laboratory JSC Katod) have entered the American market through licensed importers. In spite of their foreign origin, re-export of these components outside of the United States is restricted similarly to domestic components.
A 2012 assessment of the sector by the Department of Commerce and Bureau of Industry and Security made the case for relaxing export controls in light of the narrowing performance gap and increased competition internationally, and a review period undertaken by the Directorate of Defense Trade Controls in 2015 introduced much more granular performance definitions.
Other technologies:
In addition to obvious and headline-grabbing dual-use technologies there are some less obvious ones, in that many erstwhile peaceful technologies can be used in weapons.
One example during the First and Second World War is the role of German toy manufacturers: Germany was one of the leading nations in the production of wind-up toys, and the ability to produce large numbers of small and reliable clockwork motors was converted into the ability to produce shell and bomb fuses.
Control:
Most industrial countries have export controls on certain types of designated dual-use technologies, and they are required by a number of treaties as well. These controls restrict the export of certain commodities and technologies without the permission of the government.
The principal agency for investigating violations of dual use export controls in the United States is the Bureau of Industry and Security, Office of Export Enforcement. Interagency coordination of export control cases are conducted through the Export Enforcement Coordination Center (E2C2).
There are several international arrangements among countries which seek to harmonize lists of dual-use (and military) technologies to control. These include:
- the Nuclear Suppliers Group,
- the Australia Group, which looks at chemical and biological technologies,
- the Missile Technology Control Regime, which covers delivery systems for weapons of mass destruction,
- and the Wassenaar Arrangement, which covers conventional arms and dual-use technologies.
See also:
- Treaty on the Non-Proliferation of Nuclear Weapons
- U.S. Department of Commerce, Bureau of Industry and Security
- Federation of American Scientists Case Studies in Dual-Use Research
- University of Bradford Disarmament Research Centre Dual Use Bioethics Homepage.
- European Commission, List of Dual-use items and technologies
- Commission updates EU control list on dual use items (22 October 2014)
- European Parliament Rapporteur Marietje Schaake on Dual-Use / Surveillance Technology
Military-Industrial Complex Pictured below: The illustration below demonstrates the quid pro quo inter-relationships between Congress, voters/employees, defense contractors/lobbyists and media.
The military–industrial complex (MIC) is an informal alliance between a nation's military and the defense industry that supplies it, seen together as a vested interest which influences public policy.
A driving factor behind this relationship between the government and defense-minded corporations is that both sides benefit—one side from obtaining war weapons, and the other from being paid to supply them.
The term is most often used in reference to the system behind the military of the United States, where it is most prevalent due to close links between defense contractors, the Pentagon and politicians and gained popularity after a warning on its detrimental effects in the farewell address of President Dwight D. Eisenhower on January 17, 1961. In the context of the United States, the appellation is sometimes extended to military–industrial–congressional complex (MICC), adding the U.S. Congress to form a three-sided relationship termed an iron triangle.
These relationships include political contributions, political approval for military spending, lobbying to support bureaucracies, and oversight of the industry; or more broadly to include the entire network of contracts and flows of money and resources among individuals as well as corporations and institutions of the defense contractors, private military contractors, The Pentagon, the Congress and executive branch.
Click on any of the following blue hyperlinks for more about the Military-Industrial Complex:
A driving factor behind this relationship between the government and defense-minded corporations is that both sides benefit—one side from obtaining war weapons, and the other from being paid to supply them.
The term is most often used in reference to the system behind the military of the United States, where it is most prevalent due to close links between defense contractors, the Pentagon and politicians and gained popularity after a warning on its detrimental effects in the farewell address of President Dwight D. Eisenhower on January 17, 1961. In the context of the United States, the appellation is sometimes extended to military–industrial–congressional complex (MICC), adding the U.S. Congress to form a three-sided relationship termed an iron triangle.
These relationships include political contributions, political approval for military spending, lobbying to support bureaucracies, and oversight of the industry; or more broadly to include the entire network of contracts and flows of money and resources among individuals as well as corporations and institutions of the defense contractors, private military contractors, The Pentagon, the Congress and executive branch.
Click on any of the following blue hyperlinks for more about the Military-Industrial Complex:
- Etymology
- Post-Cold War
- Eras of the United States Military Industrial Complex
- Benefits
- The military subsidy theory
- Current applications
- Similar Concepts
- See also:
- Animal industrial complex
- Companies by arms sales
- Corporate statism
- Erik Prince and Academi (formerly Blackwater)
- Government contractor
- List of countries by military expenditures
- Militarism
- Military budget
- Military-entertainment-complex
- Military–industrial–media complex
- Military-digital complex
- Military Keynesianism
- National security state
- Politico-media complex
- Prison–industrial complex
- Project for the New American Century
- Rosoboronexport
- Upward Spiral
- War profiteering
- Literature and media:
- War Is a Racket (1935 book by Smedley Butler)
- Why We Fight (2005 documentary film by Eugene Jarecki)
- War Made Easy: How Presidents & Pundits Keep Spinning Us to Death (2007 documentary film)
- The Complex: How the Military Invades Our Everyday Lives (2008 book by Nick Turse)
- Khaki capitalism, The Economist, Dec 3rd 2011
- Militaryindustrialcomplex.com, Features running daily, weekly and monthly defense spending totals plus Contract Archives section.
- C. Wright Mills, Structure of Power in American Society, British Journal of Sociology, Vol. 9. No. 1 1958
- Dwight David Eisenhower, Farewell Address On the military–industrial complex and the government–universities collusion – 17 January 1961
- William McGaffin and Erwin Knoll, The military–industrial complex, An analysis of the phenomenon written in 1969
- The Cost of War & Today's Military Industrial Complex, National Public Radio, 8 January 2003.
- Leading Defense Industry news source
- Human Rights First; Private Security Contractors at War: Ending the Culture of Impunity (2008)
- Fifty Years After Eisenhower's Farewell Address, A Look at the Military–Industrial Complex – video report by Democracy Now!
- Military Industrial Complex – video reports by The Real News
Militarization of Space, including Space Warfare and its Space Weapons
- YouTube Video: The Future of Space Warfare
- YouTube Video: Neil deGrasse Tyson On What Space Militarization Means
- YouTube Video: 10 Most Dangerous Space Weapons
The militarization of space involves the placement and development of weaponry and military technology in outer space.
The early exploration of space in the mid-20th century had, in part, a military motivation, as the United States and the Soviet Union used it as an opportunity to demonstrate ballistic-missile technology and other technologies having the potential for military application.
Outer space has since been used as an operating location for military spacecraft such as imaging and communications satellites, and some ballistic missiles pass through outer space during their flight.
As of 2019, known deployments of weapons stationed in space include only the Almaz space-station armament and pistols such as the TP-82 Cosmonaut survival pistol (for post-landing, pre-recovery use).
Click on any of the following blue hyperlinks for more about the Militarization of Space:
Space warfare is combat that takes place in outer space. The scope of space warfare therefore includes ground-to-space warfare, such as attacking satellites from the Earth, as well as space-to-space warfare, such as satellites attacking satellites.
As of 2019 no actual warfare has ever taken place in space, though a number of tests and demonstrations have been performed. International treaties are in place that regulate conflicts in space and limit the installation of space weapon systems, especially nuclear weapons.
From 1985 to 2002 there was a United States Space Command, which in 2002 merged with the United States Strategic Command, leaving Air Force Space Command as the primary American military space force.
The Russian Space Force, established on August 10, 1992, which became an independent section of the Russian military on June 1, 2001, was replaced by the Russian Aerospace Defence Forces starting December 1, 2011, but was reestablished as a component of the Russian Aerospace Forces on August 1, 2015.
In 2019 India conducted a test of the ASAT missile making it the fourth country with that capability. In April 2019, the government established the Defence Space Agency, or DSA.
Click on any of the following blue hyperlinks for more about Space Warfare:
Space weapons are weapons used in space warfare. They include weapons that can attack space systems in orbit (i.e. anti-satellite weapons), attack targets on the earth from space or disable missiles travelling through space.
In the course of the militarization of space, such weapons were developed mainly by the contesting superpowers during the Cold War, and some remain under development today. Space weapons are also a central theme in military science fiction and sci-fi video games.
Space-to-space weapons:
The Soviet Almaz secret military space station program was equipped with a fixed 23mm autocannon to prevent hostile interception or boarding by hostile forces.
The Soviet unmanned Polyus weapons platform was designed to be equipped with a megawatt carbon-dioxide laser and a self-defense cannon.
Earth-to-space weapons:
Anti-satellite weapons, which are primarily surface-to-space and air-to-space missiles, have been developed by the United States, the USSR/Russia, India and the People's Republic of China.
Multiple test firings have been done with recent Chinese and U.S test program that destroy an orbiting satellite. In general use of explosive and kinetic kill systems is limited to relatively low altitude due to space debris issues and so as to avoid leaving debris from launch in orbit.
Strategic Defense Initiative:
Main article: Strategic Defense Initiative
On March 23, 1983, President Ronald Reagan proposed the Strategic Defense Initiative, a research program with a goal of developing a defensive system which would destroy enemy ICBMs.
The defensive system was nicknamed Star Wars, after the movie, by its detractors. Some concepts of the system included Brilliant Pebbles, which were Kinetic Kill Vehicles, essentially small rockets launched from satellites toward their targets (a warhead, warhead bus, or even an upper stage of an ICBM).
Other aspects included satellites in orbit carrying powerful lasers or particle beams. When a missile launch was detected, the satellite would fire at the missile (or warheads) and destroy it.
Although no real hardware was ever manufactured for deployment, the military did test the use of lasers mounted on Boeing 747s to destroy missiles in the 2000s, however these were discontinued due to practical limitations of keeping a constant fleet airborne near potential launch sites due to the lasers range limitations keeping a small number from being sufficient.
The tests took place at Edwards Air Force Base.
Space-to-Earth weapons:
Orbital weaponry:
Orbital weaponry is any weapon that is in orbit around a large body such as a planet or moon.
As of September 2017, there are no known operative orbital weapons systems, but several nations have deployed orbital surveillance networks to observe other nations or armed forces.
Several orbital weaponry systems were designed by the United States and the Soviet Union during the Cold War. During World War II Nazi Germany also was developing plans for an orbital weapon called the Sun gun, an orbital mirror that would have been used to focus and weaponize beams of sunlight.
Development of orbital weaponry was largely halted after the entry into force of the Outer Space Treaty and the SALT II treaty. These agreements prohibit weapons of mass destruction from being placed in space.
As other weapons exist, notably those using kinetic bombardment, that would not violate these treaties, some private groups and government officials have proposed a Space Preservation Treaty which would ban the placement of any weaponry in outer space.
Orbital bombardment:
See also: Kinetic bombardment
Orbital bombardment is the act of attacking targets on a planet, moon or other astronomical object from orbit around the object, rather than from an aircraft, or a platform beyond orbit. It has been proposed as a means of attack for several weapons systems concepts, including kinetic bombardment and as a nuclear delivery system.
During the Cold War, the Soviet Union deployed a Fractional Orbital Bombardment System from 1968 to 1983. Using this system, a nuclear warhead could be placed in low Earth orbit, and later de-orbited to hit any location on the Earth's surface.
While the Soviets deployed a working version of the system, they were forbidden by the Outer Space Treaty to place live warheads in space.
The fractional orbital bombardment system was phased out in January 1983 in compliance with the SALT II treaty of 1979, which, among other things, prohibited the deployment of systems capable of placing weapons of mass destruction in such a partial orbit.
Orbital bombardment systems with conventional warheads are permitted under the terms of SALT II. Some of the proposed systems rely on large tungsten carbide/uranium cermet rods dropped from orbit and depend on kinetic energy, rather than explosives, but their mass makes them prohibitively difficult to transport to orbit
In fiction:
Main article: Space warfare in fiction
Fictional or real space weapons in various forms are often prominently featured in science fiction, particularly in military science fiction and in video games with a sci-fi theme.
See also:
The early exploration of space in the mid-20th century had, in part, a military motivation, as the United States and the Soviet Union used it as an opportunity to demonstrate ballistic-missile technology and other technologies having the potential for military application.
Outer space has since been used as an operating location for military spacecraft such as imaging and communications satellites, and some ballistic missiles pass through outer space during their flight.
As of 2019, known deployments of weapons stationed in space include only the Almaz space-station armament and pistols such as the TP-82 Cosmonaut survival pistol (for post-landing, pre-recovery use).
Click on any of the following blue hyperlinks for more about the Militarization of Space:
- History
- Weapons in space
- Space warfare
- Space treaties
- National Missile Defense (NMD)
- See also:
- Do We Really Need Space Weapons? on Slashdot
- Global Network Against Weapons and Nuclear Power in Space
- Polyus page (in Russian)
- K26 Polyus-Energia page
- Astronautix.com Polyus page
- http://www.globalsecurity.org/wmd/world/russia/r-36o.htm
- U.S. deploys warfare unit to jam enemy satellites from the Washington Times
- Space Force and international space law
- Project A119
- Fractional Orbital Bombardment
- Gravity tractor
- Kinetic bombardment
- VRYAN programme
- Anti-satellite weapon
- Artificial satellites:
- Asia's Space Race
- Ballistic missiles
- Commercialization of space
- Disclosure Project
- High altitude nuclear explosion
- Kill vehicle
- Orbital bombardment
- Outer Space Treaty
- Space geostrategy
- Space force
- Strategic Defense Initiative
- Strategy of technology
- Militarisation of cyberspace
Space warfare is combat that takes place in outer space. The scope of space warfare therefore includes ground-to-space warfare, such as attacking satellites from the Earth, as well as space-to-space warfare, such as satellites attacking satellites.
As of 2019 no actual warfare has ever taken place in space, though a number of tests and demonstrations have been performed. International treaties are in place that regulate conflicts in space and limit the installation of space weapon systems, especially nuclear weapons.
From 1985 to 2002 there was a United States Space Command, which in 2002 merged with the United States Strategic Command, leaving Air Force Space Command as the primary American military space force.
The Russian Space Force, established on August 10, 1992, which became an independent section of the Russian military on June 1, 2001, was replaced by the Russian Aerospace Defence Forces starting December 1, 2011, but was reestablished as a component of the Russian Aerospace Forces on August 1, 2015.
In 2019 India conducted a test of the ASAT missile making it the fourth country with that capability. In April 2019, the government established the Defence Space Agency, or DSA.
Click on any of the following blue hyperlinks for more about Space Warfare:
- History
- Theoretical space weaponry
- Practical considerations
- Possible warfare over space
- Space warfare in fiction
- See also:
- Asteroid impact avoidance
- Space force
- Air Force
- Sun outage
- Beijing–Washington space hotline
- Related to specific countries and facilities:
- Department of Defense Manned Space Flight Support Office
- European Aeronautic Defense and Space Company
- Joint Functional Component Command for Space and Global Strike (US Strategic Command)
- National Missile Defense
- Pine Gap (Australia)
- United States Air Force Space Command
- United States Army Space and Missile Defense Command
Space weapons are weapons used in space warfare. They include weapons that can attack space systems in orbit (i.e. anti-satellite weapons), attack targets on the earth from space or disable missiles travelling through space.
In the course of the militarization of space, such weapons were developed mainly by the contesting superpowers during the Cold War, and some remain under development today. Space weapons are also a central theme in military science fiction and sci-fi video games.
Space-to-space weapons:
The Soviet Almaz secret military space station program was equipped with a fixed 23mm autocannon to prevent hostile interception or boarding by hostile forces.
The Soviet unmanned Polyus weapons platform was designed to be equipped with a megawatt carbon-dioxide laser and a self-defense cannon.
Earth-to-space weapons:
Anti-satellite weapons, which are primarily surface-to-space and air-to-space missiles, have been developed by the United States, the USSR/Russia, India and the People's Republic of China.
Multiple test firings have been done with recent Chinese and U.S test program that destroy an orbiting satellite. In general use of explosive and kinetic kill systems is limited to relatively low altitude due to space debris issues and so as to avoid leaving debris from launch in orbit.
Strategic Defense Initiative:
Main article: Strategic Defense Initiative
On March 23, 1983, President Ronald Reagan proposed the Strategic Defense Initiative, a research program with a goal of developing a defensive system which would destroy enemy ICBMs.
The defensive system was nicknamed Star Wars, after the movie, by its detractors. Some concepts of the system included Brilliant Pebbles, which were Kinetic Kill Vehicles, essentially small rockets launched from satellites toward their targets (a warhead, warhead bus, or even an upper stage of an ICBM).
Other aspects included satellites in orbit carrying powerful lasers or particle beams. When a missile launch was detected, the satellite would fire at the missile (or warheads) and destroy it.
Although no real hardware was ever manufactured for deployment, the military did test the use of lasers mounted on Boeing 747s to destroy missiles in the 2000s, however these were discontinued due to practical limitations of keeping a constant fleet airborne near potential launch sites due to the lasers range limitations keeping a small number from being sufficient.
The tests took place at Edwards Air Force Base.
Space-to-Earth weapons:
Orbital weaponry:
Orbital weaponry is any weapon that is in orbit around a large body such as a planet or moon.
As of September 2017, there are no known operative orbital weapons systems, but several nations have deployed orbital surveillance networks to observe other nations or armed forces.
Several orbital weaponry systems were designed by the United States and the Soviet Union during the Cold War. During World War II Nazi Germany also was developing plans for an orbital weapon called the Sun gun, an orbital mirror that would have been used to focus and weaponize beams of sunlight.
Development of orbital weaponry was largely halted after the entry into force of the Outer Space Treaty and the SALT II treaty. These agreements prohibit weapons of mass destruction from being placed in space.
As other weapons exist, notably those using kinetic bombardment, that would not violate these treaties, some private groups and government officials have proposed a Space Preservation Treaty which would ban the placement of any weaponry in outer space.
Orbital bombardment:
See also: Kinetic bombardment
Orbital bombardment is the act of attacking targets on a planet, moon or other astronomical object from orbit around the object, rather than from an aircraft, or a platform beyond orbit. It has been proposed as a means of attack for several weapons systems concepts, including kinetic bombardment and as a nuclear delivery system.
During the Cold War, the Soviet Union deployed a Fractional Orbital Bombardment System from 1968 to 1983. Using this system, a nuclear warhead could be placed in low Earth orbit, and later de-orbited to hit any location on the Earth's surface.
While the Soviets deployed a working version of the system, they were forbidden by the Outer Space Treaty to place live warheads in space.
The fractional orbital bombardment system was phased out in January 1983 in compliance with the SALT II treaty of 1979, which, among other things, prohibited the deployment of systems capable of placing weapons of mass destruction in such a partial orbit.
Orbital bombardment systems with conventional warheads are permitted under the terms of SALT II. Some of the proposed systems rely on large tungsten carbide/uranium cermet rods dropped from orbit and depend on kinetic energy, rather than explosives, but their mass makes them prohibitively difficult to transport to orbit
In fiction:
Main article: Space warfare in fiction
Fictional or real space weapons in various forms are often prominently featured in science fiction, particularly in military science fiction and in video games with a sci-fi theme.
See also:
The Arms Industry, including a List of Companies by Arms Sales as well as a List of Countries by Military Expenditures
TOP: Military Expenditures by Country (2018) By Barnhorst - Own workSource:data from Stockholm International Peace Research Institute Military Expenditure Database https://www.sipri.org/databases/milex, CC BY-SA 4.0,
BOTTOM: in These Times: Here's Exactly Who's Profiting from the War on Yemen (2015-Present)
- YouTube Video: Top 10 Weapons-Producing Countries
- YouTube Video: The global arms trade is booming | The Economist (9/12/2017)
- YouTube Video: Top 10 Weapons-Producing Countries
TOP: Military Expenditures by Country (2018) By Barnhorst - Own workSource:data from Stockholm International Peace Research Institute Military Expenditure Database https://www.sipri.org/databases/milex, CC BY-SA 4.0,
BOTTOM: in These Times: Here's Exactly Who's Profiting from the War on Yemen (2015-Present)
The arms industry, also known as the defense industry or the arms trade, is a global industry which manufactures and sells weapons and military technology. It consists of a commercial industry involved in the research and development, engineering, production, and servicing of military material, equipment, and facilities.
Arms-producing companies, also referred to as arms dealers, defense contractors, or as the military industry, produce arms for the armed forces of states and for civilians.
Departments of government also operate in the arms industry, buying and selling weapons, munitions and other military items. An arsenal is a place where arms and ammunition - whether privately or publicly owned - are made, maintained and repaired, stored, or issued, in any combination.
Products of the arms industry include any of the following:
The arms industry also provides other logistical and operational support.
The Stockholm International Peace Research Institute (SIPRI) estimated military expenditures as of 2012 at roughly $1.8 trillion. This represented a relative decline from 1990, when military expenditures made up 4% of world GDP.
Part of the money goes to the procurement of military hardware and services from the military industry. The combined arms-sales of the top 100 largest arms-producing companies amounted to an estimated $395 billion in 2012 according to SIPRI.
In 2004 over $30 billion were spent in the international arms-trade (a figure that excludes domestic sales of arms). According to SIPRI, the volume of international transfers of major weapons in 2010–14 was 16 percent higher than in 2005–2009. The five biggest exporters in 2010–2014 were the United States, Russia, China, Germany and France, and the five biggest importers were India, Saudi Arabia, China, the United Arab Emirates and Pakistan.
Many industrialized countries have a domestic arms-industry to supply their own military forces. Some countries also have a substantial legal or illegal domestic trade in weapons for use by their own citizens, primarily for self-defense, hunting or sporting purposes. Illegal trade in small arms occurs in many countries and regions affected by political instability.
The Small Arms Survey estimates that 875 million small arms circulate worldwide, produced by more than 1,000 companies from nearly 100 countries.
Governments award contracts to supply their country's military; such arms contracts can become of substantial political importance. The link between politics and the arms trade can result in the development of what U.S. President Dwight D. Eisenhower described in 1961 as a military-industrial complex (see above), where the armed forces, commerce, and politics become closely linked, similarly to the European multilateral defense procurement.
Various corporations, some publicly held, others private, bid for these contracts, which are often worth many billions of dollars. Sometimes, as with the contract for the international Joint Strike Fighter, a competitive tendering process takes place, with the decision made on the merits of the designs submitted by the companies involved. Other times, no bidding or competition takes place.
Click on any of the following blue hyperlinks for more about the Arms Race:
This is a list of the world's 50 largest arms manufacturers and other military service companies, along with their countries of origin. The information is based on a list published by the Stockholm International Peace Research Institute for 2018. The list provided by the SIPRI excludes companies based in China. The numbers are in billions of US dollars.
Click here for the list of 50 largest arms manufacturers.
See also:
This article contains a list of countries by military expenditure in a given year. Military expenditure figures are presented in United States dollars based on either constant or current exchange rates.
Stockholm International Peace Research Institute (SIPRI) 2018 fact sheet:
The first list is based on the SIPRI fact sheet which includes a list of the world's top 15 military spenders in 2018, based on current market exchange rates.
The second list is based on the 2019 edition of "The Military Balance" published by the (IISS) using average market exchange rates.
Click here for a List of Countries by Military Expenditures
Spending based on GDP:
This first list is a list of countries by military expenditure share of GDP—more specifically, a list of the top 15 countries by percentage share in recent years—the amount spent by a nation on its military as a share of its GDP.
The second list presents this as a share of the general government expenditure.
The first list is sourced from the Stockholm International Peace Research Institute for the year 2017 and from Military Balance 2017 published by International Institute for Strategic Studies for the year 2016.
The second list is sourced only from the Stockholm International Peace Research Institute for the year 2017.
None of the following analyze such potential record-breakers like North Korea, Syria, Yemen, and Libya.
Military expenditure as a share of GDP
See Also:
Arms-producing companies, also referred to as arms dealers, defense contractors, or as the military industry, produce arms for the armed forces of states and for civilians.
Departments of government also operate in the arms industry, buying and selling weapons, munitions and other military items. An arsenal is a place where arms and ammunition - whether privately or publicly owned - are made, maintained and repaired, stored, or issued, in any combination.
Products of the arms industry include any of the following:
- guns,
- artillery,
- ammunition,
- missiles,
- military aircraft,
- military vehicles,
- ships,
- electronic systems,
- night-vision devices,
- holographic weapon sights,
- laser rangefinders,
- laser sights,
- hand grenades,
- landmines
- and more.
The arms industry also provides other logistical and operational support.
The Stockholm International Peace Research Institute (SIPRI) estimated military expenditures as of 2012 at roughly $1.8 trillion. This represented a relative decline from 1990, when military expenditures made up 4% of world GDP.
Part of the money goes to the procurement of military hardware and services from the military industry. The combined arms-sales of the top 100 largest arms-producing companies amounted to an estimated $395 billion in 2012 according to SIPRI.
In 2004 over $30 billion were spent in the international arms-trade (a figure that excludes domestic sales of arms). According to SIPRI, the volume of international transfers of major weapons in 2010–14 was 16 percent higher than in 2005–2009. The five biggest exporters in 2010–2014 were the United States, Russia, China, Germany and France, and the five biggest importers were India, Saudi Arabia, China, the United Arab Emirates and Pakistan.
Many industrialized countries have a domestic arms-industry to supply their own military forces. Some countries also have a substantial legal or illegal domestic trade in weapons for use by their own citizens, primarily for self-defense, hunting or sporting purposes. Illegal trade in small arms occurs in many countries and regions affected by political instability.
The Small Arms Survey estimates that 875 million small arms circulate worldwide, produced by more than 1,000 companies from nearly 100 countries.
Governments award contracts to supply their country's military; such arms contracts can become of substantial political importance. The link between politics and the arms trade can result in the development of what U.S. President Dwight D. Eisenhower described in 1961 as a military-industrial complex (see above), where the armed forces, commerce, and politics become closely linked, similarly to the European multilateral defense procurement.
Various corporations, some publicly held, others private, bid for these contracts, which are often worth many billions of dollars. Sometimes, as with the contract for the international Joint Strike Fighter, a competitive tendering process takes place, with the decision made on the merits of the designs submitted by the companies involved. Other times, no bidding or competition takes place.
Click on any of the following blue hyperlinks for more about the Arms Race:
- History
- Sectors
- Cybersecurity industry
- International arms transfers
- World’s biggest postwar arms exporter
- List of major weapon manufacturers
- Arms control
- See also:
- Arms race
- Arms control
- Arms deal (disambiguation)
- Arms embargo
- Arms trafficking
- Cyber-arms industry
- Disarmament
- Guns versus butter model
- History of military technology
- List of chemical arms control agreements
- List of United States defense contractors
- List of most-produced firearms
- Military Keynesianism
- Naval conference (disambiguation)
- Nuclear disarmament
- Offset agreement
- Peace and conflict studies
- Peace dividend
- Permanent war economy
- Private military company
- Small Arms and Light Weapons (SALW)
- Small arms trade
- Torture trade
- United Nations Office for Disarmament Affairs
- Amnesty International: Arms Trade
- FAS's Arms Sales Monitoring Project
- The Guardian's arms trade report
- List of participators of the Defense System and Equipment international conference in London, 2003
- SIPRI arms industry reports and database
- SIPRI list of Top 100 arms-producing companies
- SPADE Defense Index (NYSE: DXS) Defense sector market index
- The True Cost of Global Arms Trade [infographic included]
- UN Office for Disarmament Affairs
- U.S. Arms Sales to the Third World from the Dean Peter Krogh Foreign Affairs Digital Archives
- World Map and Chart of Arms exports per country by Lebanese-economy-forum, World Bank data
- World Security Institute's Center for Defense Information
- Z. Yihdego, Arms Trade and International Law, Hart: OXford, 2007
- Heritage Weapon Factories in Spain
This is a list of the world's 50 largest arms manufacturers and other military service companies, along with their countries of origin. The information is based on a list published by the Stockholm International Peace Research Institute for 2018. The list provided by the SIPRI excludes companies based in China. The numbers are in billions of US dollars.
Click here for the list of 50 largest arms manufacturers.
See also:
- List of major arms industry corporations by country
- List of National Defense Industries
- Arms deals
- Arms control
- Arms embargo
- Arms trafficking
- Arms Trade Treaty
- Campaign Against Arms Trade
- Canadian Arms trade
- Disarmament
- Gun control
- Gun politics
- Guns versus butter theory
- IANSA
- List of chemical arms control agreements
- List of international environmental agreements
- Military funding of science
- Military Keynesianism
- MMRCA (Sale of 126–200 Fighter Aircraft for Indian Airforce)
- Naval conference (disambiguation), various conferences relating to arms control
- Nuclear disarmament
- Offset agreement
- Peace dividend
- Private military company
- Permanent arms economy
- SALW
- Small Arms Survey
- Small arms trade
- Torture trade
This article contains a list of countries by military expenditure in a given year. Military expenditure figures are presented in United States dollars based on either constant or current exchange rates.
Stockholm International Peace Research Institute (SIPRI) 2018 fact sheet:
The first list is based on the SIPRI fact sheet which includes a list of the world's top 15 military spenders in 2018, based on current market exchange rates.
The second list is based on the 2019 edition of "The Military Balance" published by the (IISS) using average market exchange rates.
Click here for a List of Countries by Military Expenditures
Spending based on GDP:
This first list is a list of countries by military expenditure share of GDP—more specifically, a list of the top 15 countries by percentage share in recent years—the amount spent by a nation on its military as a share of its GDP.
The second list presents this as a share of the general government expenditure.
The first list is sourced from the Stockholm International Peace Research Institute for the year 2017 and from Military Balance 2017 published by International Institute for Strategic Studies for the year 2016.
The second list is sourced only from the Stockholm International Peace Research Institute for the year 2017.
None of the following analyze such potential record-breakers like North Korea, Syria, Yemen, and Libya.
Military expenditure as a share of GDP
See Also:
- Arms industry
- Military budget
- List of countries by past military expenditure
- List of countries by military expenditure per capita
- List of countries by Global Militarization Index
- Military budget of the United States
- SIPRI military expenditure database (sipri.org)
Artificial Intelligence (AI) Arms Race
- YouTube Video: The Threat of AI Weapons
- YouTube Video: Russia Unveils New Tu-22M3M Artificial Intelligence Guided Long Range Bomber
- YouTube Video: Will China win the AI arms race?
- TOP (L) China is Building Artificial Intelligence-powered Nuclear Submarine that could have its own Thoughts (Newsweek 2/5/2018);
- TOP (R) AI in Military Drones and UAV's -- Current Applications
- BOTTOM (L): The U.S. Army is turning to Robot Soldiers (Bloomberg 5/18/2018;
- BOTTOM (R) AI Innovators Take Pledge Against Autonomous Killer Weapons (NPR 7/18/2018)
An artificial intelligence arms race is a competition between two or more states to have its military forces equipped with the best "artificial intelligence" (AI). Since the mid-2010s, many analysts have argued that a such a global arms race for better artificial intelligence has already begun.
Stances toward military artificial intelligence:
Russia:
Russian General Viktor Bondarev, commander-in-chief of the Russian air force, has stated that as early as February 2017, Russia has been working on AI-guided missiles that can decide to switch targets mid-flight. Reports by state-sponsored Russian media on potential military uses of AI increased in mid-2017.
In May 2017, the CEO of Russia's Kronstadt Group, a defense contractor, stated that "there already exist completely autonomous AI operation systems that provide the means for UAV clusters, when they fulfill missions autonomously, sharing tasks between them, and interact", and that it is inevitable that "swarms of drones" will one day fly over combat zones.
Russia has been testing several autonomous and semi-autonomous combat systems, such as Kalashnikov's "neural net" combat module, with a machine gun, a camera, and an AI that its makers claim can make its own targeting judgements without human intervention.
In September 2017, during a National Knowledge Day address to over a million students in 16,000 Russian schools, Russian President Vladimir Putin stated "Artificial intelligence is the future, not only for Russia but for all humankind... Whoever becomes the leader in this sphere will become the ruler of the world".
The Russian government has strongly rejected any ban on lethal autonomous weapons systems, suggesting that such a ban could be ignored.
China:
Further information: Artificial intelligence industry in China
According to a February 2019 report by Gregory C. Allen of the Center for a New American Security, "China’s leadership – including President Xi Jinping – believes that being at the forefront in AI technology is critical to the future of global military and economic power competition."
Chinese military officials have said that their goal is to incorporate commercial AI technology to "narrow the gap between the Chinese military and global advanced powers." The close ties between Silicon Valley and China, and the open nature of the American research community, has made the West's most advanced AI technology easily available to China; in addition, Chinese industry has numerous home-grown AI accomplishments of its own, such as Baidu passing a notable Chinese-language speech recognition capability benchmark in 2015.
As of 2017, Beijing's roadmap aims to create a $150 billion AI industry by 2030. Before 2013, Chinese defense procurement was mainly restricted to a few conglomerates; however, as of 2017, China often sources sensitive emerging technology such as drones and artificial intelligence from private start-up companies. One Chinese state has pledged to invest $5 billion in AI.
Beijing has committed $2 billion to an AI development park. The Japan Times reported in 2018 that annual private Chinese investment in AI is under $7 billion per year. AI startups in China received nearly half of total global investment in AI startups in 2017; the Chinese filed for nearly five times as many AI patents as did Americans.
China published a position paper in 2016 questioning the adequacy of existing international law to address the eventuality of fully autonomous weapons, becoming the first permanent member of the U.N. Security Council to broach the issue. In 2018, Xi called for greater international cooperation in basic AI research. Chinese officials have expressed concern that AI such as drones could lead to accidental war, especially in the absence of international norms.
United States:
In 2014, former Secretary of Defense Chuck Hagel posited the "Third Offset Strategy" that rapid advances in artificial intelligence will define the next generation of warfare.
According to data science and analytics firm Govini, The U.S. Department of Defense increased investment in artificial intelligence, big data and cloud computing from $5.6 billion in 2011 to $7.4 billion in 2016. However, the civilian NSF budget for AI saw no increase in 2017.
The U.S. has many military AI combat programs, such as the Sea Hunter autonomous warship, which is designed to operate for extended periods at sea without a single crew member, and to even guide itself in and out of port.
As of 2017, a temporary US Department of Defense directive requires a human operator to be kept in the loop when it comes to the taking of human life by autonomous weapons systems. Japan Times reported in 2018 that the United States private investment is around $70 billion per year.
United Kingdom:
In 2015, the UK government opposed a ban on lethal autonomous weapons, stating that "international humanitarian law already provides sufficient regulation for this area", but that all weapons employed by UK armed forces would be "under human oversight and control".
Israel:
Israel's Harpy anti-radar "fire and forget" drone is designed to be launched by ground troops, and autonomously fly over an area to find and destroy radar that fits pre-determined criteria.
South Korea:
The South Korean Super aEgis II machine gun, unveiled in 2010, sees use both in South Korea and in the Middle East. It can identify, track, and destroy a moving target at a range of 4 km. While the technology can theoretically operate without human intervention, in practice safeguards are installed to require manual input.
A South Korean manufacturer states, "Our weapons don't sleep, like humans must. They can see in the dark, like humans can't. Our technology therefore plugs the gaps in human capability", and they want to "get to a place where our software can discern whether a target is friend, foe, civilian or military".
Trends:
According to Siemens, worldwide military spending on robotics was 5.1 billion USD in 2010 and 7.5 billion USD in 2015.
China became a top player in artificial intelligence research in the 2010s. According to the Financial Times, in 2016, for the first time, China published more AI papers than the entire European Union.
When restricted to number of AI papers in the top 5% of cited papers, China overtook the United States in 2016 but lagged behind the European Union. 23% of the researchers presenting at the 2017 American Association for the Advancement of Artificial Intelligence (AAAI) conference were Chinese.
Eric Schmidt, the former chairman of Alphabet, has predicted China will be the leading country in AI by 2025.
Proposals for international regulation:
As early as 2007, scholars such as AI professor Noel Sharkey have warned of "an emerging arms race among the hi-tech nations to develop autonomous submarines, fighter jets, battleships and tanks that can find their own targets and apply violent force without the involvement of meaningful human decisions".
As early as 2014, AI specialists such as Steve Omohundro have been warning that "An autonomous weapons arms race is already taking place".
Miles Brundage of the University of Oxford has argued an AI arms race might be somewhat mitigated through diplomacy: "We saw in the various historical arms races that collaboration and dialog can pay dividends". Over a hundred experts signed an open letter in 2017 calling on the UN to address the issue of lethal autonomous weapons; however, at a November 2017 session of the UN Convention on Certain Conventional Weapons (CCW), diplomats could not agree even on how to define such weapons.
The Indian ambassador and chair of the CCW stated that agreement on rules remained a distant prospect. As of 2017, twenty-two countries have called for a full ban on lethal autonomous weapons.
Many experts believe attempts to completely ban killer robots are likely to fail. A 2017 report from Harvard's Belfer Center predicts that AI has the potential to be as transformative as nuclear weapons. The report further argues that "Preventing expanded military use of AI is likely impossible" and that "the more modest goal of safe and effective technology management must be pursued", such as banning the attaching of an AI dead man's switch to a nuclear arsenal.
Part of the impracticality is that detecting treaty violations would be extremely difficult.
Other reactions to autonomous weapons:
A 2015 open letter calling for the ban of lethal automated weapons systems has been signed by tens of thousands of citizens, including scholars such as physicist Stephen Hawking, Tesla magnate Elon Musk, and Apple's Steve Wozniak.
Professor Noel Sharkey of the University of Sheffield has warned that autonomous weapons will inevitably fall into the hands of terrorist groups such as the Islamic State.
Disassociation:
Many Western tech companies are leery of being associated too closely with the U.S. military, for fear of losing access to China's market. Furthermore, some researchers, such as DeepMind's Demis Hassabis, are ideologically opposed to contributing to military work.
For example, Project Maven is a Pentagon project involving using machine learning and engineering talent to distinguish people and objects in drone videos, established in a memo by the U.S. Deputy Secretary of Defense on 26 April 2017.
Also known as the Algorithmic Warfare Cross Functional Team, it is, according to Lt. Gen. of the United States Air Force Jack Shanahan in November 2017, a project "designed to be that pilot project, that pathfinder, that spark that kindles the flame front of artificial intelligence across the rest of the [Defense] Department". Its chief, U.S. Marine Corps Col. Drew Cukor, said: "People and computers will work symbiotically to increase the ability of weapon systems to detect objects."
At the second Defense One Tech Summit in July 2017, Cukor also said that the investment in a "deliberate workflow process" was funded by the Department [of Defense] through its "rapid acquisition authorities" for about "the next 36 months".
In June 2018, company sources at Google said that top executive Diane Greene told staff that the company would not follow-up Project Maven after the current contract expires in March 2019.
See also:
Stances toward military artificial intelligence:
Russia:
Russian General Viktor Bondarev, commander-in-chief of the Russian air force, has stated that as early as February 2017, Russia has been working on AI-guided missiles that can decide to switch targets mid-flight. Reports by state-sponsored Russian media on potential military uses of AI increased in mid-2017.
In May 2017, the CEO of Russia's Kronstadt Group, a defense contractor, stated that "there already exist completely autonomous AI operation systems that provide the means for UAV clusters, when they fulfill missions autonomously, sharing tasks between them, and interact", and that it is inevitable that "swarms of drones" will one day fly over combat zones.
Russia has been testing several autonomous and semi-autonomous combat systems, such as Kalashnikov's "neural net" combat module, with a machine gun, a camera, and an AI that its makers claim can make its own targeting judgements without human intervention.
In September 2017, during a National Knowledge Day address to over a million students in 16,000 Russian schools, Russian President Vladimir Putin stated "Artificial intelligence is the future, not only for Russia but for all humankind... Whoever becomes the leader in this sphere will become the ruler of the world".
The Russian government has strongly rejected any ban on lethal autonomous weapons systems, suggesting that such a ban could be ignored.
China:
Further information: Artificial intelligence industry in China
According to a February 2019 report by Gregory C. Allen of the Center for a New American Security, "China’s leadership – including President Xi Jinping – believes that being at the forefront in AI technology is critical to the future of global military and economic power competition."
Chinese military officials have said that their goal is to incorporate commercial AI technology to "narrow the gap between the Chinese military and global advanced powers." The close ties between Silicon Valley and China, and the open nature of the American research community, has made the West's most advanced AI technology easily available to China; in addition, Chinese industry has numerous home-grown AI accomplishments of its own, such as Baidu passing a notable Chinese-language speech recognition capability benchmark in 2015.
As of 2017, Beijing's roadmap aims to create a $150 billion AI industry by 2030. Before 2013, Chinese defense procurement was mainly restricted to a few conglomerates; however, as of 2017, China often sources sensitive emerging technology such as drones and artificial intelligence from private start-up companies. One Chinese state has pledged to invest $5 billion in AI.
Beijing has committed $2 billion to an AI development park. The Japan Times reported in 2018 that annual private Chinese investment in AI is under $7 billion per year. AI startups in China received nearly half of total global investment in AI startups in 2017; the Chinese filed for nearly five times as many AI patents as did Americans.
China published a position paper in 2016 questioning the adequacy of existing international law to address the eventuality of fully autonomous weapons, becoming the first permanent member of the U.N. Security Council to broach the issue. In 2018, Xi called for greater international cooperation in basic AI research. Chinese officials have expressed concern that AI such as drones could lead to accidental war, especially in the absence of international norms.
United States:
In 2014, former Secretary of Defense Chuck Hagel posited the "Third Offset Strategy" that rapid advances in artificial intelligence will define the next generation of warfare.
According to data science and analytics firm Govini, The U.S. Department of Defense increased investment in artificial intelligence, big data and cloud computing from $5.6 billion in 2011 to $7.4 billion in 2016. However, the civilian NSF budget for AI saw no increase in 2017.
The U.S. has many military AI combat programs, such as the Sea Hunter autonomous warship, which is designed to operate for extended periods at sea without a single crew member, and to even guide itself in and out of port.
As of 2017, a temporary US Department of Defense directive requires a human operator to be kept in the loop when it comes to the taking of human life by autonomous weapons systems. Japan Times reported in 2018 that the United States private investment is around $70 billion per year.
United Kingdom:
In 2015, the UK government opposed a ban on lethal autonomous weapons, stating that "international humanitarian law already provides sufficient regulation for this area", but that all weapons employed by UK armed forces would be "under human oversight and control".
Israel:
Israel's Harpy anti-radar "fire and forget" drone is designed to be launched by ground troops, and autonomously fly over an area to find and destroy radar that fits pre-determined criteria.
South Korea:
The South Korean Super aEgis II machine gun, unveiled in 2010, sees use both in South Korea and in the Middle East. It can identify, track, and destroy a moving target at a range of 4 km. While the technology can theoretically operate without human intervention, in practice safeguards are installed to require manual input.
A South Korean manufacturer states, "Our weapons don't sleep, like humans must. They can see in the dark, like humans can't. Our technology therefore plugs the gaps in human capability", and they want to "get to a place where our software can discern whether a target is friend, foe, civilian or military".
Trends:
According to Siemens, worldwide military spending on robotics was 5.1 billion USD in 2010 and 7.5 billion USD in 2015.
China became a top player in artificial intelligence research in the 2010s. According to the Financial Times, in 2016, for the first time, China published more AI papers than the entire European Union.
When restricted to number of AI papers in the top 5% of cited papers, China overtook the United States in 2016 but lagged behind the European Union. 23% of the researchers presenting at the 2017 American Association for the Advancement of Artificial Intelligence (AAAI) conference were Chinese.
Eric Schmidt, the former chairman of Alphabet, has predicted China will be the leading country in AI by 2025.
Proposals for international regulation:
As early as 2007, scholars such as AI professor Noel Sharkey have warned of "an emerging arms race among the hi-tech nations to develop autonomous submarines, fighter jets, battleships and tanks that can find their own targets and apply violent force without the involvement of meaningful human decisions".
As early as 2014, AI specialists such as Steve Omohundro have been warning that "An autonomous weapons arms race is already taking place".
Miles Brundage of the University of Oxford has argued an AI arms race might be somewhat mitigated through diplomacy: "We saw in the various historical arms races that collaboration and dialog can pay dividends". Over a hundred experts signed an open letter in 2017 calling on the UN to address the issue of lethal autonomous weapons; however, at a November 2017 session of the UN Convention on Certain Conventional Weapons (CCW), diplomats could not agree even on how to define such weapons.
The Indian ambassador and chair of the CCW stated that agreement on rules remained a distant prospect. As of 2017, twenty-two countries have called for a full ban on lethal autonomous weapons.
Many experts believe attempts to completely ban killer robots are likely to fail. A 2017 report from Harvard's Belfer Center predicts that AI has the potential to be as transformative as nuclear weapons. The report further argues that "Preventing expanded military use of AI is likely impossible" and that "the more modest goal of safe and effective technology management must be pursued", such as banning the attaching of an AI dead man's switch to a nuclear arsenal.
Part of the impracticality is that detecting treaty violations would be extremely difficult.
Other reactions to autonomous weapons:
A 2015 open letter calling for the ban of lethal automated weapons systems has been signed by tens of thousands of citizens, including scholars such as physicist Stephen Hawking, Tesla magnate Elon Musk, and Apple's Steve Wozniak.
Professor Noel Sharkey of the University of Sheffield has warned that autonomous weapons will inevitably fall into the hands of terrorist groups such as the Islamic State.
Disassociation:
Many Western tech companies are leery of being associated too closely with the U.S. military, for fear of losing access to China's market. Furthermore, some researchers, such as DeepMind's Demis Hassabis, are ideologically opposed to contributing to military work.
For example, Project Maven is a Pentagon project involving using machine learning and engineering talent to distinguish people and objects in drone videos, established in a memo by the U.S. Deputy Secretary of Defense on 26 April 2017.
Also known as the Algorithmic Warfare Cross Functional Team, it is, according to Lt. Gen. of the United States Air Force Jack Shanahan in November 2017, a project "designed to be that pilot project, that pathfinder, that spark that kindles the flame front of artificial intelligence across the rest of the [Defense] Department". Its chief, U.S. Marine Corps Col. Drew Cukor, said: "People and computers will work symbiotically to increase the ability of weapon systems to detect objects."
At the second Defense One Tech Summit in July 2017, Cukor also said that the investment in a "deliberate workflow process" was funded by the Department [of Defense] through its "rapid acquisition authorities" for about "the next 36 months".
In June 2018, company sources at Google said that top executive Diane Greene told staff that the company would not follow-up Project Maven after the current contract expires in March 2019.
See also:
- Arms race
- Artificial intelligence
- Artificial general intelligence
- Ethics of artificial intelligence
- Existential risk from artificial general intelligence
- Global issue
- Lethal autonomous weapon
Vietnam War (1955-1975)
Clockwise, from top left: U.S. combat operations in Ia Đrăng, ARVN Rangers defending Saigon during the 1968 Tết Offensive, two A-4C Skyhawks after the Gulf of Tonkin incident, ARVN recapture Quảng Trị during the 1972 Easter Offensive, civilians fleeing the 1972 Battle of Quảng Trị, and burial of 300 victims of the 1968 Huế Massacre.
- YouTube Video: Vietnam War, 1970: CBS camera rolls as platoon comes under fire
- YouTube Video: The Fall of Saigon
- YouTube Video: 1968: The Tet Offensive
Clockwise, from top left: U.S. combat operations in Ia Đrăng, ARVN Rangers defending Saigon during the 1968 Tết Offensive, two A-4C Skyhawks after the Gulf of Tonkin incident, ARVN recapture Quảng Trị during the 1972 Easter Offensive, civilians fleeing the 1972 Battle of Quảng Trị, and burial of 300 victims of the 1968 Huế Massacre.
The Vietnam War (Vietnamese: Chiến tranh Việt Nam), also known as the Second Indochina War, and in Vietnam as the Resistance War Against America (Vietnamese: Kháng chiến chống Mỹ) or simply the American War, was a conflict in Vietnam, Laos, and Cambodia from 1 November 1955 to the fall of Saigon on 30 April 1975.
It was the second of the Indochina Wars and was officially fought between North Vietnam and South Vietnam.
North Vietnam was supported by the Soviet Union, China, and other communist allies;
South Vietnam was supported by the United States, South Korea, the Philippines, Australia, Thailand and other anti-communist allies.
The war, considered a Cold War-era proxy war by some, lasted 19 years, with direct U.S. involvement ending in 1973, and included the Laotian Civil War and the Cambodian Civil War, which ended with all three countries becoming communist in 1975.
The conflict emerged from the First Indochina War against the communist-led Viet Minh. Most of the funding for the French war effort was provided by the U.S.
After the French quit Indochina in 1954, the US assumed financial and military support for the South Vietnamese state. The Việt Cộng, also known as Front national de libération du Sud-Viêt Nam or NLF (the National Liberation Front), a South Vietnamese common front under the direction of North Vietnam, initiated a guerrilla war in the south.
North Vietnam had also invaded Laos in the mid-1950s in support of insurgents, establishing the Ho Chi Minh Trail to supply and reinforce the Việt Cộng.16 U.S. involvement escalated under President John F. Kennedy through the MAAG program from just under a thousand military advisors in 1959 to 16,000 in 1963.
By 1963, the North Vietnamese had sent 40,000 soldiers to fight in South Vietnam. North Vietnam was heavily backed by the USSR and the People's Republic of China. China also sent hundreds of PLA servicemen to North Vietnam to serve in air-defense and support roles.
By 1964, there were 23,000 US advisors in South Vietnam. In August, the Gulf of Tonkin incident occurred, in which a U.S. destroyer was alleged to have clashed with North Vietnamese fast attack craft. In response, the U.S Congress passed the Gulf of Tonkin Resolution, giving President Lyndon B. Johnson broad authorization to increase U.S. military presence. He ordered the deployment of combat units for the first time and increased troop levels to 184,000.
Past this point, the People's Army of Vietnam (PAVN) (also known as the North Vietnamese Army or NVA) engaged in more conventional warfare with U.S and South Vietnamese forces.
Every year onward, there was significant build-up of U.S forces, despite little progress. U.S Secretary of Defense Robert McNamara, one of the principal architects of the war, began expressing doubts of victory by the end of 1966.
U.S. and South Vietnam forces relied on air superiority and overwhelming firepower to conduct search and destroy operations, involving ground forces, artillery, and airstrikes. The U.S. also conducted a large-scale strategic bombing campaign against North Vietnam and Laos.
The Tet Offensive of 1968 showed the lack of progress with these doctrines. With the VC and PAVN mounting large-scale urban offensives throughout 1968, U.S domestic support for the war began fading. The Army of the Republic of Vietnam (ARVN) expanded following a period of neglect after Tet and was modeled after U.S doctrine.
The VC sustained heavy losses during the Tet Offensive and subsequent U.S.-ARVN operations in the rest of 1968, losing over 50,000 men. The CIA's Phoenix Program further degraded the VC's membership and capabilities.
By the end of the year, the VC insurgents held almost no territory in South Vietnam, and their recruitment dropped by over 80% in 1969, signifying a drastic reduction in guerrilla operations, necessitating increased use of PAVN regular soldiers from the north.
In 1969, North Vietnam declared a Provisional Revolutionary Government in South Vietnam in an attempt to give the reduced VC a more international stature, but the southern guerrillas from then on were sidelined as PAVN forces began more conventional Combined arms warfare.
Operations crossed national borders: Laos was invaded by North Vietnam early on, while Cambodia was used by North Vietnam as a supply route starting in 1967; the route through Cambodia began to be bombed by the U.S. in 1969, while the Laos route had been heavily bombed since 1964.
The deposing of the monarch Norodom Sihanouk by the Cambodian National Assembly resulted in a PAVN invasion of the country at the request of the Khmer Rouge, escalating the Cambodian Civil War and resulting in a U.S.-RVN counter-invasion.
In 1969, following the election of U.S President Richard Nixon, a policy of "Vietnamization" began, which saw the conflict fought by an expanded ARVN, with U.S. forces sidelined and increasingly demoralized by domestic opposition and reduced recruitment. U.S. ground forces had largely withdrawn by early 1972 and support was limited to air support, artillery support, advisers, and materiel shipments.
The ARVN, buttressed by said U.S. support, stopped the largest and first mechanized PAVN offensive to date during the Easter Offensive of 1972.The offensive resulted in heavy casualties on both sides and the failure of the PAVN to subdue South Vietnam, but the ARVN itself failed to recapture all territory, leaving its military situation difficult.
The Paris Peace Accords of January 1973 saw all U.S forces withdrawn; the Case–Church Amendment, passed by the U.S Congress on 15 August 1973, officially ended direct U.S military involvement. The Peace Accords were broken almost immediately, and fighting continued for two more years.
Phnom Penh fell to the Khmer Rouge on 17 April 1975 while the 1975 Spring Offensive saw the capture of Saigon by the PAVN on 30 April; this marked the end of the war, and North and South Vietnam were reunified the following year.
The scale of fighting was enormous: by 1970 the ARVN was the world's fourth largest army, with the PAVN being similar in size at around a million regular soldiers. The war exacted a huge human cost in terms of fatalities (see Vietnam War casualties): estimates of the number of Vietnamese soldiers and civilians killed vary from 966,000 to 3.8 million.
Some 275,000–310,000 Cambodians, 20,000–62,000 Laotians, and 58,220 U.S. service members also died in the conflict, and a further 1,626 remain missing in action.
The Sino-Soviet split re-emerged following the lull during the Vietnam War. Conflict between North Vietnam and its Cambodian allies in the Royal Government of the National Union of Kampuchea, and the newly-formed Democratic Kampuchea began almost immediately in a series of border raids by the Khmer Rouge, eventually escalating into the Cambodian–Vietnamese War.
Chinese forces directly invaded Vietnam in the Sino-Vietnamese War, with subsequent border conflicts lasting until 1991. Insurgencies were fought by the unified Vietnam in all three countries.
The end of the war and resumption of the Third Indochina War would precipitate the Vietnamese boat people and the larger Indochina refugee crisis, which saw millions of refugees leave Indochina (mainly southern Vietnam), with an estimated 250,000 of whom perished at sea.
Within the U.S, the war gave rise to what was referred to as Vietnam Syndrome, a public aversion to American overseas military involvements, which together with the Watergate scandal contributed to the crisis of confidence that affected America throughout the 1970s.
Names:
Further information: Terminology of the Vietnam War
Various names have been applied to the conflict. Vietnam War is the most commonly used name in English. It has also been called the Second Indochina War and the Vietnam Conflict.
Given that there have been several conflicts in Indochina, this particular conflict is known by the names of its primary protagonists, in order to distinguish it from others.
In Vietnamese, the war is generally known as Kháng chiến chống Mỹ (Resistance War Against America), but less formally as 'Cuộc chiến tranh Mỹ' (The American War). It is also called Chiến tranh Việt Nam (The Vietnam War).
Click on any of the following blue hyperlinks for more about the Vietnam War:
It was the second of the Indochina Wars and was officially fought between North Vietnam and South Vietnam.
North Vietnam was supported by the Soviet Union, China, and other communist allies;
South Vietnam was supported by the United States, South Korea, the Philippines, Australia, Thailand and other anti-communist allies.
The war, considered a Cold War-era proxy war by some, lasted 19 years, with direct U.S. involvement ending in 1973, and included the Laotian Civil War and the Cambodian Civil War, which ended with all three countries becoming communist in 1975.
The conflict emerged from the First Indochina War against the communist-led Viet Minh. Most of the funding for the French war effort was provided by the U.S.
After the French quit Indochina in 1954, the US assumed financial and military support for the South Vietnamese state. The Việt Cộng, also known as Front national de libération du Sud-Viêt Nam or NLF (the National Liberation Front), a South Vietnamese common front under the direction of North Vietnam, initiated a guerrilla war in the south.
North Vietnam had also invaded Laos in the mid-1950s in support of insurgents, establishing the Ho Chi Minh Trail to supply and reinforce the Việt Cộng.16 U.S. involvement escalated under President John F. Kennedy through the MAAG program from just under a thousand military advisors in 1959 to 16,000 in 1963.
By 1963, the North Vietnamese had sent 40,000 soldiers to fight in South Vietnam. North Vietnam was heavily backed by the USSR and the People's Republic of China. China also sent hundreds of PLA servicemen to North Vietnam to serve in air-defense and support roles.
By 1964, there were 23,000 US advisors in South Vietnam. In August, the Gulf of Tonkin incident occurred, in which a U.S. destroyer was alleged to have clashed with North Vietnamese fast attack craft. In response, the U.S Congress passed the Gulf of Tonkin Resolution, giving President Lyndon B. Johnson broad authorization to increase U.S. military presence. He ordered the deployment of combat units for the first time and increased troop levels to 184,000.
Past this point, the People's Army of Vietnam (PAVN) (also known as the North Vietnamese Army or NVA) engaged in more conventional warfare with U.S and South Vietnamese forces.
Every year onward, there was significant build-up of U.S forces, despite little progress. U.S Secretary of Defense Robert McNamara, one of the principal architects of the war, began expressing doubts of victory by the end of 1966.
U.S. and South Vietnam forces relied on air superiority and overwhelming firepower to conduct search and destroy operations, involving ground forces, artillery, and airstrikes. The U.S. also conducted a large-scale strategic bombing campaign against North Vietnam and Laos.
The Tet Offensive of 1968 showed the lack of progress with these doctrines. With the VC and PAVN mounting large-scale urban offensives throughout 1968, U.S domestic support for the war began fading. The Army of the Republic of Vietnam (ARVN) expanded following a period of neglect after Tet and was modeled after U.S doctrine.
The VC sustained heavy losses during the Tet Offensive and subsequent U.S.-ARVN operations in the rest of 1968, losing over 50,000 men. The CIA's Phoenix Program further degraded the VC's membership and capabilities.
By the end of the year, the VC insurgents held almost no territory in South Vietnam, and their recruitment dropped by over 80% in 1969, signifying a drastic reduction in guerrilla operations, necessitating increased use of PAVN regular soldiers from the north.
In 1969, North Vietnam declared a Provisional Revolutionary Government in South Vietnam in an attempt to give the reduced VC a more international stature, but the southern guerrillas from then on were sidelined as PAVN forces began more conventional Combined arms warfare.
Operations crossed national borders: Laos was invaded by North Vietnam early on, while Cambodia was used by North Vietnam as a supply route starting in 1967; the route through Cambodia began to be bombed by the U.S. in 1969, while the Laos route had been heavily bombed since 1964.
The deposing of the monarch Norodom Sihanouk by the Cambodian National Assembly resulted in a PAVN invasion of the country at the request of the Khmer Rouge, escalating the Cambodian Civil War and resulting in a U.S.-RVN counter-invasion.
In 1969, following the election of U.S President Richard Nixon, a policy of "Vietnamization" began, which saw the conflict fought by an expanded ARVN, with U.S. forces sidelined and increasingly demoralized by domestic opposition and reduced recruitment. U.S. ground forces had largely withdrawn by early 1972 and support was limited to air support, artillery support, advisers, and materiel shipments.
The ARVN, buttressed by said U.S. support, stopped the largest and first mechanized PAVN offensive to date during the Easter Offensive of 1972.The offensive resulted in heavy casualties on both sides and the failure of the PAVN to subdue South Vietnam, but the ARVN itself failed to recapture all territory, leaving its military situation difficult.
The Paris Peace Accords of January 1973 saw all U.S forces withdrawn; the Case–Church Amendment, passed by the U.S Congress on 15 August 1973, officially ended direct U.S military involvement. The Peace Accords were broken almost immediately, and fighting continued for two more years.
Phnom Penh fell to the Khmer Rouge on 17 April 1975 while the 1975 Spring Offensive saw the capture of Saigon by the PAVN on 30 April; this marked the end of the war, and North and South Vietnam were reunified the following year.
The scale of fighting was enormous: by 1970 the ARVN was the world's fourth largest army, with the PAVN being similar in size at around a million regular soldiers. The war exacted a huge human cost in terms of fatalities (see Vietnam War casualties): estimates of the number of Vietnamese soldiers and civilians killed vary from 966,000 to 3.8 million.
Some 275,000–310,000 Cambodians, 20,000–62,000 Laotians, and 58,220 U.S. service members also died in the conflict, and a further 1,626 remain missing in action.
The Sino-Soviet split re-emerged following the lull during the Vietnam War. Conflict between North Vietnam and its Cambodian allies in the Royal Government of the National Union of Kampuchea, and the newly-formed Democratic Kampuchea began almost immediately in a series of border raids by the Khmer Rouge, eventually escalating into the Cambodian–Vietnamese War.
Chinese forces directly invaded Vietnam in the Sino-Vietnamese War, with subsequent border conflicts lasting until 1991. Insurgencies were fought by the unified Vietnam in all three countries.
The end of the war and resumption of the Third Indochina War would precipitate the Vietnamese boat people and the larger Indochina refugee crisis, which saw millions of refugees leave Indochina (mainly southern Vietnam), with an estimated 250,000 of whom perished at sea.
Within the U.S, the war gave rise to what was referred to as Vietnam Syndrome, a public aversion to American overseas military involvements, which together with the Watergate scandal contributed to the crisis of confidence that affected America throughout the 1970s.
Names:
Further information: Terminology of the Vietnam War
Various names have been applied to the conflict. Vietnam War is the most commonly used name in English. It has also been called the Second Indochina War and the Vietnam Conflict.
Given that there have been several conflicts in Indochina, this particular conflict is known by the names of its primary protagonists, in order to distinguish it from others.
In Vietnamese, the war is generally known as Kháng chiến chống Mỹ (Resistance War Against America), but less formally as 'Cuộc chiến tranh Mỹ' (The American War). It is also called Chiến tranh Việt Nam (The Vietnam War).
Click on any of the following blue hyperlinks for more about the Vietnam War:
- Background
- Transition period
- Diệm era, 1954–1963
- Kennedy's escalation, 1961–1963
- Johnson's escalation, 1963–1969
- Vietnamization, 1969–1972
- U.S. exit and final campaigns, 1973–1975
- Opposition to U.S. involvement, 1964–1973
- Involvement of other countries
- United Front for the Liberation of Oppressed Races (FULRO)
- War crimes
- Women
- Black servicemen
- Weapons
- Aftermath
- See also:
- History of Cambodia
- History of Laos
- History of Vietnam
- List of conflicts in Asia
- Opposition to United States involvement in the Vietnam War
- U.S. news media and the Vietnam War
- The Vietnam War (TV series)
- A Vietnam Diary's Homecoming Video produced by the PBS Series History Detectives
- Detailed bibliography of Vietnam War
- Documents Relating to American Foreign Policy–Vietnam primary sources on U.S. involvement
- Fallout of the War from the Dean Peter Krogh Foreign Affairs Digital Archives
- Glossary of Military Terms & Slang from the Vietnam War
- Impressions of Vietnam and descriptions of the daily life of a soldier from the oral history of Elliott Gardner, U.S. Army
- Stephen H. Warner Southeast Asia Photograph Collection at Gettysburg College
- Timeline US – Vietnam (1947–2001) in Open-Content project
- The U.S. Army in Vietnam the official history of the United States Army
- The Vietnam War at The History Channel
- UC Berkeley Library Social Activism Sound Recording Project: Anti-Vietnam War Protests
- Vietnam war timeline comprehensive timeline of the Vietnam War
- Virtual Vietnam Archive – Texas Tech University
- 1965–1975 Another Vietnam; Unseen images of the war from the winning side – Mashable
- Archival collections about the Vietnam War, University Archives and Special Collections, Joseph P. Healey Library, University of Massachusetts Boston